From the Ostrich Watch Desk: A Signal for Secure Messaging?
December 4, 2025
![green-dino_thumb_thumb[1] green-dino_thumb_thumb[1]](https://www.arnoldit.com/wordpress/wp-content/uploads/2025/11/green-dino_thumb_thumb1_thumb.gif) Another dinobaby post. No AI unless it is an image. This dinobaby is not Grandma Moses, just Grandpa Arnold.
Another dinobaby post. No AI unless it is an image. This dinobaby is not Grandma Moses, just Grandpa Arnold.
A dinobaby is not supposed to fraternize with ostriches. These two toed birds can run. It may be time for those cyber security folks who say, “Signal is secure to run away from that broad statement.” Perhaps something like sort of secure if the information presented by the “please, please, please, send us money” newspaper company. (Tip to the Guardian leadership. There are ways to generate revenue some of which I shared in a meeting about a decade ago.)

Listening, verifying, and thinking critically are skills many professionals may want to apply to routine meetings about secure services. Thanks, Venice.ai. Good enough.
The write up from the “please, please, please, donate” outfit is “The FBI Spied on a Signal Group Chat of Immigration Activists, Records Reveal.” The subtitle makes clear that I have to mind the length of my quotes and emphasize that absolutely no one knows about this characteristic of super secret software developed by super quirky professionals working in the not-so-quirky US of A today.
The write up states:
The FBI spied on a private Signal group chat of immigrants’ rights activists who were organizing “courtwatch” efforts in New York City this spring, law enforcement records shared with the Guardian indicate.
How surprised is the Guardian? The article includes this statement, which I interpret as the Guardian’s way of saying, “You Yanks are violating privacy.” Judge for yourself:
Spencer Reynolds, a civil liberties advocate and former senior intelligence counsel with the DHS, said the FBI report was part of a pattern of the US government criminalizing free speech activities.
Several observations are warranted:
- To the cyber security vice president who told me, “Signal is secure.” The Guardian article might say, “Ooops.” When I explained it was not, he made a Three Stooges’ sound and cancel cultured me.
- When appropriate resources are focused on a system created by a human or a couple of humans, that system can be reverse engineered. Did you know Android users can drop content on an iPhone user’s device. What about those how-tos explaining the insecurity of certain locks on YouTube? Yeah. Security.
- Quirky and open source are not enough, and quirky will become less suitable as open source succumbs to corporatism and agentic software automates looking for tricks to gain access. Plus, those after-the-fact “fixes” are usually like putting on a raincoat after the storm. Security enhancement is like going to the closest big box store for some fast drying glue.
One final comment. I gave a lecture about secure messaging a couple of years ago for a US government outfit. One topic was a state of the art messaging service. Although a close hold, a series of patents held by entities in Virginia disclosed some of the important parts of the system and explained in a way lawyers found just wonderful a novel way to avoid Signal-type problems. The technology is in use in some parts of the US government. Better methods for securing messages exist. Open source, cheap, and easy remains popular.
Will I reveal the name of this firm, provide the patent numbers in this blog, and present my diagram showing how the system works? Nope.
PS to the leadership of the Guardian. My recollection is that your colleagues did not know how to listen when I ran down several options for making money online. Your present path may lead to some tense moments at budget review time. Am I right?
Stephen E Arnold, December 4, 2025
First WAP? What Is That? Who Let the Cat Out of the Bag?
October 21, 2025
 This essay is the work of a dumb dinobaby. No smart software required.
This essay is the work of a dumb dinobaby. No smart software required.
Ageing in rural Kentucky is not a good way to keep up with surveillance technology. I did spot a post on LinkedIn. I will provide a url for the LinkedIn post, but I have zero clue if anyone reading this blog will be able to view the information. The focus of the LinkedIn post is that some wizards have taken inspiration from NSO Group-type of firms and done some innovation. Like any surveillance technology, one has to apply it in a real life situation. Sometimes there is a slight difference between demonstrations, PowerPoint talks, and ease of use. But, hey, that’s the MBA-inspired way to riches or at least in NSO Group’s situation, infamy.

Letting the cat out of the bag. Who is the individual? The president, an executive, a conference organizer, or a stealthy “real” journalist. One thing is clear: The cat is out of the bag. Thanks, Venice.ai. Good enough.
The LinkedIn post is from an entity using the handle OSINT Industries. Here is the link, dutifully copied from Microsoft’s outstanding social media platform. Don’t blame me if it doesn’t work. Microsoft just blames users, so just look in the mirror and complain: https://www.linkedin.com/posts/osint-industries_your-phone-is-being-tracked-right-now-ugcPost-7384354091293982721-KQWk?utm_source=share&utm_medium=member_desktop&rcm=ACoAAAACYEwBhJbGkTw7Ad0vyN4RcYKj0Su8NUU
How’s that for a link. ShortURL spit out this version: https://shorturl.at/x2Qx9.
So what’s the big deal. Cyber security outfits and an online information service (in the old days a printed magazine) named Mother Jones learned that an outfit called First WAP exploited the SS7 telecom protocol. As i understand this signal switching, SS7 is about 50 years old and much loved by telephony nerds and Bell heads. The system and method acts like an old fashioned switchyard operator at a rail yard in the 1920s. Signals are filtered from voice channels. Call connections and other housekeeping are pushed to the SS7 digital switchyard. Instead of being located underground in Manhattan, the SS7 system is digital and operates globally. I have heard but have no first hand information about its security vulnerabilities. I know that a couple of companies are associated with switching fancy dancing. Do security exploits work? Well, the hoo-hah about First WAP suggests that SS7 exploitation is available.
The LinkedIn post says that “The scale [is] 14,000+ phone numbers. 160 countries. Over 1 million location pings.
A bit more color appears in the Russian information service ? FrankMedia.ru’s report “First WAP Empire: How Hidden Technology Followed Leaders and Activists.” The article is in Russian, but ever-reliable Google Translate makes short work of one’s language blind spots. Here are some interesting points from Frank Media:
- First WAP has been in business for about 17 or 18 years
- The system was used to track Google and Raytheon professionals
- First WAP relies on resellers of specialized systems and services and does not do too much direct selling. The idea is that the intermediaries are known to the government buyers. A bright engineer from another country is generally viewed as someone who should not be in a meeting with certain government professionals. This is nothing personal, you understand. This is just business.
- The system is named Altamides, which may be a variant of a Greek word for “powerful.”
The big reveal in the Russian write up is that a journalist got into the restricted conference, entered into a conversation with an attendee at the restricted conference, and got information which has put First WAP in the running to be the next NSO Group in terms of PR problems. The Frank Media write up does a fine job of identifying two individuals. One is the owner of the firm and the other is the voluble business development person.
Well, everyone gets 15 minutes of fame. Let me provide some additional, old-person information. First, the company’s Web address is www.1rstwap.com. Second, the firm’s alleged full name is First WAP International DMCC. The “DMCC” acronym means that the firm operates from Dubai’s economic zone. Third, the firm sells through intermediaries; for example, an outfit called KCS operating allegedly from the UK. Companies House information is what might be called sparse.
Several questions:
- How did a non-LE or intel professional get into the conference?
- Why was the company to operate off the radar for more than a decade?
- What benefits does First WAP derive from its nominal base in Indonesia?
- What are the specific security vulnerabilities First WAP exploits?
- Why do the named First WAP executives suddenly start talking after many years of avoiding an NSO-type PR problem?
Carelessness seems to be the reason this First WAP got its wireless access protocol put in the spotlight. Nice work!
To WAP up, you can download the First WAP encrypted messaging application from… wait for it… the Google Play Store. The Google listing includes this statement, “No data shared with third parties.” Think about that statement.
Stephen E Arnold, October 21, 2025
Desperate Much? Buying Cyber Security Software Regularly
September 16, 2025
Bad actors have access to AI, and it is enabling them to increase both speed and volume at an alarming rate. Are cybersecurity teams able to cope? Maybe—if they can implement the latest software quickly enough. VentureBeat reports, “Software Commands 40% of Cybersecurity Budgets ad Gen AI Attacks Execute in Milliseconds.” Citing IBM’s recent Cost of a Data Breach Report, writer Louis Columbus reports 40% of cybersecurity spending now goes to software. Compare that to just 15.8% spent on hardware, 15% on outsourcing, and 29% on personnel. Even so, AI-assisted hacks now attack in milliseconds while the Mean Time to Identify (MTTI) is 181 days. That is quite the disparity. Columbus observes:
“Three converging threats are flipping cybersecurity on its head: what once protected organizations is now working against them. Generative AI (gen AI) is enabling attackers to craft 10,000 personalized phishing emails per minute using scraped LinkedIn profiles and corporate communications. NIST’s 2030 quantum deadline threatens retroactive decryption of $425 billion in currently protected data. Deepfake fraud that surged 3,000% in 2024 now bypasses biometric authentication in 97% of attempts, forcing security leaders to reimagine defensive architectures fundamentally.”
Understandable. But all this scrambling for solutions may now be part of the problem. Some teams, we are told, manage 75 or more security tools. No wonder they capture so much of the budget. Simplification, however, is proving elusive. We learn:
“Security Service Edge (SSE) platforms that promised streamlined convergence now add to the complexity they intended to solve. Meanwhile, standalone risk-rating products flood security operations centers with alerts that lack actionable context, leading analysts to spend 67% of their time on false positives, according to IDC’s Security Operations Study. The operational math doesn’t work. Analysts require 90 seconds to evaluate each alert, but they receive 11,000 alerts daily. Each additional security tool deployed reduces visibility by 12% and increases attacker dwell time by 23 days, as reported in Mandiant’s 2024 M-Trends Report. Complexity itself has become the enterprise’s greatest cybersecurity vulnerability.”
See the writeup for more on efforts to improve cybersecurity’s speed and accuracy and the factors that thwart them. Do we have a crisis yet? Of course not. Marketing tells us cyber security just works. Sort of.
Cynthia Murrell, September 16, 2025
Supermarket Snitches: Old-Time Methods Are Back
September 5, 2025
So much for AI and fancy cyber-security systems. One UK grocery chain has found a more efficient way to deal with petty theft—pay people to rat out others. BBC reports, “Iceland Offers £1 Reward for Reporting Shoplifters.” (Not to be confused with the country, this Iceland is a British supermarket chain.) Business reporter Charlotte Edwards tells us shoplifting is a growing problem for grocery stores and pharmacies. She writes:
“Victims minister Alex Davies-Jones told BBC Radio 4’s Today programme on Monday that shoplifting had ‘got out of hand’ in the UK. … According to the Office for National Statistics, police recorded 530,643 shoplifting offences in the year to March 2025. That is a 20% increase from 444,022 in the previous year, and the highest figure since current recording practices began in 2002-03.”
Amazing what economic uncertainty will do. In response, the government plans to put thousands more police officers on neighborhood patrols by next spring. Perhaps encouraging shoppers to keep their eyes peeled will help. We learn:
“Supermarket chain Iceland will financially reward customers who report incidents of shoplifting, as part of efforts to tackle rising levels of retail theft. The firm’s executive chairman, Richard Walker, said that shoppers who alert staff to a theft in progress will receive a £1 credit on their Iceland Bonus Card. The company estimates that shoplifting costs its business around £20m each year. Mr Walker said this figure not only impacts the company’s bottom line but also limits its ability to reduce prices and reinvest in staff wages. Iceland told the BBC that the shoplifters do not necessarily need to be apprehended for customers to receive the £1 reward but will need to be reported and verified.”
How, exactly, they will be verified is left unexplained. Perhaps that is the role for advanced security systems. Totally worth it. Walker emphasizes customers should not try to apprehend shoplifters, just report them. Surely no one will get that twisted. But with one pound sterling equal to $1.35 USD, we wonder: is that enough incentive to pull the phone out of one’s pocket?
Technology is less effective than snitching.
Cynthia Murrell, September 5, 2025
Cyber Security: Evidence That Performance Is Different from Marketing
August 20, 2025
 This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
In 2022, Google bought a cyber security outfit named Mandiant. The firm had been around since 2004, but when Google floated more than $5 billion for the company, it was time to sell.
If you don’t recall, Google operates a large cloud business and is trying diligently to sell to Microsoft customers in the commercial and government sector. A cyber security outfit would allow Google to argue that it would offer better security for its customers and their users.
Mandiant’s business was threat intelligence. The idea is that Mandiant would monitor forums, the Web, and any other online information about malware and other criminal cyber operations. As an added bonus, Mandiant would blend automated security functions with its technology. Wham, bam! Slam dunk, right?
I read “Google Confirms Major Security Breach After Hackers Linked To ShinyHunters Steal Sensitive Corporate Data, Including Business Contact Information, In Coordinated Cyberattack.” First, a disclaimer. I have no idea if this WCCF Tech story is 100 percent accurate. It could be one of those Microsoft 1,000 Russian programmers are attacking us” plays. On the other hand, it will be fun to assume that some of the information in the cited article is accurate.
With that as background, I noted this passage:
The tech giant has recently confirmed a data breach linked to the ShinyHunters ransomware group, which targeted Google’s corporate Salesforce database systems containing business contact information.
Okay. Google’s security did not work. A cloud customer’s data were compromised. The assertion that Google’s security is better than or equal to Microsoft’s is tough for me to swallow.
Here’s another passage:
As per Google’s Threat Intelligence Group (GTIG), the hackers used a voice phishing technique that involved calling employees while pretending to be members of the internal IT team, in order to have them install an altered version of Salesforce’s Data Loader. By using this technique, the attackers were able to access the database before their intrusion was detected.
A human fooled another human. The automated systems were flummoxed. The breach allegedly took place.
Several observations are warranted:
- This is security until a breach occurs. I am not sure that customers expect this type of “footnote” to their cyber security licensing mumbo jumbo. The idea is that Google should deliver a secure service.
- Mandiant, like other threat intelligence services, allows the customer to assume that the systems and methods generally work. That’s true until they don’t.
- Bad actors have an advantage. Armed with smart software and tools that can emulate my dead grandfather, the humans remain a chink in the otherwise much-hyped armor of an outfit like Google.
What this example, even if only partly accurate, makes it clear than cyber security marketing performs better than the systems some of the firms sell. Consider that the victim was Google. That company has touted its technical superiority for decades. Then Google buys extra security. The combo delivers what? Evidence that believing the cyber security marketing may do little to reduce the vulnerability of an organization. What’s notable is that the missteps were Google’s. Microsoft may enshrine this breach case and mount it on the walls of every cyber security employees’ cubicles.
I can imagine hearing a computer-generated voice emulating Bill Gates’, saying, “It wasn’t us this time.”
Stephen E Arnold, August 20, 2025
Thanks, Google: Scam Link via Your Alert Service
July 20, 2025
 This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
This blog post is the work of an authentic dinobaby. Sorry. No smart software can help this reptilian thinker.
July 20, 2025 at 926 am US Eastern time: The idea of receiving a list of relevant links on a specific topic is a good one. Several services provide me with a stream of sometimes-useful information. My current favorite service is Talkwalker, but I have several others activated. People assume that each service is comprehensive. Nothing is farther from the truth.
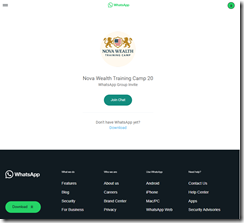
Let’s review a suggested article from my Google Alert received at 907 am US Eastern time.
Imagine the surprise of a person watching via Google Alerts the bound phrase “enterprise search.” Here’s the landing page for this alert. I received this message:
The snippet says “enterprise search platform Shenzhen OCT Happy Valley Tourism Co. Ltd is PRMW a good long term investment [investor sentiment]. What happens when one clicks on Google’s AI-infused message:
My browser displayed this:
If you are not familiar with Telegram Messenger-style scams and malware distribution methods, you may not see these red flags:
- The link points to an article behind the WhatsApp wall
- To view the content, one must install WhatsApp
- The information in Google’s Alert is not relevant to “Nova Wealth Training Camp 20”
This is an example a cross service financial trickery.
Several observations:
- Google’s ability to detect and block scams is evident
- The relevance mechanism which identified a financial scam is based on key word matching; that is, brute force and zero smart anything
- These Google Alerts have been or are now being used to promote either questionable, illegal, or misleading services.
Should an example such as this cause you any concern? Probably not. In my experience, the Google Alerts have become less and less useful. Compared to Talkwalker, Google’s service is in the D to D minus range. Talkwalker is a B plus. Feedly is an A minus. The specialized services for law enforcement and intelligence applications are in the A minus to C range.
No service is perfect. But Google? This is another example of a company with too many services, too few informed and mature managers, and a consulting leadership team disconnected from actual product and service delivery.
Will this change? No, in my opinion.
Stephen E Arnold, July 20, 2025
Sharp Words about US Government Security
May 22, 2025
 No AI. Just a dinobaby who gets revved up with buzzwords and baloney.
No AI. Just a dinobaby who gets revved up with buzzwords and baloney.
On Monday (April 29, 2025), I am headed to the US National Cyber Crime Conference. I am 80, and I don’t do too many “in person” lectures. Heck, I don’t do too many lectures anymore period. A candidate for the rest home or an individual ready for a warehouse for the soon-to-die is a unicorn amidst the 25 to 50 year old cyber fraud, law enforcement professionals, and government investigators.
In my lectures, I steer clear of political topics. This year, I have been assigned a couple of topics which the NCCC organizers know attract a couple of people out of the thousand or so attendees. One topic concerns changes in the Dark Web. Since I wrote “Dark Web Notebook” years ago, my team and I keep track of what’s new and interesting in the world of the Dark Web. This year, I will highlight three or four services which caught our attention. The other topic is my current research project: Telegram. I am not sure how I became interested in this messaging service, but my team and I will will make available to law enforcement, crime analysts, and cyber fraud investigators a monograph modeled on the format we used for the “Dark Web Notebook.”
I am in a security mindset before the conference. I am on the lookout for useful information which I can use as a point of reference or as background information. Despite my age, I want to appear semi competent. Thus, I read “Signalgate Lessons Learned: If Creating a Culture of Security Is the Goal, America Is Screwed.” I think the source publication is British. The author may be an American journalist.
Several points in the write up caught my attention.
First, the write up makes a statement I found interesting:
And even if they are using Signal, which is considered the gold-standard for end-to-end chat encryption, there’s no guarantee their personal devices haven’t been compromised with some sort of super-spyware like Pegasus, which would allow attackers to read the messages once they land on their phones.
I did not know that Signal was “considered the gold standard for end-to-end chat encryption.” I wonder if there are some data to back this up.
Second, is NSO Group’s Pegasus “super spyware.” My information suggests that there are more modern methods. Some link to Israel but others connect to other countries; for example, Spain, the former Czech Republic, and others. I am not sure what “super” means, and the write up does not offer much other than a nebulous adjectival “super spyware.”
Third, these two references are fascinating:
“The Salt Typhoon and Volt Typhoon campaigns out of China demonstrate this ongoing threat to our telecom systems. Circumventing the Pentagon’s security protocol puts sensitive intelligence in jeopardy.”
The authority making the statement is a former US government official who went on to found a cyber security company. There were publicized breaches, and I am not sure comparable to Pegasus type of data exfiltration method. “Insider threats” are different from lousy software from established companies with vulnerabilities as varied as Joseph’s multi-colored coat. An insider, of course, is an individual presumed to be “trusted”; however, that entity provides information for money to an individual who wants to compromise a system, a person who makes an error (honest or otherwise), and victims who fall victim to quite sophisticated malware specifically designed to allow targeted emails designed to obtain information to compromise that person or a system. In fact, the most sophisticated of these “phishing” attack systems are available for about $250 per month for the basic version with higher fees associated with more robust crime as a service vectors of compromise.
The opinion piece seems to focus on a single issue focused on one of the US government’s units. I am okay with that; however, I think a slightly different angle would put the problem and challenge of “security” in a context less focused on ad hominin rhetorical methods.
Stephen E Arnold, May 22, 2025
Banks and Security? Absolutely
April 28, 2025
The second-largest US bank has admitted it failed to recover documents lost to a recent data breach. The Daily Hodl reports, “Bank of America Discloses Data Breach After Customers’ Documents Disappear, Says Names, Addresses, Account Information and Social Security Numbers Affected.” Writer Mark Emem tells us:
“Bank of America says efforts to locate sensitive documents containing personal information on an undisclosed number of customers have failed. The North Carolina-based bank says it is unable to recover the documents, which were lost in transit and ‘resulted in the disclosure’ of personal information. [The bank’s notice states,] ‘According to our records, the information involved in this incident was related to your savings bonds and included your first and last name, address, phone number, Social Security number, and account number…We understand how upsetting this can be and sincerely apologize for this incident and any concerns or inconvenience it may cause. We are notifying you so we can work together to protect your personal and account information.’”
Banks are forthcoming and bad actors know there is money in them. It is no surprise Bank of America faces a challenge. The succinct write-up notes the bank’s pledge to notify affected customers of any suspicious activity on their accounts. It is also offering them a two-year membership to an identity theft protection service. We suggest any Bank of America customers go ahead and change their passwords as a precaution. Now. We will wait.
Cynthia Murrell, April 28, 2025
Hey, We Know This Is Fake News: Sharing Secrets on Signal
April 24, 2025
Some government professionals allegedly blundered when they accidentally shared secret information via Signal with a reporter. The reporter, by the way, is not a person who wears a fedora with a command on it. To some, sharing close-hold information is an oopsie, but doing so with a non-hat wearing reporter is special. The BBC explained what the fallout will be from this mistake: “Why Is It A Problem If Yemen Strike Plans Shared On Signal?”
The Atlantic editor-in-chief Jeffrey Goldberg alleged received close-hold information via a free messaging application. A government professional seemed to agree that the messages appeared to be authentic. Hey, a free application is a cost reducer. Plus, Signal is believed to be encrypted end to end and super secure to boot. Signal is believed to be the “whisper network” of Washington D., an area known for its appropriate behavior and penchant for secrecy. (What was Wilbur Mills doing in the reflecting pool?)
While the messages are encrypted, bad actors (particularly those who may or may not be pals of the United States) allegedly can penetrate the Signal system. The Google Threat Intelligence Group noticed that Russia’s intelligence services have stepped up their hacking activities. Well, maybe or maybe not. Google is the leader in online advertising, but its “cyber security” expertise was acquired and may not be Googley yet.
The US government is not encouraging use of free messaging apps for sensitive information. That’s good. And the Pentagon is not too keen on a system not authorized to transmit non-public Department of Defense information. That’s good to know.
The whole sharing thing presents a potential downside for whomever is responsible for the misstep. The article says:
“Sensitive government communications are required to take place in a sealed-off room called a Sensitive Compartmentalized Information Facility (SCIF), where mobile phones are generally forbidden. The US government has other systems in place to communicate classified information, including the Joint Worldwide Intelligence Communications System (JWICS) and the Secret Internet Protocol Router (SIPR) network, which top government officials can access via specifically configured laptops and phones.”
Will there be consequences?
The article points out that the slip betwixt the cup and the lip may have violated two Federal laws:
“If confirmed, that would raise questions about two federal laws that require the preservation of government records: the Presidential Records Act and the Federal Records Act. "The law requires that electronic messages that take place on a non-official account are preserved, in some fashion, on an official electronic record keeping system," said Jason R Baron, a former director of litigation at the National Archives and Records Administration. Such regulations would cover Signal, he said.”
Hey, wasn’t the National Archive the agent interrupting normal business and holiday activities at a high profile resort residence in Florida recently? What does that outfit know about the best way to share sensitive information?
Whitney Grace, April 24, 2025
Israel Military: An Alleged Lapse via the Cloud
April 23, 2025
 No AI, just a dinobaby watching the world respond to the tech bros.
No AI, just a dinobaby watching the world respond to the tech bros.
Israel is one of the countries producing a range of intelware and policeware products. These have been adopted in a number of countries. Security-related issues involving software and systems in the country are on my radar. I noted the write up “Israeli Air Force Pilots Exposed Classified Information, Including Preparations for Striking Iran.” I do not know if the write up is accurate. My attempts to verify did not produce results which made me confident about the accuracy of the Haaretz article. Based on the write up, the key points seem to be:
- Another security lapse, possibly more severe than that which contributed to the October 2023 matter
- Classified information was uploaded to a cloud service, possibly Click Portal, associated with Microsoft’s Azure and the SharePoint content management system. Haaretz asserts: “… it [MSFT Azure SharePoint Click Portal] enables users to hold video calls and chats, create documents using Office applications, and share files.”
- Documents were possibly scanned using CamScanner, A Chinese mobile app rolled out in 2010. The app is available from the Russian version of the Apple App Store. A CamScanner app is available from the Google Play Store; however, I elected to not download the app.
Modern interfaces can confuse users. Lack of training rigor and dashboards can create a security problem for many users. Thanks, Open AI, good enough.
Haaretz’s story presents this information:
Officials from the IDF’s Information Security Department were always aware of this risk, and require users to sign a statement that they adhere to information security guidelines. This declaration did not prevent some users from ignoring the guidelines. For example, any user could easily find documents uploaded by members of the Air Force’s elite Squadron 69.
Regarding the China-linked CamScanner software, Haaretz offers this information:
… several files that were uploaded to the system had been scanned using CamScanner. These included a duty roster and biannual training schedules, two classified training presentations outlining methods for dealing with enemy weaponry, and even training materials for operating classified weapons systems.
Regarding security procedures, Haaretz states:
According to standard IDF regulations, even discussing classified matters near mobile phones is prohibited, due to concerns about eavesdropping. Scanning such materials using a phone is, all the more so, strictly forbidden…According to the Click Portal usage guidelines, only unclassified files can be uploaded to the system. This is the lowest level of classification, followed by restricted, confidential, secret and top secret classifications.
The military unit involved was allegedly Squadron 69 which could be the General Staff Reconnaissance Unit. The group might be involved in war planning and fighting against the adversaries of Israel. Haaretz asserts that other units’ sensitive information was exposed within the MSFT Azure SharePoint Click Portal system.
Several observations seem to be warranted:
- Overly complicated systems involving multiple products increase the likelihood of access control issues. Either operators are not well trained or the interfaces and options confuse an operator so errors result
- The training of those involved in sensitive information access and handling has to be made more rigorous despite the tendency to “go through the motions” and move on in many professionals undergoing specialized instruction
- The “brand” of Israel’s security systems and procedures has taken another hit with the allegations spelled out by Haaretz. October 2023 and now Squadron 69. This raises the question, “What else is not buttoned up and ready for inspection in the Israel security sector?
Net net: I don’t want to accept this write up as 100 percent accurate. I don’t want to point the finger of blame at any one individual, government entity, or commercial enterprise. But security issues and Microsoft seem to be similar to ham and eggs and peanut butter and jelly from this dinobaby’s point of view.
Stephen E Arnold, April 23, 2025