Windows System Flaw Exploited In Ransomware
April 15, 2022
Will your Windows 11 set up result in losing your data? That’s a rumor. We learned that there may be other risks in the Microsoft ecosystem as well.
Microsoft Windows is the most deployed operating system in the world. It is also the easiest operating system to learn and, unfortunately, exploit. Tech Radar explains how bad actors hack Windows systems in the article, “Windows And LinkedIn Flaws Used In Conti Ransomware Attacks, Google Warns.”
The Conti ransomware group Exotic Lily work as initial access brokers to hack organizations, steal their digital data, and ransom it back to the rightful owners or sell access to the highest bidder. What is interesting is ransomware groups usually outsource their initial access efforts before taking over the attack, then deploying the malware. Google’s Threat Analysis Group research Exotic Lily and was surprised by the amount of advanced tactics and the large amount of grunt work it does. The Threat Analysis Group discovered that Exotic Lily works in the following way:
“The group would use domain and identity spoofing to pose as a legitimate business, and send out phishing emails, usually faking a business proposal. They would also use publicly available Artificial Intelligence (AI) tools to generate authentic images of humans, to create fake LinkedIn accounts, which would help the campaign’s credibility. After initial contact has been made, the threat actor would upload malware to a public file-sharing service, such as WeTransfer, to avoid detection by antivirus programs, and increase the chances of delivery to the target endpoint. The malware, usually a weaponized document, exploits a zero-day in Microsoft’s MSHTML browser engine, tracked as CVE-2021-40444. The second-stage deployment usually carried the BazarLoader.”
The Threat Analysis Group believes Exotic Lily is an independent operator and works for the highest bidder. It has used ransomware attacks based on Conti, Wizard Spider, and Dial. Exotic Lily targets healthcare, cyber security, and IT organizations, however, it has been expanding its victim base.
But is Google overstating, do some marketing, or trying to help out valued users?
Whitney Grace, April 11, 2022
PR or Reality? Only the Cyber Firms Know the Answer
April 6, 2022
Cyber crimes are on the rise. Businesses and individuals are the targets of malware bad actors. IT Online details how cyber security firms handle attacks: “What Happens Inside A Cybercrime War-Room?” As a major business player in Africa, South Africa fends off many types of cyber attacks: coin miner modules, viruses downloaded with bad software, self-spreading crypto mining malware, and ransomware.
The good news about catching cyber criminals is that white hat experts know how their counterparts work and can use technology like automation and machine learning against them. Carlo Bolzonello is the country manager for South Africa’s Trellis’s branch. He said that cyber crime organizations are run like regular businesses, except their job is to locate and target IT vulnerable environments. Once the bad business has the victim in its crosshairs, the bad actors exploit it for money or other assets for exploration or resale.
Bolzonello continued to explain that while it is important to understand how the enemy works, it is key that organizations have a security operations center armed with various tools that can pull information about possible threats into one dashboard:
“That single dashboard can show where a threat has emerged, and where it has spread to, so that action can be taken, immediately. It can reveal whether ransomware has gained access via a “recruitment” email sent to executives, whether a “living off the land” binary has taken hold via a download of an illicit copy of a movie, or whether a coin miner module has inserted itself via pirated software. Having this information to hand helps the SOC design and implement a quick and effective response, to stop the attack spreading further, and to prevent it costing money for people and businesses.”
Having a centralized dashboards allows organizations respond quicker and keep their enemies in check. Black hat cyber organizations actually might have a reverse of a security operations center that allow them to locate vulnerabilities. PR or reality? A bit of both perhaps?
Whitney Grace, April 6, 2022
Anti-Drone Measures: A Bit Like Enterprise Cyber Security?
April 5, 2022
The big news is that whatever anti-drone technology is being used by “the West”, it is not working at 100 percent efficiency. The Wall Street Journal, published on April Fool’s Day, the story “Drones Evade West’s Air Defense.” I could not spot the exact write up in my online resources, but this particular item is in the dead tree edition. If you go to an office which has humanoids who subscribe to the hard copy, you can check out the story on Page A-9. Story locations vary by edition because… advertising.
There is an online version with the jazzy title “NATO Investigates How Russian and Ukrainian Drones Bypassed Europe’s Air Defense System.” You might be able to view the article at this link, but you probably will either have to pay or see a cheerful 404 error. These folks are in the money business. News — mostly like the Ford 150 — is cargo, and it has a cult I believe.
The point of both write ups is that both Russian and Ukrainian drones have not be interdicted by anti-drone systems. How did those in neighboring companies know that Russian and Ukrainian drones were entering their air space and zipping through their anti-droned borders?
Drones crashed. People walked up and noted, “Okay, explosives on that one.” Another person spots a drone in a field and says, “Looks like this one has cameras, not bombs.”
Countries whose borders have been subject to drone incursions include Romania, Croatia, and Poland. There may be others, but some of the countries have areas which are a difficult to reach, even for an Eva Zu Beck type of person.
NATO is looking into the anti drone measures. That makes sense, since most vendors of military grade anti drone systems have PowerPoint decks which make it clear, “Our system works.” Should I name vendors? Nah, remember Ubiquiti and Mr. Krebs. (That sounds like a children’s program on a PBS station to me.) Slide decks become the reality until a drone with explosives plops down near a pre-school.
My immediate reaction to these Wall Street Journal stories was, “Maybe the anti-drone defense vendors operate with the same reliability as the vendors of enterprise cyber security systems?” The PowerPoint decks promise the same efficacy. There are even private YouTube videos which show drone defense vendors systems EMPing, blasting, or just knocking those evil constructs out of the sky. (Check out Anduril’s offering in this collision centric method, please.)
For several years I followed drone technology for an investment outfit. I learned that the information about the drone described devices best suited for science fiction. I read patents which were not in the fiction section of my local library. I watched YouTube videos with nifty DaVinci Fusion video effects.
The reality?
NATO is now investigating.
My point is that it is easy to sell certain government types advanced technology with PowerPoints and slick videos. This generalization applies to hardware and to software cyber systems.
I don’t need to invoke the SolarWinds’ misstep. I don’t need to recycle the information in the Wall Street Journal stories or the somewhat unusual content in Perun’s drone video.
Is procurement to blame? Partially. I think that Parkinson’s Law (1958) gets closer to the truth, particularly when combined with the observations in the Peter Principle (1971). Universals are at work with the assistance of fast talkers, PowerPoints, and video “proof”.
Stephen E Arnold, April 4, 2022
System Glitches: A Glimpse of Our Future?
April 4, 2022
I read “Nearly All Businesses Hit by IT Downtime Last Year – Here’s What’s to Blame.” The write up reports:
More than three-quarters (75%) of businesses experienced downtime in 2021, up 25% compared to the previous year, new research has claimed. Cybersecurity firm Acronis polled more than 6,200 IT users and IT managers from small businesses and enterprises in 22 countries, finding that downtime stemmed from multiple sources, with system crashes (52%) being the most prevalent cause. Human error (42%) was also a major issue, followed by cyber attacks (36%) and insider attacks (20%).
Interesting. A cyber security company reports these data. The cyber security industry sector should know. Many of the smart systems have demonstrated that those systems are somewhat slow when it comes to safeguarding licensees.
What’s the cause of the issue?
There are “crashes.” But what’s a crash. Human error. Humans make mistakes and most of the software systems with which I am familiar are dumb: Blackmagic ATEM software which “forgets” that users drag and drop. Users don’t intuitively know to put an image one place and then put that image another so that the original image is summarily replaced. Windows Defender lights up when we test software from an outfit named Chris. Excel happily exports to PowerPoint but loses the format of the table when it is pasted. There are USB keys and Secure Digital cards which just stop working. Go figure. There are enterprise search systems which cannot display a document saved by a colleague before lunch. Where is it? Yeah, good question. In the indexing queue maybe? Oh, well, perhaps tomorrow the colleague will get the requested feedback?
My takeaway from the write up is that the wild and crazy, helter skelter approach to software and some hardware has created weaknesses, flaws, and dependencies no one knows about. When something goes south, the Easter egg hunt begins. A dead Android device elicits button pushing and the hope that the gizmo shows some signs of life. Mostly not in my experience.
Let’s assume the research is correct. The increase noted in the write up means that software and systems will continue to degrade. What’s the fix? Like many things — from making a government bureaucracy more effective to having an airline depart on time — seem headed on a downward path.
My take is that we are getting a glimpse of the future. Reality is very different from the perfectly functioning demo and the slick assertions in a PowerPoint deck.
Stephen E Arnold, April 4, 2022
Why Did I Change DarkCyber?
March 31, 2022
This week we made available an interview with a senior manager of an intelware company. At lunch, a person asked me why I changed the editorial coverage of DarkCyber and reduced the number of videos I made available.
I sang my favorite song, “I am 77 and the days dwindle down.” The he/she/them ate the burrito and the conversation shifted to electric vehicles.
There is another reason for my focus on interviews. A good example of my rethink appears in “Ubiquiti Seeks $425 Million in Damages Against Industry Blogger Brian Krebs.” The main idea is that writing about cyber security can open the cages of the legal eagles.
The write up reports:
Ubiquiti on Tuesday filed a lawsuit against industry blogger Brian Krebs for $425 million in damages for allegedly falsely accusing the company of “covering up” a cyber attack. According to the complaint, Krebs intentionally misled the public about a data breach and a subsequent blackmail attempt.
I don’t know the particulars of this legal allegation. I do know that I am skeptical of many of the claims made by cyber security firms. The PowerPoint decks are so darned convincing until something goes south.
At my age, I would rather interview people about their products; hence, the shift in the DarkCyber focus. I will continue to ask questions and write what I think is super funny commentary on the information I locate via open sources.
That’s the separating the goose feathers from the giblets. Plus, who wants to deal with the hassles of explaining that the methods of a blogger writing about security are not up to snuff.
I will speak with Tibby and Pepita about their research methods later today. They are usually more interested in delivery vans than online research, but these comprise my research team.
Stephen E Arnold, March 31, 2022
Open Source Software: Do Flashing Neon Signs Say, Bad Actors Welcome?
March 29, 2022
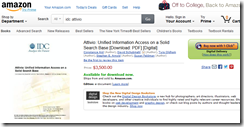
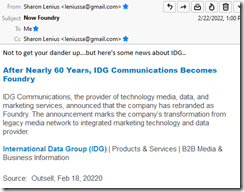
Remember when IDC, one of the units of the Patrick McGovern empire, was a big dog. Before the research unit wound up with swamp mud on its discount sneakers, one of the self-appointed experts suggested my team assemble a big report about — wait for it — open source search. We assembled our data, created profiles similar to those available on my Web site www.xenky.com/vendor-reports, and provided drafts to the estimable IDC. We learned, quite to my surprise, that several of these drafts were listed on Amazon.com for $3,000 each. We did not have a contract, and IDC had no permission to do anything with our profiles of about a dozen open source search solutions. Quite sporty behavior for “the premier global provider of marketing intelligence, advisory services, and events for the information technology, telecommunications, and consumer technology markets.” One IDC expert informed me that the company was called Foundry now. Yeah, who knew?
How do I know IDC sold my work on Amazon without an agreement from me? Check this out:
One take away from our book about open source search software was that security was an afterthought. Did users of open source software think about security? Nope. The users thought about how much money would be saved relying on a “community.” Users like the idea of not having proprietary software companies prevent changes to the code. Security was a community responsibility. Easy assumptions for users who wanted flexibility, reduced costs, and a false sense of no worries about this code.
Does the big outfit which violated my copyright and stole my intellectual property care? The information about the lack of security in an enterprise open source software sector was effectively killed. Here’s an email I received in February 2022. You judge what’s shakin’.
The author is in some way affiliated to Foundry. The entity is called Sharon Lenius, and I assume she will respond to email sent to her at leniussa@gmail.com. Let’s hope she receives a lot of email.
Why this jaunt through the history of IDC and open source search software? If the company had its well oiled second hand store slicker in tip top shape, the security weaknesses of open source search software. Furthermore, the reason open source search as well as other types of software were being adopted by big outfits was cost reduction. The big firms used what could be downloaded, assuming that the “community” would identify flaws, fix them, and assume the responsibilities companies should have shouldered themselves.
When I read “A Developer Altered Open Source Software to Wipe Files in Russia,” I thought “decade old news.” A decade! Do I care? The write up states:
The developer of a popular open source package has been caught adding malicious code to it, leading to wiped files on computers located in Russia and Belarus. The move was part of a protest that has enraged many users and raised concerns about the safety of free and open source software.
I think that the security problems now released as “real news” are significant. Security, code integrity, and malicious actions on the part of the community were not at the top of the to do list 10 years ago and are not at the top of the list today.
Is there a fix? Sure, but like most fixes, it is likely to be too little and too late. Like the self regulation of financial services firms, there is considerable room for creative thinking in the open source software sector. In my upcoming 2022 National Cyber Crime Conference lecture, I will point out specific open source tools which can be used to subvert systems relying on open source software. Why not create a malicious chunk of code, tuck it in a library, and allow an incurious 20 something to undermine an organization?
Why not relay on outfits like mid tier consulting firms to provide actionable information? Why not wait until an armed conflict highlights a ticking IED inside some of the most widely used enterprise applications? Why not act in an ethical, responsible way?
I will be dead and logged off permanently before these questions are answered.
Stephen E Arnold, March 29, 2022
KO for AO Kaspersky?
March 29, 2022
I read “Kaspersky Named First Russian Company on Security Risk List.” Interesting. The write up reports:
The U.S. placed internet-security provider AO Kaspersky Lab on a list of companies deemed a threat to national security, for the first time adding a Russian entity to a list dominated by Chinese telecommunications firms. The Federal Communications Commission on Friday also added China Telecom (Americas) Corp, and China Mobile International USA Inc. to the list.
Now let’s ask another question, “Which venture funding firms accept money from individuals who may have interesting connections?”
Do I see any hands?
No.
That’s my point. Kaspersky is an obvious outfit to probe. What’s the action for the dozens, maybe hundreds, of cyber security firms with non-obvious links to interesting sources of cash. Some bad actors buy yachts. Others villas. A few go for nifty jets. How many are into owning cyber security firms, having access to click PowerPoint decks making the future clear in designer graphics, and hanging out with other technical wizards just sharing casual info?
Who wants to ask, “Where did your money come from?”
Stephen E Arnold, March 29, 2022
Microsoft Security: Time for the Softies to Release Windows 12, a Phone, or a Bid to Buy Tesla?
March 22, 2022
I find the headline amusing. I don’t find the story “Lapsus$ Hackers leak 37GB of Microsoft’s Alleged Source Code” particularly amusing. The Softies have become the outfit with a bright laser dot on the company’s logo. The write up reports:
The Lapsus$ hacking group claims to have leaked the source code for Bing, Cortana, and other projects stolen from Microsoft’s internal Azure DevOps server.
Okay, let’s assume that the story is mostly accurate or meeting a higher standard than that set by the New York Times for its coverage of a certain president’s son and his non-functioning laptop.
The article points out:
Furthermore, we are told that some of the leaked projects contain emails and documentation that were clearly used internally by Microsoft engineers to publish mobile apps. The projects appear to be for web-based infrastructure, websites, or mobile apps, with no source code for Microsoft desktop software released, including Windows, Windows Server, and Microsoft Office. When we contacted Microsoft about tonight’s source code leak, they continued to tell BleepingComputer that they are aware of the claims and are investigating.
Ho ho ho. Perhaps Microsoft’s security, including Defender, lacks some capabilities?
How many breaches are necessary before stakeholders make clear that the brittleness, flaws, and questionable engineering be remediated?
Is some wizard at Microsoft suggesting a re-run of plays which have worked in the past; for example, just put out a news release of Windows or splash cash and PR for a big acquisition? Just imagine a Tesla with Windows File Explorer ads displayed on that great big center display.
Stephen E Arnold, March 22, 2022
Microsoft Defender Is On the Job
March 22, 2022
I don’t know if this write up is an early April Fool thing or actual factual. “Microsoft Defender Goofed Up As It Flagged Its Own Office Updates As Malware” states:
…the company’s Defender for Endpoint security started detecting updates for its own Office app as ransomware. The antivirus program was misidentifying the “OfficeSvcMgr.exe” as malicious software.
Let’s assume there is some truth in the statement OfficeSvcMgr.exe is malicious. My ideas are:
- Careless Microsoft coding was part of OfficeSvcMgr.exe and less flawed coding by another Microsoft technical group spotted the “flaw”
- Microsoft’s quality assurance for its “security” systems remains questionable and the business process flaws have not yet been remediated
- Microsoft is busy adding features to Teams and ads to File Manager so there’s no time or resources to deal with the outstanding Defender service.
Which is closer to the pin? I am into the flawed business processes. But the appeal of putting ads into an operating system is a close second.
Stephen E Arnold, March 22, 2022
Insider Threat News: Two Interesting Situations at Two Sophisticated Companies
March 21, 2022
As you may know, I enjoy pointing out that some big buck cyber security systems struggle with insider threats. Isn’t it easier to put the words “detect and prevent insider threats” on a marketing slide deck than implement the service?
Two events may serve to remind those who wonder about the risks insider threat pose.
First, “Microsoft Investigating Claim of Breach by Extortion Gang” explains that a bad actor entity advertised for insiders. This quote is from the cited article:
We recruit employees/insider at the following!!!! Apple, IBM, and Microsoft. TO NOTE: WE ARE NOT LOOKING FOR DATA, WE ARE LOOKING FOR THE EMPLOYEE TO PROVIDE US A VPN OR CITRIX TO THE NETWORK, or some anydesk.
If accurate, this group (LKAPSUS$) is clear about the why and what it wants. The article alleges that Microsoft is beavering away to determine if its systems have been breached. Don’t the Softies use Defender and other MSFT cyber defense services? Yeah, well.
Second, Apple made headlines because an insider spoofed Apple’s security to the tune of an alleged $10 million. “Former Apple Employee Charged with $10M Fraud” reports:
… Prosecutors allege that while Prasad negotiated with suppliers and entered invoices into the purchasing system, he was conspiring to take kickbacks, using false repair orders to steal parts, and paying for goods and services never received using Apple’s money. The charges go on to allege tax evasion, wire and mail fraud, defrauding the United States, and money laundering, noting that Prasad was fired from Apple in December 2018 after a decade of employment.
How about those internal security and auditing business processes? Apple cares about privacy and security is the firm’s assertion. Again: Marketing is easier than preventing an insider threat.
Why am I bringing up a subject which is not discussed in the specific context of expensive cyber security systems? I offer these examples to make clear that what a cyber outfit says and what its products and services do are less reliable than a decade AvtoVAZ LADA. If you are not familiar with these vehicles, try to find one to drive on a long road trip through the Rocky Mountains. No LADA? Go for a Renault.
Stephen E Arnold, March 21, 2022