Russian Drug Trade Likes That Cryptocurrency
January 3, 2025
 No smart software involved. Just a dinobaby’s work.
No smart software involved. Just a dinobaby’s work.
High tech innovation meets traditional thuggery in Russia’s expanding drug trade. The Global Initiative Against Transnational Organized Crime summarizes its recent report in, “Breaking Klad: Russia’s Dead Drop Drug Revolution.” The write-up includes links to download the report and a related press release. First up, the innovation:
“There has been a groundbreaking shift in the global drug trade, pioneered in Russia and now spreading globally. Unlike traditional drug trafficking models, this system leverages darknet markets and cryptocurrency for anonymous transactions, allowing buyers to retrieve drugs from hidden physical locations, or ‘dead drops,’ rather than direct exchanges. Driven by large platforms such as Kraken, Mega, and Blacksprut [sic], Russian darknet markets control 93% of the global share, generating approximately $1.5 billion in revenue in 2023 alone. This dominance marks a new era for organized crime, with Russia’s digital drug economy vastly surpassing traditional Western darknet markets in scope and influence.”
We are told this digital shift was prompted by several factors. Increasingly restrictive anti-drug policies and strained trade relations with the West contribute. Also, drug dealers now have the technology to give their clients (and themselves) the convenience and anonymity they desire. Wonderful. The writeup mentions that, within Russia, trade in cheap-to-make synthetic drugs like mephedrone is overtaking traditional imports like cocaine and heroin. Which leads us to the thuggery:
“Youth are drawn into this high-tech drug economy, often working as couriers or ‘kladmen’ for online shops—a job that comes with high risks, including violence, criminal charges, and addiction. Violence has become endemic in the system, with enforcers, known as ‘sportsmen,’ meting out harsh punishments for couriers suspected of theft or negligence. This pervasive violence, combined with the easy availability of highly addictive synthetic drugs, is fueling a public health crisis and contributing to rising incarceration rates among young Russians.”
These young people may find miserable company in a growing number of countries; the report warns this model is spreading beyond Russia’s borders. Authorities must adapt to the new reality. Understanding Russia’s darknet markets will help, advises the report.
Cynthia Murrell, January 3 , 2025
Dark Web: Clever and Cute Security Innovations
December 11, 2024
 This write up was created by an actual 80-year-old dinobaby. If there is art, assume that smart software was involved. Just a tip.
This write up was created by an actual 80-year-old dinobaby. If there is art, assume that smart software was involved. Just a tip.
I am not sure how the essay / technical analysis “The Fascinating Security Model of Dark Web Marketplaces” will diffuse within the cyber security community. I want to highlight what strikes me as a useful analysis and provide a brief, high-level summary of the points which my team and I found interesting. We have not focused on the Dark Web since we published Dark Web Notebook, a complement to my law enforcement training sessions about the Dark Web in the period from 2013 to 2016.
This write up does a good job of explaining use of open source privacy tools like Pretty Good Privacy and its two-factor authentication. The write up walks through a “no JavaScript” approach to functions on the Dark Web site. The references to dynamic domain name operations is helpful as well.
The first observation I would offer is that in the case of the Dark Web site analyzed in the cited article is that the security mechanisms in use have matured and, in the opinion of my research team, advanced to thwart some of the techniques used to track and take down the type of sites hosted by Cyberbunker in Germany. This is — alas — inevitable, and it makes the job of investigators more difficult.
The second observation is that this particular site makes use of distributed services. With the advent of certain hosting providers to offer self managed virtual servers and a professed inability to know what’s happening on physical machines. Certain hosting providers “comply” and then say, “If you try to access the virtual machines, they can fail. Since we don’t manage them, you guys will have to figure out how to get them back up.” Cute and effective.
The third observation is that the hoops through which a potential drug customer has to get through are likely to make a person with an addled brain get clean and then come back and try again. On the other hand, the Captcha might baffle a sober user or investigator as well. Cute and annoying.
The essay is useful and worth reading because it underscores the value of fluid online infrastructures for bad actors.
Stephen E Arnold, December 11, 2024
Darknet: Pounding Out a Boring Beat
October 17, 2024
 Just a humanoid processing information related to online services and information access.
Just a humanoid processing information related to online services and information access.
PC World finally got around to sharing the biggest Internet secret: “the Darknet.
The Darknet is better known as the Dark Web and it has been around for while. PC World is treating the Dark Web like a newly discovered secret in: “What Is The Darknet? How The Web’s Secretive, Hidden Underbelly Works.”
If you’ve been living under a rock for the past decade, the Dark Web is the flipside of the Internet. It’s where criminals, freedom fighters, and black marketeers thrive under anonymity. Anything can be bought on the Dark Web, including people, drugs, false passports, credit cards, perusal information, weapons, and more.
The Dark Web is accessed through the downloadable Tor browser. The Tor browser allows users to remain anonymous as long as they don’t enter in any personal information during a session. Tor also allows users to visit “hidden” Web sites that use a special web address ending with a .onion extension. Links to .onion Web sites are found the Hidden Wiki, Haystack, Ahmia, and Torch.
Tor hides Web sites inside layers similar to an onion:
“In order to conceal its origin, the Tor software installed on the user’s PC routes each data packet via various randomly selected computers (nodes) before it is then transferred to the open internet via an exit node.
The data is specially secured so that it cannot be read on any of the Tor computers involved. This entails multiple instances of encryption using the onion-skin principle: Each of the nodes involved in the transport decrypts one layer. As a result, the packet that arrives at a node looks different to eavesdroppers than the packet that the node sends on.”
It’s not illegal to use the Tor and it’s a great tool to browse the Internet anonymously. The problem with Tor is that it is slower than regular Internet, because of the anonymization process rendering.
The article is fill of technical jargon, but does a decent job of explaining the basics of the Darknet. But “real” news? Nope.
Whitney Grace, October 17, 2024
Thoughts about the Dark Web
August 8, 2024
This essay is the work of a dumb humanoid. No smart software required.
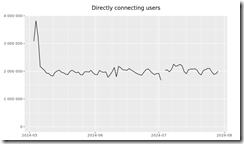
The Dark Web. Wow. YouTube offers a number of tell-all videos about the Dark Web. Articles explain the topics one can find on certain Dark Web fora. What’s forgotten is that the number of users of the Dark Web has been chugging along, neither gaining tens of millions of users or losing tens of millions of users. Why? Here’s a traffic chart from the outfit that sort of governs The Onion Router:
Source: https://metrics.torproject.org/userstats-relay-country.html
The chart is not the snappiest item on the sprawling Torproject.org Web site, but the message seems to be that TOR has been bouncing around two million users this year. Go back in time and the number has increased, but not much. Online statistics, particularly those associated with obfuscation software, are mushy. Let’s toss in another couple million users to account for alternative obfuscation services. What happens? We are not in the tens of millions.
Our research suggests that the stability of TOR usage is due to several factors:
- The hard core bad actors comprise a small percentage of the TOR usage and probably do more outside of TOR than within it. In September 2024 I will be addressing this topic at a cyber fraud conference.
- The number of entities indexing the “Dark Web” remains relatively stable. Sure, some companies drop out of this data harvesting but the big outfits remain and their software looks a lot like a user, particularly with some of the wonky verification Dark Web sites use to block automated collection of data.
- Regular Internet users don’t pay much attention to TOR, including those with the one-click access browsers like Brave.
- Human investigators are busy looking and interacting, but the numbers of these professionals also remains relatively stable.
To sum up, most people know little about the Dark Web. When these individuals figure out how to access a Web site advertising something exciting like stolen credit cards or other illegal products and services, they are unaware of a simple fact: An investigator from some country maybe operating like a bad actor to find a malefactor. By the way, the Dark Web is not as big as some cyber companies assert. The actual number of truly bad Dark Web sites is fewer than 100, based on what my researchers tell me.
A very “good” person approaches an individual who looks like a very tough dude. The very “good” person has a special job for the touch dude. Surprise! Thanks, MSFT Copilot. Good enough and you should know what certain professionals look like.
I read “Former Pediatrician Stephanie Russell Sentenced in Murder Plot.” The story is surprisingly not that unique. The reason I noted a female pediatrician’s involvement in the Dark Web is that she lives about three miles from my office. The story is that the good doctor visited the Dark Web and hired a hit man to terminate an individual. (Don’t doctors know how to terminate as part of their studies?)
The write up reports:
A Louisville judge sentenced former pediatrician Stephanie Russell to 12 years in prison Wednesday for attempting to hire a hitman to kill her ex-husband multiple times.
I love the somewhat illogical phrase “kill her ex-husband multiple times.”
Russell pleaded guilty April 22, 2024, to stalking her former spouse and trying to have him killed amid a protracted custody battle over their two children. By accepting responsibility and avoiding a trial, Russell would have expected a lighter prison sentence. However, she again tried to find a hitman, this time asking inmates to help with the search, prosecutors alleged in court documents asking for a heftier prison sentence.
One rumor circulating at the pub which is a popular lunch spot near the doctor’s former office is that she used the Dark Web and struck up an online conversation with one of the investigators monitoring such activity.
Net net: The Dark Web is indeed interesting.
Stephen E Arnold, August 8, 2024
Tor Friendly ISP Takes a Break
October 17, 2022
I usually do not post “real news.” I am making an exception today because two Tor friendly ISPs have taken a break. Usually when law enforcement takes down a Dark Web centric outfit, there are news releases, news stories, and reports about sentencing (if the “owners” are convicted).
Our routine check of the 24 Tor friendly ISPs we track, Ablative have either “paused” sign ups or disappeared. We are working to track down the individuals who have played a role in these companies. That’s not the easiest task for my team. There are some nifty obfuscation techniques available and creating personas (what some call sock puppets) is easy. Plus, the technique of paying a person in need of cash to set up an account without revealing how that account will be used is easier than ever. (Just check out the folks using free WiFi at a public library, a coffee shop near a university or methadone clinic, or individuals loitering near a food disbursement point.
Stephen E Arnold, October 18, 2022
DarkCyber for November 16, 2021, Now Available
November 16, 2021
DarkCyber, Program 23, is now available at this link. The mid-November 2021 DarkCyber (Number 23 in the 2021 series) includes six stories.
There are two cyber “bytes”. The first reports about the legal pressure being applied to Signal, a maker of secure messaging software. The second explains that an international team of police arrested more than 100 people in Operation HunTor. Sixty-five of these bad actors resided in the United States.
Malware is tough to stamp out. In fact, Rootkits, a well-known method of compromising targets is returning, is regaining popularity. Plus, bad actors have begun placing malware in computer source code. The targets are unaware that their systems have been compromised. The program provides a link to a report about the Trojan Source method. the US government has blacklisted the NSO Group, a developer of specialized software and systems. What’s interesting is that three other firms have been blacklisted as well. One of the organizations responded to the US action with a sign and indifference. Amazon and Microsoft have learned that their customers/users have been subject to somewhat novel attacks. For Amazon, the Twitch “bit” reward system was used for money laundering. Google ads were used to distribute malware via a old-fashioned spoofed pages which looked legitimate but weren’t.
The drone news in this program reveals that Russia presented more than 200 war fighting technologies at a recent trade show in Lima, Peru. The point DarkCyber makes is that Russia perceives South America as a market ripe for sales. DarkCyber is produced every two weeks by Stephen E Arnold, publisher of the Beyond Search blog at www.arnoldit.com/wordpress and subject matter expert in some interesting technical specialties.
Kenny Toth, November 16, 2021
The Darknet: a Dangerous Place
October 6, 2021
Criminal activity on the Darknet is growing and evolving. One person who has taken it on themselves to study the shadow realm shares some of their experiences and observations with reporter Vilius Petkauskas in, “Darknet Researcher: They Said They’ll Come and Kill Me—Interview” at CyberNews. The anonymous interviewee, who works with research firm DarkOwl, describes a threat to their life, one serious enough to prompt them to physically move their family to a new home. They state:
“There was one specific criminal actor I was going after, trying to figure out where they were operating, who they were involved with, what groups they were affiliated with. I became a target. They turned on me and said, we will find whoever wrote this and come kill them. We will destroy them.”
Yes, poking around the Darknet can be dangerous business. What sorts of insights has our brave explorer found? Recently, there has been a substantial uptick in ransomware, and for good reason. The researcher explains:
“Look at ransomware as a service (RaaS). First and second-generation ransomware lockers were developed by incredibly smart malware developers, cryptologists, and encryption specialists. Those who designed and employed such software were some of the most sophisticated malware developers or ‘elite’ hackers around if you want to label them that. But with the RaaS affiliate model, they’re giving others the chance to ‘rent’ ransomware for as little as a few hundred bucks a year, depending on which strain they’re using. Anyone interested in getting into the business of ransomware can enter the market without necessarily having any prior or expert knowledge of how to conduct an enterprise-level attack against a network. Some of the gangs, like Lockbit 2.0 are nearly entirely automated, and their affiliates don’t need to have the slightest clue what they’re doing. You just push, plug, and play. Identify the victim, drop it onto the network, and the rest is taken care of.”
How convenient. Getting into the target’s network, though, is another matter. For that criminals turn to
initial access brokers (IABs), also located on the Darknet, who help breach networks through vulnerabilities, leaked credentials, and other weaknesses. See the write-up for more of the researchers hard-won observations. They close with this warning—there is more going on here than opportunists looking to make a buck. Espionage and cyber terrorism are also likely involved, they say. We cannot say we are surprised.
Cynthia Murrell, October 6, 2021
DarkCyber for September 21, 2021 Now Available
September 21, 2021
DarkCyber for September 21, 2021, reports about the Dark Web, cyber crime, and lesser known Internet services. The program is produced every two weeks. This is the 19th show of 2021. There are no sponsored stories nor advertisements. The program provides basic information about subjects which may not have been given attention in other forums. The program is available at this link.
This week’s program includes five stories.
First, we provide information about two online services which offer content related to nuclear weapons. Neither source has been updated for a number of months. If you have an interest in this subject, you may want to examine the information in the event it is disappeared.
Second, you will learn about Spyfone. DarkCyber’s approach is to raise the question, “What happens when specialized software once considered “secret” by some nation states becomes available to consumers.
Third, China has demonstrated its control of certain online companies; for example, Apple. The country can cause certain applications to be removed from online stores. The argument is that large US companies, like a French bulldog, must be trained in order stay in the Middle Kingdom.
Fourth, we offer two short items about malware delivered in interesting ways. The first technique is put malicious code in a video card’s graphics processing unit. The second summarizes how “free” games have become a vector for compromising network security.
The final story reports that a Russian manufacturer of drones is taking advantage of a relaxed policy toward weapons export. The Russian firm will produce Predator-like drones in countries which purchase the unmanned aerial vehicles. The technology includes 3D printing, specialized software, and other advanced manufacturing techniques. The program includes information about they type of kinetic weapons these drones can launch.
DarkCyber is produced by Stephen E Arnold and his DarkCyber research team. You can download the program from the Beyond Search blog or from YouTube.
Kenny Toth, September 21, 2021
DarkCyber for July 27, 2021: NSO Group Again, Making AWS Bots, How Bad Actors Scale, and Tethered Drones
July 27, 2021
The 15th DarkCyber for 2021 addresses some of the NSO Group’s market position. With more than a dozen news organizations digging into who does what with the Pegasus intelware system, the Israeli company has become the face of what some have called the spyware industry. In this program, Stephen E Arnold, author of the Dark Web Notebook, explains how bad actors scale their cyber crime operations. One thousand engineers is an estimate which is at odds with how these cyber groups and units operate. What’s the technique? Tune in to learn why Silicon Valley provided the road map for global cyber attacks. If you are curious, you can build your own software robot to perform interesting actions using the Amazon AWS system as a launch pad. The final story explains that innovation in policing can arrive from the distant pass. An 18th century idea may be the next big thing in law enforcement’s use of drones. DarkCyber is produced by Stephen E Arnold, who publishes Beyond Search. You can access the blog at www.arnoldit.com/wordpress and view the DarkCyber video at this link.
Kenny Toth, July 27, 2021
Tor Compromised?
July 9, 2021
I read “Tor Encryption Can Allegedly Be Accessed by the NSA, Says Security Expert.” I was stunned. I thought that the layers of encryption, the triple hop through relays, and the hope that everything worked as planned was bulletproof. And who funded Tor in the first place? What’s the status of the not-for-profit foundation today? Why were some European entities excited about cross correlating date and time stamps, IP addresses, and other bits of metadata? I don’t have answers to these questions, nor does the write up.
The article presents this information:
A security expert by the name of Robert Graham, however, has outlined his reasons for actually believing that the NSA might not even need tricks and paltry exploits in order for them to gain access to Tor, according to a blog post on Erratasec. Why? The security expert notes that this is because they might already have the keys to the kingdom. If they don’t, then they might be able to, according to arsTechnica.
Let me see if I can follow the source of this interesting assertion. TechTimes (the outfit publishing the “Tor Encryption Can” story cited above) quotes a security expert. There was a source called Erratasec. Then there was a story on ars Technica.
Now I think that Tor software and the onion method have security upsides and downsides. I also know that what humans create, other humans can figure out. I think the point of the write up is that anyone who uses Tor should embrace the current version.
Can NSA or any other intelligence entity figure out who is doing what, when, and why? My view is that deobfuscation methods are advancing. The fact that bad actors are shifting from old-school Dark Web sites to other channels speaks volumes. Bad actors have been shifting to messaging services which feature end-to-end encryption (E2EE) and do not require a particularly hard-to-complete registration process. But this shift from the “old” Dark Web to the “new” Dark Web began several years ago. Bad actors have been aware that other secure communications options were Job One for years. My thought is that this story in interesting, just not focused on what is actually further consumerizing criminal behavior. The action has shifted, and the US may not be the leader in making sense of the new types of communications traffic.
Stephen E Arnold, July 9, 2021