Verizon and Google Are Love Birds? Their Call Is 5G 5G 5G
December 22, 2021
The folks involved with electronic equipment for air planes are expressing some concerns about 5G. Why? Potential issues related to interference. See the FAA and others care about passengers and air freight. Now Verizon and Google care about each other and are moving forward with more 5G goodness. (Please, turn off those 5G mobiles.)
Verizon is regarded as the top mobile provider in the United States. Verizon earns that title, because the company is always innovating. Tech Radar has the story on one of Verizon’s newest innovations: “Verizon Partners With Google Cloud On 5G Edge.” Google Cloud and Verizon will pool their resources to offer 5G mobile edge with guaranteed performance for enterprise customers.
Verizon is promising its 5G networks will have lower latency with faster speeds, reliable connections, and greater capacity. The mobile provider will deliver on its 5G and lower latency promise by decentralizing infrastructures and virtualizing networks, so they are closer to customers. Edge computing means data is processed closer to its collection point. This will enable more advanced technology to take root: smart city applications, telemedicine, and virtual reality.
Google Cloud’s storage and compute capabilities are what Verizon needs to deliver 5G:
“The partnership will initially combine Verizon’s private on-site 5G and its private 5G edge services with Google Distributed Cloud Edge, but the two companies have said they plan to develop capabilities for public networks that will allow enterprises to deploy applications across the US.”
Verizon’s new Google partnership makes it the first mobile provider to offer edge services with Amazon Web Services, Google Cloud, and Microsoft Azure.
The advancement of 5G will transform developed countries into automated science-fiction dreams. Verizon 5G edge sounds like it requires the use of more user data in order for it to be processed closer to the collection point. Is this why Verizon has been capturing more of late? Will 5G networks require more private user data to function?
One of my colleagues at Beyond Search had the silly idea that the Verizon Google discussions contributed to Verizon’s keen interest in capturing more customer data. Will the cooing of 5G 5G 5G soothe those worried about having a 757 visit the apartments adjacent O’Hare Airport? Of course not. Verizon and Google are incapable of making technical missteps.
Whitney Grace, December 22, 2021
Google and Its Penchant for Bold Assertions
December 17, 2021
Google claimed quantum supremacy. Recently Google’s engineers studied the technology of the NSO Group and according to “A Deep Dive into an NSO Zero-Click iMessage Exploit: Remote Code Execution” found the “most technically sophisticated exploit ever seen.” The analysis is thorough and reflects considerable enthusiasm for disentangling some of the inner workings of Apple’s mobile operating system. I can almost hear the chuckles of the Google engineers as they figured out how the NSO Group compromised iPhones simply by sending the unlucky target a message packet.
Several observations:
- The NSO Group talks with other entities (people from university, a military unit, colleagues at limited attendance conference, etc.). Consequently information about methods seeps into the intelware community. This community is not quite like the Yacht Club in Manhattan, but it is similar: Traditions, friendships, bon homie, and the like.
- Intelware developers associated with other countries often gain access to specialized tools and services via connections with a nation state which is a customer of an specialized services firm, say, for argument’s sake, the NSO Group. It is probable that other entities have examined and replicated some of the NSO Group’s systems and methods. The fact that Google figured out the system and methods of this particular NSO Group service means that other groups can too. (It is possible that some at Google believe that their work is singular and not replicable. Yeah, high school science club thinking, perhaps?)
- Due to the connection between high value targets and the cachet of the Apple iPhone, figuring out how to penetrate an iPhone is a high value activity. Apple’s engineers are bright and were in their high school science clubs as well. However, engineers do not design to prevent unforeseeable flaws in their engineering innovations. This means that iPhones have flaws. When a device is the focus of attention of numerous nation states’ intelligence services, commercial enterprises in the zero day business, and companies with staff trained by military intelligence organizations — flaws will be found. My Arnold Rule for this situation is that insights will be discovered of which the original developer had no clue.
Kudos to Google for the NSO Group information. However, like quantum supremacy, the statements about the sophistication of the exploit are a bit like the claim for quantum supremacy. There are other entities in the Intel world which have capabilities which will surprise the “experts” just now discovering the world of intelware. Nice paper, very academic, but it reveals a disconnect between the world of the commercial researcher and the robust, broad intelware ecosystem.
Stephen E Arnold, December 17, 2021
Chinese Company Excitement: Xiaomi
December 15, 2021
Own stock in Alibaba? Well, think Xiaomi.
Lithuania made a discovery during a recent cybersecurity assessment that, honestly, does not surprise us in the least. We learn of the finding in Big Technology’s piece, “A Xiaomi Phone Might’ve Shipped With a Censorship List in Europe. Now What?” A certain Xiaomi phone model sold in Europe was found to carry a built-in censorship list of about 450 political terms, like “democratic movement” and “long live Taiwan’s independence.” The blocklist lay dormant, but it could have been activated remotely at any time. It is thought its inclusion on phones shipped outside China, where censorship is the norm, may have been a mistake. Reporter Alex Kantrowitz writes:
“After the government published its findings, things got weird. The list swelled to more than 1,000 terms, including hundreds of non-political terms like ‘pornography,’ seemingly to turn the political blocklist into something more generic. Then, it disappeared. ‘They reacted,’ Margiris Abukevicius, Lithuania’s vice minister for defense, told me. ‘It wasn’t publicized from their side.’ The accusations, which Xiaomi disputes, clarified just how fraught the West’s relationship is with China’s growing technology power. As China-based tech companies like Xiaomi and TikTok flourish, there’s still no playbook in North America or Europe to deal with their potential to censor or steer culture via algorithms. TikTok, with its inscrutable feed, remains unchecked. And the Lithuanian government’s report on Xiaomi, replicated by another researcher, sparked a collective shrug. ‘Western countries,’ Abukevicius said, ‘are more and more reliant on technologies, and a big part of those technologies comes from countries which are not friendly, which we don’t trust, and it poses risks.’ How to address those risks remains unclear, though. Xiaomi was Europe’s top-selling smartphone manufacturer in the second quarter of 2021, and it’s number two in the world overall.”
Not in the US, though. Xiaomi was blacklisted here until recently, and FCC commissioner Brendan Carr is taking Lithuania’s discovery into account as he decides whether to allow Xiaomi smartphones to run on our wireless networks. In Europe, more countries are investigating the matter. It is uncertain what measures will be taken; an outright ban seems “extreme,” we’re told, considering there is no evidence the blocklist was ever activated within the EU. Kantrowitz points out the bigger issue going forward is a more general one—Western nations need a plan to address the culture clash and potential security risks cropping up on our devices.
Cynthia Murrell, December xx, 2021
No Click Excitement: Interaction-Less Vulnerabilities in Messaging Apps
October 20, 2021
Google researcher Natalie Silvanovich has made it her mission to investigate one particular type of vulnerability—one that allows attackers to access video and/or audio without the victim so much as clicking a link. Wired discusses her unnerving findings in, “Messaging Apps Have an Eavesdropping Problem.” Writer Lily Hay Newman tells us:
“Silvanovich has spent years studying “interaction-less” vulnerabilities, hacks that don’t require their targets to click a malicious link, download an attachment, enter a password in the wrong place, or participate in any way. Those attacks have taken on increasing significance as targeted mobile surveillance explodes around the world.”
The resolute researcher presented her findings at the recent Black Hat security conference in Las Vegas. Her search turned up bugs in apps domestic and foreign, from Facebook Messenger, Google Duo, and Signal to JioChat and Viettel Mocha. The vulnerabilities she found were eagerly patched by the respective developers once she notified them, but her discoveries reveal a problem more widespread than had been suspected. It seems that some of the vulnerabilities resulted from honest mistakes by developers using the open source communication tool WebRTC. Other times, though, it had to do with how an app connects calls. We learn:
“When someone calls you on an internet-based communication app, the system can start setting up the connection between your devices right away, a process known as ‘establishment,’ so the call can start instantly when you hit accept. Another option is for the app to hang back a bit, wait to see if you accept the call, and then take a couple of seconds to establish the communication channel once it knows your preference. … Most mainstream services take the other route, though, setting up the communication channel and even starting to send data like audio and video streams in advance to offer a near-instantaneous connection should the call’s recipient pick up. Doing that prep work doesn’t inherently introduce vulnerabilities, and it can be done in a privacy-preserving way. But it does create more opportunities for mistakes.”
Concerned users may want to favor Telegram—Silvanovich found that app takes the slower but safer route. Though the snippets hackers can capture with these vulnerabilities may or may not be valuable, many find it worth a try—such attacks are difficult to detect and to trace. Careful design and implementation on the part of app developers are the keys to avoiding such breaches, she tells us.
Cynthia Murrell October 20, 2021
Data Slupring Gluttons: Guess Who, Please?
October 19, 2021
Apple’s iOS enjoys a reputation of being more respectful of users’ privacy than Google’s Android. However, announces Tom’s Guide, “New Study Reveals iPhones Aren’t as Private as You Think.” The recent paper was published by Trinity College’s School of Computer Science & Statistics. Unlike the many studies that have covered what kind of data apps collect, this research focusses on data reaped by core operating systems.
The researchers found Android does collect a higher volume of data, but iPhones collect more types of information. This includes data about other devices that could allow Apple to make a relationship graph of all devices in a local network, whether a home, office, or public space like a café. Creepy. Not only that, both operating systems collect telemetry and other data even when users explicitly opt out. Much of this collection happens when the phone is powered up. The rest occurs the whole time the device is on, even when sitting idle. Writer Paul Wegenseil specifies:
“Both the iPhone and Android phone called home to Apple and Google servers every 4 or 5 minutes while the phones were left idle and unused for several days. The phones were powered on and plugged in, but the users had not yet logged into Apple or Google accounts. Even when the iPhone user stayed logged out of their Apple account, the iPhone still sent identifying cookies to iCloud, Siri, the iTunes Store and Apple’s analytics servers while the iPhone was idle. It also sent information about nearby devices sharing the same Wi-Fi network. When location services were enabled on the iPhone, its latitude and longitude were transmitted to Apple servers. On Android, data is sent to Google Play servers every 10 to 20 minutes even when the user is not logged in. Certain Google apps also send data, including Chrome, Docs, Messaging, Search and YouTube, although only YouTube sends unique device identifiers. Even when the iPhone user stayed logged out of their Apple account, the iPhone still sent identifying cookies to iCloud, Siri, the iTunes Store and Apple’s analytics servers while the iPhone was idle. It also sent information about nearby devices sharing the same Wi-Fi network.”
Unfortunately, researchers concluded, there is not much one can do to prevent this data from being harvested. The best Android users can do is to start their phone with network connections disabled. The study found disabling Google Play Services and the Google Play and YouTube apps before connecting to a network prevented the vast majority of data sharing. But then, users would have to visit other app stores to download apps, each of which has its own privacy issues. Apple users do not even have that option, as their device must connect to a network to activate.
See the article for a summary of the researchers’ process. They reached out to both companies for comment. Google responded by comparing its data collection to the statistics modern vehicles send back to manufacturers—they just want to make sure everything is working properly. Apple’s spokesperson quibbled with the researchers findings and insisted users’ personal data was safe and could not be traced to individuals. I suppose we will just have to take their word for it.
Cynthia Murrell October 19, 2021
NSO Group and an Alert Former French Diplomat: Observation Is Often Helpful
August 2, 2021
I read “French Ex-Diplomat Saw Potential for Misuse While Working at NSO.” The allegedly accurate write up reports that Gerard Araud [once a French ambassador] took a position at NSO Group. The write up adds:
His one-year mission from September 2019, along with two other external consultants from the United States, was to look at how the company could improve its human rights record after a host of negative news stories. Earlier that year, the group’s technology had been linked publicly to spying or attempted spying on the murdered Saudi journalist Jamal Khashoggi by Saudi Arabian security forces, which it denied. The group was acquired in 2019 by a London-based private equity group, Novalpina, which hired Araud to recommend ways to make the company’s safeguard procedures “more rigorous and a bit more systematic,” he said.
The write up explains how a prospect becomes an NSO Group customer:
Its [the Pegasus software and access credentials] export is regulated “like an arms sale,” said Araud, meaning NSO must seek approval from the Israeli government to sell it, and state clients then sign a lengthy commercial contract stipulating how the product will be used. They are meant to deploy Pegasus only to tackle organised crime or terrorism — the company markets itself this way — but Araud said “you could see all the potential for misuse, even though the company wasn’t always responsible.”
The argute veteran of the French ambassadorial team maybe, possibly, could have discerned the potential for misuse of the Pegasys system.
The write up includes this information, allegedly direct from the former diplomat, who obviously provides information diplomatically:
In a firm that practices “a form of extreme secrecy,” he says he nonetheless became convinced that NSO Group worked with Israel’s Mossad secret services, and possibly with the CIA. He said there were three Americans who sat on the group’s advisory board with links to the US intelligence agency, and the company has said that its technology cannot be used to target US-based numbers. “There’s a question about the presence of Mossad and the CIA. I thought it was both of them, but I have no proof,” he said. “But I suspect they’re both behind it with what you call a ‘backdoor’.” A “backdoor” is a technical term meaning the security services would be able to monitor the deployment of Pegasus and possibly the intelligence gathered as a result.
Interesting. Several years ago, the BBC published “When Is a Diplomat Really Just a Spy?” In that 2018 write up, the Beeb stated:
So where do you draw the line between official diplomacy and the murky world of espionage? “Every embassy in the world has spies,” says Prof Anthony Glees, director of the Centre for Security and Intelligence Studies at the University of Buckingham. And because every country does it, he says there’s “an unwritten understanding” that governments are prepared to “turn a blind eye” to what goes on within embassies.
Would French diplomats have some exposure to ancillary duties at a French embassy? Potentially.
Stephen E Arnold, August 3, 2021
China: Making Technology into a Friend Magnet in Africa
July 27, 2021
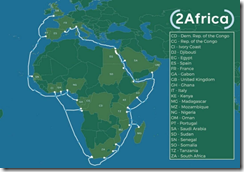
I don’t know much about Africa. I remember studying about Belgium’s wonderful and humane approach, but China has found technology more agreeable than Léopold II’s tactics. “Chinese Tech, Ignored by the West, Is Taking over Africa’s Cyberspace” reports:
While China’s telecom giant Huawei has come under increasing attack in the US and the European Union, it is thriving in Africa…
The drive to lure people comes as Huawei faces mounting attacks from the West. But in Africa, the company has a solid base. Currently, Huawei is active in most African countries. According to an Atlantic Council study – “The Digital Infrastructure Imperative in African Markets,” – around 50 percent of Africa’s 3G networks and 70 percent of its 4G networks are built by Huawei.
What’s Huawei’s secret sauce? The article quotes an expert who asserts:
“Huawei has a big competitive advantage because it’s got access to state capital,” says Eric Olander, managing editor of The China Africa Project, a portal that monitors Chinese business ventures across the continent.
What’s that “state capital” enable? Check out this map. The white line is cable which surrounds the African continent. Sixteen major nodes are planned. The 5G system will connect hundreds of millions of people.
Maybe the Google Loon balloons will be given another shot at the Internet connectivity the online ad company deployed in Puerto Rico. Facebook had model airplane-type devices. And Elon Musk has nifty satellite things. But for now, Huawei is having its way with 5G, the Internet connectivity, and capturing a growing market for devices and services.
Stephen E Arnold, July 27, 2021
How about That 5G?
March 26, 2021
Here we have some premium marketing hoo hah from Digital Trends, “8 Exciting Use Cases that Show What 5G Can Really Do.” In our experience, most people find 4G,LTE, and ATT DSS-fake-5G to be faster than 5G. The write-up seems to presage a time when 5G Ultra Wideband networks have expanded much farther than they have. Writer Jacob Kienlen envisions:
“Like any upgrade to our mobile network infrastructure, the most exciting aspect is the speed and consistency it brings. That, combined with latency reductions, is enough to start predicting some of the opportunities 5G will provide in the coming years. Some of the most obvious 5G use cases are related to technologies that can only really be made better by an improved mobile network. These are things like smart cities, autonomous vehicles, and businesses. The difference between 4G and 5G in that regard is the sheer improvement to consistent high-speed internet on the go. That improvement will bring with it a slew of improvements to existing technologies, but also spark entirely new ones that couldn’t exist with 4G or 3G networks. Here are some of the most exciting 5G cases you can look forward to.”
Can we, really? Right now people are turning off the 5G service on their mobile phones because it is too slow and unreliable. Let us play along, though, and picture a world where 5G has engulfed us coast-to-coast. The eight use cases described here include better home internet; better communication, with both voice and video calls; more viable autonomous vehicles; improved video-streaming quality; advanced agriculture technologies; the rise of more smart cities; a refined Internet of Things; and advances in healthcare, from faster and easier remote diagnoses and operations to health-monitoring smart watches for all.
Keinlen does paint an exciting picture, and perhaps it will come to pass someday. For the foreseeable future, though, these visions remain illusory for most of us.
Cynthia Murrell, March 26, 2021
T-Mobile: Privacy Is a Tough Business
March 12, 2021
Just a bit of mobile phone experience this morning. T Mobile (the magenta or pink outfit) notified me I could opt out of its forthcoming “sell your data” initiative. I dutifully clicked on the link to something which appeared in an SMS as t-mo.com/privacy12. Surprise. The page rendered with a notice that it was a new domain. I fiddled around and was able to locate the page via the search box on T-mobile.com. I filled in the data, including a very long Google ad tracker number. I clicked the submit button and nothing happened. I spotted an email address which was “privacy@tmobile.com.” Guess what? The email bounced. I called 611, the number for customer service. I was told that T Mobile would call me back in 30 minutes. Guess what? No call within the time window.
Privacy is a tough business, and it is one which amuses the marketers and thumbtypers who work with developers to create dark patterns for paying customers. Nice work.
Nifty move. Well, the company is magenta or pink. It is dark, however. Very dark and quite sad.
Stephen E Arnold, March 11, 2021, 435 pm US Eastern
Google Allegedly Sucking User Data: Some Factoids from the Taylor Legal Filing
November 16, 2020
I read the legal filing by Taylor et al v. Google. The case is related to Google’s use of personal data for undisclosed reasons without explicit user permission to consume the user’s bandwidth on a mobile network. You can download the 23 page legal document from this link, courtesy of The Register, a UK online information service. Here’s a rundown a few of the factoids in the document which I found interesting:
- Google’s suck hundreds of megabytes of data is characterized as a “dirty little secret.” Hundreds of megabytes of data does not seem to me to be “little.”
- Google allegedly conducts “passive information transfers which are not initiated by any action of the user and are performed without their knowledge.” I think this means taking data surreptitiously.
- Taking the data uses for fee network connections. I think this means that the user foots the bill for the data sucking.
- Android has a 54.4 percent of the US smartphone market.
- The volume of data “transferred” is about nine megabytes per 24 hours when an Android device is stationary and not in active use.
This graphic appears in the filing on page 11:
The big bar shows Google’s data sucking compared to Apple’s.
The document states:
Google has concealed its misappropriate of Plaintiffs’ cellular data.
I wonder if Google’s senior executives are aware of what the Android phones are allegedly doing. Google was not aware of a number of employee activities, most recently the leak of ideas for thwarting EU regulators.
Is this another example of entitlement management; that is, acting in a manner of a high school science club confident in its superiority over lesser mortals?
Stephen E Arnold, November 16, 2020