Can Clarity Confuse? No, It Is Just Zeitgeist
August 1, 2025
 This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
In my newsreader this morning, popped this article “Why Navigating Ongoing Uncertainty Requires Living in the Now, Near, and Next.” I was not familiar with Clarity Global. I think it is a public relations firm. The CEO of the firm is a former actress. I have minimal knowledge of PR and even less about acting.
I plunged into the essay. The purpose of the write up, in my opinion, was to present some key points from a conference called “TNW2025.” Conference often touch upon many subjects. One event at which I spoke this year had a program listing on six pages the speakers. I think 90 percent of the people attending the conference were speakers.
The first ideas in the write up touch upon innovation, technology adoption, funding, and the zeitgeist. Yep, zeitgeist.
As if these topics were not of sufficient scope, the write up identifies three themes. These are:
- “Regulation is a core business competency”
- “Partnership is the engine of progress”
- “Culture is critical”.
Notably absent was making money and generating a profit.
What about the near, now, and next?
The near means having enough cash on hand to pay the bills at the end of the month. The now means having enough credit or money to cover the costs of being in business. Recently a former CIA operative invited me to lunch. When the bill arrived, he said, “Oh, I left my billfold at home.” I paid the bill and decided to delete him from my memory bank. He stiffed me for $11, and he told me quite a bit about his “now.” And the next means that without funding there is a greatly reduced chance of having a meaningful future. I wondered, “Was this ‘professional’ careless, dumb, or unprofessional?” (Maybe all three?)
Now what about these themes. First, regulation means following the rules. I am not sure this is a competency. To me, it is what one does. Second, partnership is a nice word, not as slick as zeitgeist but good. The idea of doing something alone seems untoward. Partnerships have a legal meaning. I am not sure that a pharmaceutical company with a new drug is going to partner up. The company is going to keep a low profile, file paperwork, and get the product out. Paying people and companies to help is not a partnership. It is a fee-for-service relationship. These are good. Partnerships can be “interesting.” And culture is critical. In a market, one has to identify a market. Each market has a profile. It is common sense to match the product or service to each market’s profile. Apple cannot sell an iPhone to a person who cannot afford to pay for connectivity, buy apps or music, or plug the gizmo in. (I am aware that some iPhone users steal them and just pretend, but those are potential customers, not “real” customers.)
Where does technology fit into this conference? It is the problem organizations face. It is also the 10th word in the essay. I learned “… the technology landscape continues to evolve at an accelerating page.” Where’s smart software? Where’s non-democratic innovation? Where’s informed resolution of conflict?
What about smart software, AI, or artificial intelligence? Two mentions: One expert at the conference invests in AI and in this sentence:
As AI, regulation and societal expectations evolve, the winners will be those who anticipate change and act with conviction.
I am not sure regulation, partnership, and coping with culture can do the job. As for AI, I think funding and pushing out products and services capture the zeitgeist.
Stephen E Arnold, August 1, 2025
China Smart, US Dumb: Is There Any Doubt?
August 1, 2025
 This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
I have been identifying some of the “China smart, US dumb” information that I see. I noticed a write up from The Register titled “China Proves That Open Models Are More Effective Than All the GPUs in the World.” My Google-style Red Alert buzzer buzzed and the bubble gum machine lights flashed.
There is was. The “all.” A categorical affirmative. China is doing something that is more than “all the GPUs in the world.” Not only that “open models are more effective” too. I have to hit the off button.
The point of the write up for me is that OpenAI is a loser. I noted this statement:
OpenAI was supposed to make good on its name and release its first open-weights model since GPT-2 this week. Unfortunately, what could have been the US’s first half-decent open model of the year has been held up by a safety review…
But it is not just OpenAI muffing the bunny. The write up points out:
the best open model America has managed so far this year is Meta’s Llama 4, which enjoyed a less than stellar reception and was marred with controversy. Just this week, it was reported that Meta had apparently taken its two-trillion-parameter Behemoth out behind the barn after it failed to live up to expectations.
Do you want to say, “Losers”? Go ahead.
But what outfit is pushing out innovative smart software as open source? Okay, you can shout, “China. The Middle Kingdom. The rightful rulers of the Pacific Rim and Southeast Asia.
That’s the “right” answer if you accept the “all” type of reasoning in the write up.
China has tallied a number of open source wins; specifically, Deepseek, Qwen, M1, Ernie, and the big winner Kimi.
Do you still have doubts about China’s AI prowess? Something is definitely wrong with you, pilgrim.
Several observations:
- The write up is a very good example of the China smart, US dumb messaging which has made its way from the South China Morning Post to YouTube and now to the Register. One has to say, “Good work to the Chinese strategists.”
- The push for open source is interesting. I am not 100 percent convinced that making these models available is intended to benefit non-Middle Kingdom people. I think that the push, like the shift to crypto currency in non traditional finance, is part of an effort to undermine what might be called “America’s hegemony.”
- The obviousness of overt criticism of OpenAI and Meta (Facebook) illustrates a growing confidence in China that Western European information channels can be exploited.
Does this matter? I think it does. Open source software has some issues. These include its use as a vector for malware. Developers often abandon projects, leaving users high and dry with some reaching for their wallet to buy commercial solutions. Open source projects for smart software may have baked in biases and functions that are not easily spotted. Many people are aware of NSO Group’s ability to penetrate communications on a device by device basis. What happens if the phone home ability is baked into some open source software.
Remember that “all.” The logical fallacy illustrates that some additional thinking may be necessary when it comes to embedding and using software from some countries with very big ambitions. What is China proving? Could it be China smart, US dumb?
Stephen E Arnold, August 1, 2025
Microsoft and Job Loss Categories: AI Replaces Humans for Sure
July 31, 2025
 This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
I read “Working with AI: Measuring the Occupational Implications of Generative AI.” This is quite a sporty academic-type write up. The people cranking out this 41 page Sociology 305 term paper work at Microsoft (for now).
The main point of the 41-page research summary is:
Lots of people will lose their jobs to AI.
Now this might be a surprise to many people, but I think the consensus among bean counters is that humans cost too much and require too much valuable senior manager time to manage correctly. Load up the AI, train the software, and create some workflows. Good enough and the cost savings are obvious even to those who failed their CPA examination.
The paper is chock full of jargon, explanations of the methodology which makes the project so darned important, and a wonky approach to presenting the findings.
Remember:
Lots of people will lose their jobs to AI.
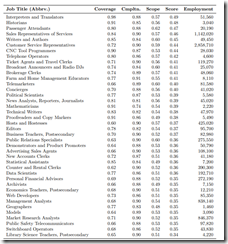
The highlight of the paper in my opinion is the “list” of occupations likely to find that AI displaces humans at a healthy pace. The list is on page 12 of the report. I snapped an image of this chart “Top 40 Occupations with Highest AI Applicability Score.” The jargon means:
Lots of people will lose their jobs to AI.
Here’s the chart. (Yes, I know you cannot read it. Just navigate to the original document and read the list. I am not retyping 40 job categories. Also, I am not going to explain the MSFT “mean action score.” You can look at that capstone to academic wizardry yourself.)
What are the top 10 jobs likely to result in big time job losses? Microsoft says they are:
- People who translate from one language to another
- Historians which I think means “history teachers” and writers of non-fiction books about the past
- Passenger attendants (think robots who bring you a for-fee vanilla cookie and an over-priced Coke with “real cane sugar”)
- People who sell services (yikes, that’s every consulting firm in the world. MBAs, be afraid)
- Writers (this category appears a number of times in the list of 40, but the “mean action score” knows best)
- Customer support people (companies want customers to never call. AI is the way to achieve this goal)
- CNC tool programmers (really? Someone has to write the code for the nifty Chip Foose wheel once I think. After that, who needs the programmer?)
- Telephone operators (there are still telephone operators. Maybe the “mean action score” system means receptionists at the urology doctors’ office?)
- Ticket agents (No big surprise)
- Broadcast announcers (no more Don Wilsons or Ken Carpenters. Sad.)
The 30 are equally eclectic and repetitive. I think you get the idea. Service jobs and work that is repetitive — Dinosaurs waiting to die.
Microsoft knows how to brighten the day for recent college graduates, people under 35, and those who are unemployed.
Oh, well, there is the Copilot system to speed information access about job hunting and how to keep a positive attitude. Thanks, Microsoft.
Stephen E Arnold, July 31, 2025
No Big Deal. It Is Just Life or Death. Meh.
July 31, 2025
 This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
I am not sure about information from old-fashioned television channels is rock solid, but today what information is? I read “FDA’s Artificial Intelligence Is Supposed to Revolutionize Drug Approvals. It’s Making Up Nonexistent Studies.” Heads up. You may have to pay to read the full write up.
The main idea in the report struck me as:
[Elsa, an AI system deployed by the US Food and Drug Administration] has also made up nonexistent studies, known as AI “hallucinating,” or misrepresented research, according to three current FDA employees and documents seen by CNN. This makes it unreliable for their most critical work, the employees said.
To be fair, some researchers make up data and fiddle with “real” images for some peer reviewed research papers. It makes sense that smart software trained on “publicly available” data would possibly learn that making up information is standard operating procedure.
The cited article does not provide the names and backgrounds of the individuals who provided the information about this smart software. That’s not unusual today.
I did not this anonymous quote:
“Anything that you don’t have time to double-check is unreliable. It hallucinates confidently,” said one employee — a far cry from what has been publicly promised. “AI is supposed to save our time, but I guarantee you that I waste a lot of extra time just due to the heightened vigilance that I have to have” to check for fake or misrepresented studies, a second FDA employee said.
Is this a major problem? Many smart people are working to make AI the next big thing. I have confidence that prudence, accuracy, public safety, and AI user well-being is a priority. Yep, that’s my assumption.
I wish to offer several observations:
- Smart software may need some fine tuning before it becomes the arbiter of certain types of medical treatments, procedures, and compounds.
- AI is definitely free from the annoying hassles of sick leave, health care, and recalcitrance that human employees evidence. Therefore, AI has major benefits by definition.
- Hallucinations are a matter of opinion; for example, humans are creative. Hallucinating software may be demonstrating creativity. Creativity is a net positive; therefore, why worry?
The cited news report stated:
Those who have used it say they have noticed serious problems. For example, it cannot reliably represent studies.
As I said, “Why worry?” Humans make drug errors as well. Example: immunomodulatory drugs like thalidomide. AI may be able to repurpose dome drugs. Net gain. Why worry?
Stephen E Arnold, July 31, 20205
Private Equities and Libraries: Who Knew?
July 31, 2025
Public libraries are a benevolent part of the local and federal governments. They’re awesome places for entertainment, research, and more. Public libraries in the United States have a controversial histories dealing with banned books, being a waste of tax paying dollars, and more. LitHub published an editorial about the Samuels Public Library in Front Royal, Virginia: “A Virginia Public Library Is Fighting Off A Takeover By Private Equity.”
In short, the Samuels Public Library refused to censor books, mostly those dealing with LGBTQ+ themes. The local county officials withheld funding and the library might be run by LS&S, a private equity firm that specializes in any fields including government outsourcing and defense.
LS&S has a bad reputation and the CEO said:
“ ‘There’s this American flag, apple pie thing about libraries,’ said Frank A. Pezzanite, the outsourcing company’s chief executive. He has pledged to save $1 million a year in Santa Clarita, mainly by cutting overhead and replacing unionized employees. ‘Somehow they have been put in the category of a sacred organization.’
…
‘A lot of libraries are atrocious,’ Mr. Pezzanite said. ‘Their policies are all about job security. That’s why the profession is nervous about us. You can go to a library for 35 years and never have to do anything and then have your retirement. We’re not running our company that way. You come to us, you’re going to have to work.’”
The author wrote in response to this quote:
“In their defense, I think some of these businesses think they’re doing the right thing. But the valorization of profit has blinded them to seeing the advantages of the public good as a worthy bottom line. Providing for a community might not be profitable, but that doesn’t make it wrong…Efficiency shouldn’t always be the goal, especially when used as a narrowly defined metonym for profitability. The Samuels Public Library, like so many public institutions around the country, works because it serves something other than money.”
Public libraries are the one institution that should never be ripped off. Maybe a private equity firm could work hand in hand with public libraries so they aren’t ripped off by bad actors? Or …?
Whitney Grace, July 31, 2025
Guess Who Coded the Official Messaging App of Russia
July 30, 2025
 This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
The Bloomberg story title “Russia Builds a New Web Around Kremlin’s Handpicked Super App” caused me to poke around in the information my team and I have collected about “super apps,” encrypted messaging services, and ways the Kremlin wants to get access to any communication by Russian citizens and those living in the country and across the Russian Federation. The Bloomberg story is interesting, but I want to add some color to what seems to be a recent development.
If you answered the question “Guess who coded the official messaging app of Russia?” by saying, “Pavel and Nikolai Durov,” you are mostly correct. The official messaging act is a revamped version of VKontakte, the the Facebook knock off coded by Pavel and Nikolai Durov. By 2011, Kremlin authorities figured out that access to the content on a real time social media service like VK was a great way to stamp out dissent.
The Durovs did not immediately roll over, but by 2013, Pavel Durov folded. He took some cash, left Nikolai at home with mom, and set off to find a place for hospitable to his views of freedom, privacy, security, and living a life not involving a Siberian prison. Pavel Durov, however, has a way of attracting attention from government officials outside of Russia at this time. He is awaiting trial in France for a number of alleged online crimes, including CSAM. (CSAM is in the news in the US recently as well.)
Ongoing discussions with VK and an “integrator” have been underway for years. The Kremlin contracted with Sber and today’s VK to create a mandatory digital service for Russian citizens and anyone in the country buying a mobile phone in Russia. The idea is that with a mandatory messaging app, the Kremlin could access the data that Pavel Durov refused to produce.
The official roll out of the “new”, government-controlled VK service began in June 2025. On September 1, 2025, the new VK app must be pre-installed on any smartphone or tablet sold in the country. Early reports suggested that about one million users had jumped on the “new” messaging app MAX. Max is the post-Durov version of VKontakte without the Pavel Durov obstinacy and yapping about privacy.
The Russian online service https://PCNews.ru published “Ministry of Digital: Reports That the MAX Messenger Will Be Mandatory for Signing Electronic Documents Are Not True.” The write up reports that the “official” messaging service “MAX” will not be required for Russian is not true.
Earlier this week (July 28, 2025):
… the [Russian] government of the Kemerovo region is officially switching to using the Russian MAX messenger for all work communications. Before this, the national messenger began to be implemented in St. Petersburg, as we have already reported, Novosibirsk and Tatarstan. Depending on the region, the platform is used both in government structures and in the field of education. In Russia they want to ensure free and secure transfer of user data from WhatsApp and Telegram instant messengers to the Russian MAX platform. From September 1, 2025, the Max messenger will have to be pre-installed on all smartphones and tablets sold in Russia. In late June 2025, the developers announced that over one million users had registered with Max.
This means that not everything the Kremlin requires will reside on the super app MAX. From a government security vantage point, the decision is a good one. The Kremlin, like other governments, has information it tries hard to keep secret. The approach works until something like Microsoft SharePoint is installed or an outstanding person like Edward Snowden hauls off some sensitive information.
The Russians appear to be quite enthusiastic about the new government responsive super app. Here’s some data to illustrate the level of the survey sample’s enthusiasm.
“The Attitude of Russians Towards the National Messenger Has Become Known” reports:
- 55% of respondents admitted that they would like their data to be stored on Russian servers
- 85% communicate with loved ones using messaging apps
- 49% watch the news
- 47% of respondents use instant messengers for work or study
- 38% of respondents supported the idea of creating a Russian national messenger
- 26% answered that they rather support it
- 19% of respondents admitted that they were indifferent to this topic.
Other findings included:
- 36% of Russians named independence from the departure of foreign services among the advantages of creating a domestic messenger
- 33% appreciate popularization of Russian developments
- 32% see a positive from increasing data security
- 53% of respondents liked the idea when in one service you can not only communicate, but also use government services and order goods.
Will Russians be able to circumvent the mandatory use of MAX? Almost anything set up to cage online users can be circumvented. The Great Firewall of China after years of chatter does not seem to impede the actions of some people living in China from accessing certain online services. At this time, I can see some bright young people poking around online for tips and tricks related to modern proxy services, commodity virtual private networks, and possibly some fancy dancing with specialized hardware.
What about Telegram Messenger, allegedly the most popular encrypted messaging super app in Russia, the Russian Federation, and a chunk of Southeast Asia? My perception is that certain online habits, particularly if they facilitate adult content, contraband transactions, and money laundering are likely to persist. I don’t think it will take long for the “new” MAX super app to be viewed as inappropriate for certain types of online behavior. How long? Maybe five seconds?
Stephen E Arnold, July 30, 2025
SEO Plus AI: Putting a Stake in the Frail Heart of Relevance
July 30, 2025
 This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
I have not been too impressed with the search engine optimization service sector. My personal view is that relevance has been undermined. Gamesmanship, outright trickery, and fabrication have replaced content based on verifiable facts, data, and old-fashioned ethical and moral precepts.
Who needs that baloney? Not the SEO sector. The idea is to take content and slam it in the face of a user who may be looking for information relevant to a question, problem, or issue.
I read “Altezza Introduces Service as Software Platform for AI-Powered Search Optimization.” The name Altezza reminded me of a product called Bartesian. This outfit sell a machine that automatically makes alcohol-based drinks. Alcohol, some researchers suggest, is a bit of a problem for humanoids. Altezza may be doing to relevance what three watermelon margaritas do to a college student’s mental functions.
The article about Altezza says:
Altezza’s platform turns essential SEO tasks into scalable services that enterprise eCommerce brands can access without the burden of manual implementation.
Great AI-generated content pushed into a software script and “published” in a variety of ways in different channels. Altezza’s secret sauce may be revealed in this statement:
While conventional tools provide access to data and features, they leave implementation to overwhelmed internal teams.
Yep, let those young content marketers punch the buttons on a Bartesian device and scroll TikTok-type content. Altezza does the hard work: SEO based on AI and automated distribution and publishing.
Altezza is no spring chicken. The company was found in 1998 and “combines cutting-edge AI technology with deep search expertise to help brands achieve sustainable organic growth.”
Yep, another relevance destroying drone based smart system is available.
Stephen E Arnold, July 30, 2025
AI: Pirate or Robin Hood?
July 30, 2025
One of the most notorious things about the Internet is pirating creative properties. The biggest victim is the movie industry followed closely by publishing. Creative works that people spend endless hours making are freely distributed without proper payment to the creators and related staff. It sounds like a Robin Hood scenario, but creative folks are the ones suffering. Best selling author David Baldacci ripped into Big Tech for training their AI on stolen creative properties and he demanded that the federal government step in to rein them in.
LSE says that only a small amount of AI developers support using free and pirated data for trading models: “Most AI Researchers Reject Free Use Of Public Data To Train AI Models.” Data from UCL shows AI developers want there to be ethical standards for training data and many are in favor of asking permission from content creators. The current UK government places the responsibility on content creators to “opt out” of their work being used for AI models. Anyone with a brain knows that the AI developers skirt around those regulations.
When LSE polled people about who should protecting content creators and regulating AI, their opinions were split between the usual suspects: tech companies, governments, independent people, and international standards bodies.
Let’s see what creative genius Paul McCartney said:
While there are gaps between researchers’ and the views of authors, it would be a mistake to see these only as gaps in understanding. Song writer and surviving Beatle Paul McCartney’s comments to the BBC are a case in point: “I think AI is great, and it can do lots of great things,” McCartney told Laura Kuensberg, but it shouldn’t rip creative people off. It’s clear that McCartney gets the opportunities AI offers. For instance, he used AI to help bring to life the voice of former bandmate John Lennon in a recent single. But like the writers protesting outside of Meta’s office, he has a clear take on what AI is doing wrong and who should be responsible. These views and the views of over members of the public should be taken seriously, rather than viewed as misconceptions that will improve with education or the further development of technologies.
Authors want protection. Publishers want money. AI companies want to do exactly what they want. This is a three intellectual body problem with no easy solution.
Whitney Grace, July 30, 2025
Indiscriminate Scanning: Hello, Telegram, This Is for You
July 29, 2025
 This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
I read a version of the message the European Union is sending to Pavel Durov. This super special human is awaiting trial in France for a couple of minor infractions. Yep, minor as in CSAM. Oh, the French judiciary tossed in a few other crimes.
The EU, following France’s long overdue action, is mustering some oomph, according to “The EU Could Be Scanning Your Chats by October 2025 – Here’s Everything We Know”:
Denmark kicked off its EU Presidency on July 1, 2025, and, among its first actions, lawmakers swiftly reintroduced the controversial child sexual abuse (CSAM) scanning bill to the top of the agenda. Having been deemed by critics as Chat Control, the bill aims to introduce new obligations for all messaging services operating in Europe to scan users’ chats, even if they’re encrypted.
After a three year hiatus, the EU is in “could” and “try” mode. The write up says:
As per its first version, all messaging software providers would be required to perform indiscriminate scanning of private messages to look for CSAM – so-called ‘client-side scanning’. The proposal was met with a strong backlash, and the European Court of Human Rights ended up banning all legal efforts to weaken encryption of secure communications in Europe.
Where does Telegram fit into this “could” initiative?
Telegram semi-encrypts. The idea is that the user’s Messenger mini app encrypts a message, adds routing, and whisks the contents to the user… sort of. Telegram has a command-and-control node which receives the encrypted message, the header, assorted metadata, and then decrypts the message in the Telegram command-and-control center. Why? Good question.
Telegram does support complete end-to-end encryption. The command-and-control center just hands off the encrypted message. There is no slam dunk information available about Telegram’s sucking up the metadata for these EE2E messages which may contain text, rich media, or other content objects.
How will Telegram interpret this “could” move? My view is that the French judiciary may have some ways to realign Mr. Durov’s thinking. I understand that France has some lovely prison facilities like the facilities at the French Foreign Legion headquarters and the salubrious quarters in Africa. I would not suggest these are five star hotel type detainment structures, but Mr. Durov’s attorneys may convince him to reconsider his position as a French citizen under the watchful eye of the French legal system.
Stephen E Arnold, August 29, 2025
Microsoft: Knee Jerk Management Enigma
July 29, 2025
 This blog post is the work of an authentic dinobaby. Sorry. Not even smart software can help this reptilian thinker.
This blog post is the work of an authentic dinobaby. Sorry. Not even smart software can help this reptilian thinker.
I read “In New Memo, Microsoft CEO Addresses Enigma of Layoffs Amid Record Profits and AI Investments.” The write up says in a very NPR-like soft voice:
“This is the enigma of success in an industry that has no franchise value,” he wrote. “Progress isn’t linear. It’s dynamic, sometimes dissonant, and always demanding. But it’s also a new opportunity for us to shape, lead through, and have greater impact than ever before.” The memo represents Nadella’s most direct attempt yet to reconcile the fundamental contradictions facing Microsoft and many other tech companies as they adjust to the AI economy. Microsoft, in particular, has been grappling with employee discontent and internal questions about its culture following multiple rounds of layoffs.
Discontent. Maybe the summer of discontent. No, it’s a reshaping or re-invention of a play by William Shakespeare (allegedly) which borrows from Chaucer’s Troilus and Criseyde with a bit more emphasis on pettiness and corruption to add spice to Boccaccio’s antecedent. Willie’s Troilus and Cressida makes the “love affair” more ironic.
Ah, the Microsoft drama. Let’s recap: [a] Troilus and Cressida’s Two Kids: Satya and Sam, [b] Security woes of SharePoint (who knew? eh, everyone]; [c] buying green credits or how much manure does a gondola rail card hold? [d] Copilot (are the fuel switches on? Nope); and [e] layoffs.
What’s the description of these issues? An enigma. This is a word popping up frequently it seems. An enigma is, according to Venice, a smart software system:
The word “enigma” derives from the Greek “ainigma” (meaning “riddle” or “dark saying”), which itself stems from the verb “aigin” (“to speak darkly” or “to speak in riddles”). It entered Latin as “aenigma”, then evolved into Old French as “énigme” before being adopted into English in the 16th century. The term originally referred to a cryptic or allegorical statement requiring interpretation, later broadening to describe any mysterious, puzzling, or inexplicable person or thing. A notable modern example is the Enigma machine, a cipher device used in World War II, named for its perceived impenetrability. The shift from “riddle” to “mystery” reflects its linguistic journey through metaphorical extension.
Okay, let’s work through this definition.
- Troilus and Cressida or Satya and Sam. We have a tortured relationship. A bit of a war among the AI leaders, and a bit of the collapse of moral certainty. The play seems to be going nowhere. Okay, that fits.
- Security woes. Yep, the cipher device in World War II. Its security or lack of it contributed to a number of unpleasant outcomes for a certain nation state associated with beer and Rome’s failure to subjugate some folks.
- Manure. This seems to be a metaphorical extension. Paying “green” or money for excrement is a remarkable image. Enough said.
- Fuel switches and the subsequent crash, explosion, and death of some hapless PowerPoint users. This lines up with “puzzling.” How did those Word paragraphs just flip around? I didn’t do it. Does anyone know why? Of course not.
- Layoffs. Ah, an allegorical statement. Find your future elsewhere. There is a demand for life coaches, LinkedIn profile consultants, and lawn service workers.
Microsoft is indeed speaking darkly. The billions burned in the AI push have clouded the atmosphere in Softie Land. When the smoke clears, what will remain? My thought is that the items a to e mentioned above are going to leave some obvious environmental alterations. Yep, dark saying because knee jerk reactions are good enough.
Stephen E Arnold, July 29, 2025