Indian Regulators Pursue Market Manipulators Around Web
January 11, 2018
Apparently, efforts by India’s market watchdog have driven manipulators in that country to explore alternative methods of communication. So we learn from the article, “Market Manipulators Take To Dark Web, Whatsapp As Sebi Steps Up Surveillance” at India’s NDTV. Note that a “multi-bagger” is a deal promising multi-fold returns. We’re told:
Market manipulators have hooked onto dark web and private chat groups on messaging apps like WhatsApp and Telegram for sharing ‘multibagger’ stock tips and unpublished price sensitive information about listed firms. This has prompted the exchanges and the regulator to beef up the ‘whistleblower’ framework to encourage people, including investors and those working with various market intermediaries, to anonymously give a tip-off on such groups. The shift to these platforms follow an enhanced vigil by the capital markets watchdog Sebi (Securities and Exchange Board of India) and the stock exchanges on social media platforms like Facebook and Twitter, while the regulator can also seek call data records from telecom firms for its probe.
The article notes that both the National Stock Exchange of India and the Bombay Stock Exchange have tip-off systems in place and that officials are considering ways to reward whistleblowers. Both exchanges are using social media analytics to monitor for rumors and news reports about companies they have listed. They are also analyzing the last year’s worth of trade data for such companies, hoping to spot any breaches of norms. So far, Sebi has taken action against some parties for providing investment advice without a registration. The article observes that last year, Sebi suggested banning the exchange of “unauthorized trading tips” through chat apps, social media, and securities-related games and competitions; however, no such regulation has been put in place as of yet.
Cynthia Murrell, January 11, 2018
AlphaBay Takedown Just One Chapter in Dark Web Saga
January 9, 2018
Did the takedown of AlphaBay last summer have much effect, or will black markets on the dark web carry on with business as usual? Both, according to Wired’s article, “The Biggest Dark Web Takedown Yet Sends Black Markets Reeling.” Writer Andy Greenberg details the immediate aftermath as customers of AlphaBay, the largest dark web marketplace in existence, frantically searched for other sources—apparently causing technical difficulties for two of the leading alternatives. He also notes the (reasonable) secrecy around just how the FBI pulled this off, causing other dark web vendors to wonder whether they will be next.
On the other hand, a robust demand for black market goods has been a fact of life for millennia, and that does not stop with AlphaBay’s defeat. Greenberg writes:
Even so, the chaos in the wake of AlphaBay’s disappearance shouldn’t deal a death blow to the dark web’s vibrant drug trade, or even cause much more than a temporary shakeup, says Carnegie Mellon’s Christin. He points to prior dark web crises like the 2013 takedown of the Silk Road, the bust of the Silk Road’s sequel site in late 2014, or the so-called ‘exit scam’ pulled by the dark web market Evolution in 2015, in which its administrators abruptly absconded with their patrons’ bitcoins. Each time, Christin points out, the dark web’s overall business took a temporary dive, but came roaring back more quickly after those setbacks and continued to grow as a whole. AlphaBay, for example, had more than 20 times as many product listings as the original Silk Road. (Some research has found that even bad news about the dark web markets only attracts more users to them.) And AlphaBay’s buyers and customers will eventually find a new home.
And so the adventure continues. What is next in the fight between law enforcement and dark web marketplaces? Stay tuned.
Cynthia Murrell, January 9, 2018
The Dark Web: Becoming Trendy? Yep
January 4, 2018
I track articles which suggest that the Dark Web is becoming trendy. My fave for 2017 was the supermodel who was to be auctioned as a sex slave via the Dark Web. Fake news? Who knows. One lucky person of interest faces a trial in Italy.
The leader in the Dark Web trend making is Wired Magazine and its story “An Interview With Darkside, Russia’s Favorite Dark Web Drug Lord.” The Dark Web Notebook team has no easy way to tell if the write up about the interview with a Dark Web drug kingpin is real or more like the information distributed by some other “real” journalism outfits.
We did note three interesting comments in the write up. Let’s tally these and remind you to read the original story:
- Darkside says that RAMP makes around $250,000 a year from its brisk drug trafficking business. [With the shuttering of Dark Web drug markets, the estimated revenue seems low. The dealer subscription service is a nice angle. The DarkCyber report about the economics of online drug trafficking suggest that RAMP is an outlier both in its longevity (five years of operation) and its approach to business.]
- Darkside says that he favors human intermediated processes, not smart software. [One issue with humans is that they talk. Presumably Darkside has a way to zip the lips of his colleagues, subscribers, and customers. However, he did allegedly “talk” with Wired. No word on whether the information was obtained face to face, via a phone call, or a digital channel like encrypted email. Loose lips sink ships and Dark Web drug markets.]
- Darkside does not “mess with the CIA.” [This is interesting. A number of enforcement agencies are working to shutter Dark Web contraband sites. Examples range from Interpol to the Dutch authorities, German and Czech Republic investigators, and, of course, US enforcement entities. How does Darkside know which investigator is from what country? Not even some of the parallel enforcement authorities know what other countries’ agents are doing on a daily basis. We have seen a list of more than 1,500 Dark Web sites operated by police. Maybe RAMP is such a spoofed site?]
Interesting information. Now about that “real” news thing.
Stephen E Arnold, January 4, 2018
Dark Cyber, January 2, 2018, Now Available
January 2, 2018
Dark Cyber, a weekly video news program about the Dark Web, is now available. The January 2, 2018, program can be viewed at www.arnoldit.com/wordpress and on Vimeo at https://vimeo.com/248961405.
Dark Cyber reveals the connection between zero day exploits and Tor de-anonymization. Specialist vendors like Gamma Group Finfisher, the Hacking Team and NSO Group provide technology to law enforcement and intelligence professionals. These software components make it possible to strip away some of the security the Onion Router software bundle implements for Dark Web access. Zerodium, One high profile vendor of these exploits is Zerodium. Dark Cyber reveals the million dollar price tag on new Tor exploits.
Viewers will learn about the new wave of take downs and seizures of Surface Web and Dark Web sites. With more than 20,000 sites affected, would be scofflaws may be visiting Web sites operated by law enforcement agencies in the UK, the Netherlands, and dozens of other countries.
The program reports that Grams and its sister site Helix have been taken offline. Grams provided a “drug” centric Dark Web search service for three years until it went dark in mid December 2017. Helix offered digital currency laundering and mixing services. These also were shuttered. The Grams Helix technology was offered with an application programming interface or API. The idea was that developers could include Grams and Helix services in third party applications. Dark Cyber reveals that the administrator of these sites and services stepped away from these Dark Web offerings because of the work required to deal with stepped up enforcement and technological change.
Dark Web is a weekly video program distributed via YouTube and Vimeo. The program provides information about the Dark Web and about the tools and technologies used to hide, obfuscate, and encrypt a wide range of online activities, products, and services.
You can view the video at www.arnoldit.com/wordpress.
Kenny Toth, January 2, 2018
Dark Cyber Now on Vimeo
December 27, 2017
The Dark Cyber video for December 26, 2017, is now available on Vimeo. Dark Cyber is a new series of videos from Stephen E Arnold’s Beyond Search HonkinNews Productions. You can view the Vimeo program at https://vimeo.com/248450035.
Stephen E Arnold, December 27, 2017
Dark Cyber: December 26, 2017, Program Available
December 26, 2017
The Dark Cyber team has released the December 26, 2017, program. You can access the news show via YouTube at this link. The program is also available via Vimeo at this link. The program includes these stories:
- Information about Blackdot Solutions’ social media and analytics technology. What makes this important is that Blackdot has extended Relativity’s eDiscovery platform so that other types of data can be integrated with the Relativity system. The pay off is a more robust investigative and legal discovery capability.
- The useful functionality of a new Dark Web search system named Ichidan. With this free tool, an analyst can probe specific ONION urls in order to obtain clues about possible Dark Web server vulnerabilities.
- How to locate up to the date information about the location of Dark Web sites engaged in questionable eCommerce activities. With the failure of some Dark Web search services to update in a timely manner, finding pointers can be difficult. Dark Cyber reveals that there are three ways to track down the site one wishes to investigate.
In January 2018, Dark Cyber introduces a new look and adds news features. Special programs featuring interviews with individuals with specific expertise related to Dark Cyber activities will be released. Plus, the company profiles will be expanded. The first program for 2018 takes a look at Trovicor, an important intercept and analytics platform which serves the governments of more than 35 countries.
If you have questions or wish to request specific companies for the Dark Cyber team to profile, write us at darkcyber333 at yandex dot com.
Kenny Toth, December 26, 2017
Dark Cyber, December 19, 2017, Now Available
December 19, 2017
Dark Cyber (a new series from Stephen E Arnold, publisher of Beyond Search) provides an insider’s look at Oxygen Forensic Detective. The December 19, 2017, video explains what information can be extracted from a mobile computing device by investigators. The Detective software includes a function which can identify, extract, and organize contacts from the mobile device and from cloud services to which the device owner connected. The investigator can then click to see the most frequently called contacts and display the location of individuals on a digital map.
Stephen E Arnold said:
Individuals who engage in high-risk behaviors lack a good understanding of the information which can be pulled from a mobile computing device. Oxygen Forensic Detective is one example of the remarkable investigative and analytic tools now in active use in more than 100 countries by enforcement and intelligence personnel.
He added:
Detective is able to extract high-value information from messaging applications as well as more than 5,000 separate programs which run on a mobile computing device. Oxygen Forensics’ technical team releases frequent updates which allows Detective users to keep pace with rapid technical changes in the mobile computing sector.
The December 19, 2017, Dark Cyber program also reveals that Wikipedia has a Dark Web presence. The Dark Cyber research team notes that when high-value sites make their content available on the Dark Web, that content acts like a magnet to pull new users to the obfuscated Tor environment.
The program concludes with news that 18 Bitcoin ATM machines will be online and available in Atlanta, Georgia. A Bitcoin ATM makes it easier to convert digital Bitcoin into hard cash in the form of US dollars.
You can view this week’s video at this link.
SIXGILL: Dark Web Intelligence with Sharp Teeth
December 14, 2017
“Sixgill” refers to the breathing apparatus of a shark. Deep. Silent. Stealthy. SIXGILL offers software and services which function like “your eyes in the Dark Web.”
Based in Netanya, just north of Tel Aviv, SIXGILL offers services for its cyber intelligence platform for the Dark Web. What sets the firm apart is its understanding of social networks and their mechanisms for operation.*
The company’s primary product is called “Dark-i.” The firm’s Web site states that the firm’s system can:
- Track and discover communication nodes across darknets with the capability to trace malicious activity back to their original sources
- Track criminal activity throughout the cyber crime lifecycle
- Operate in a covert manner including the ability to pinpoint and track illegal hideouts
- Support clients with automated and intelligence methods.
The Dark-i system is impressive. In a walk through of the firm’s capabilities, I noted these specific features of the Dark-i system:
- Easy-to-understand reports, including summaries of alleged bad actors behaviors with time stamp data
- Automated “profiles” of Dark Web malicious actors
- The social networks of the alleged bad actors
- The behavior patterns in accessing the Dark Web and the Dark Web sites the individuals visit.
- Access to the information on Dark Web forums.
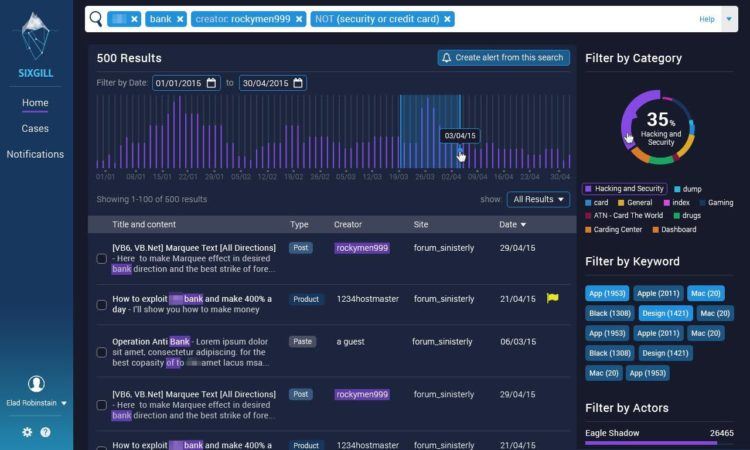
Details about the innovations the company uses are very difficult to obtain. Based on open source information, a typical interface for SIXGILL looks like this:
Based on my reading of the information in the screenshot, it appears that this SIXGILL display provides the following information:
- The results of a query
- Items in the result set on a time line
- One-click filtering based on categories taken from the the sources and from tags generated by the system, threat actors, and Dark Web sources
- A list of forum posts with the “creator” identified along with the source site and the date of the post.
Compared with reports about Dark Web activity from other vendors providing Dark Web analytic, monitoring, and search services, the Dark Web Notebook team pegs s SIXGILL in the top tier of services.
Dark Cyber for December 12, 2017, Now Available
December 12, 2017
The HonkinNews Dark Cyber program for December 12, 2017, presents a snapshot of a next-generation investigation analysis system, data about illegal drugs on the Dark Web, and news about a secure chat system which runs within Tor. Most analysts and investigators have access to a range of software and hardware devices designed to make sense of data from a range of computing devices. However, the newer systems offer visual analyses which often surprise with their speed, power, and ability to deliver “at a glance” insights. This week’s Dark Cyber examines Brainspace, now a unit of Cyxtera. Brainspace’s graphics are among the most striking in the intelligence analysis market. The role that Cyxtera plays is perhaps more important. The company is a roll up of existing businesses and focused on cloud delivery of advanced software and services. Dark Cyber also provides facts from a recent European Union report about illegal substances on the Dark Web. What’s interesting about the report is that the data it presents seems to understate the magnitude of the volume of drug sales via the Dark Web. You can download the report without charge from the url included in this week’s program. The final story addresses what is a growing challenge for law enforcement and intelligence authorities: Secure chat within Tor. The Dark Cyber team reports that Anonymous Portugal has made this alleged breakthrough. (The second edition of the Dark Web Notebook will include a new chapter about chat and related services plus ways to compromise these communications.) You can view the program at this link https://youtu.be/E2jNuJXblOI.
Kenny Toth, December 12, 2017
HonkinNews Dark Cyber for December 5, 2017, Now Available
December 5, 2017
The December 5, 2017, Dark Cyber program includes three stories and one feature. If you were wondering if the Dark Web offered high-value content, you will find our report about the New York Times useful. The “nation’s newspaper” or the “Gray Lady” to some has a Dark Web site. Dark Cyber asks two questions about this surprising online move. Uber is a popular, controversial, and litigation magnet. For those who depend on Uber, the fact that valid Uber accounts are available for purchase on the Dark Web may be troubling. Dark Cyber adds to the concern by pointing to Surface Web sites which also sell stolen Uber accounts. Free rides on someone else’s account my sound like a good idea. The reality is that you may be violating one or more laws if your dabble in stolen Uber accounts. The feature this week answers in part the question, “Exactly what type of reports does a high-end intelligence analysis system provide to an authorized user?” Dark Cyber uses reports generated by Tovek, an intelligence software and services firm based in Prague, for the answer. As you review the outputs, please, keep in mind that Dark Cyber has intentionally blurred the images for security. Pay particular attention to the mapping of a person of interest’s travel data. The final story for December 5, 2017, is a quick look at what a consumer newspaper revealed about Google Chrome browser’s “incognito” mode. If you thought your online behaviors were hidden from monitoring, you may want to think about what Google Chrome Incognito does not do for its users. You can view the program at this link https://youtu.be/LwGDBczVj10
Kenny Toth, December 5, 2017