The Path to Success for AI Startups? Fancy Dancing? Pivots? Twisted Ankles?
October 17, 2023
![Vea4_thumb_thumb_thumb_thumb_thumb_t[2] Vea4_thumb_thumb_thumb_thumb_thumb_t[2]](https://arnoldit.com/wordpress/wp-content/uploads/2023/10/Vea4_thumb_thumb_thumb_thumb_thumb_t2_thumb-13.gif) Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
I read “AI-Enabled SaaS vs Moatless AI.” The buzzwordy title hides a somewhat grim prediction for startups in the AI game.” Viggy Balagopalakrishnan (I love that name Viggy) explains that the best shot at success is:
…the only real way to build a strong moat is to build a fuller product. A company that is focused on just AI copywriting for marketing will always stand the risk of being competed away by a larger marketing tool, like a marketing cloud or a creative generation tool from a platform like Google/Meta. A company building an AI layer on top of a CRM or helpdesk tool is very likely to be mimicked by an incumbent SaaS company. The way to solve for this is by building a fuller product.
My interpretation of this comment is that small or focused AI solutions will find competing with big outfits difficult. Some may be acquired. A few may come up with a magic formula for money. But most will fail.
How does that moat work when an AI innovator’s construction is attacked by energy weapons discharged from massive death stars patrolling the commercial landscape? Thanks, MidJourney. Pretty complicated pointy things on the castle with a moat.
Viggy does not touch upon the failure of regulatory entities to slow the growth of companies that some allege are monopolies. One example is the Microsoft game play. Another is the somewhat accommodating investigation of the Google with its closed sessions and odd stance on certain documents.
There are other big outfits as well, and the main idea is that the ecosystem is not set up for most AI plays to survive with huge predators dominating the commercial jungle. That means clever scripts, trade secrets, and agility may not be sufficient to ensure survival.
What’s Ziggy think? Here’s an X-ray of his perception:
Given that the infrastructure and platform layers are getting reasonably commoditized, the most value driven from AI-fueled productivity is going to be captured by products at the application layer. Particularly in the enterprise products space, I do think a large amount of the value is going to be captured by incumbent SaaS companies, but I’m optimistic that new fuller products with an AI-forward feature set and consequently a meaningful moat will emerge.
How do moats work when Amazon-, Google-, Microsoft-, and Oracle-type outfits just add AI to their commercial products the way the owner of a Ford Bronco installs a lift kit and roof lights?
Productivity? If that means getting rid of humans, I agree. If the term means to Ziggy smarter and more informed decision making? I am not sure. Moats don’t work in the 21st century. Land mines, surprise attacks, drones, and missiles seem to be more effective. Can small firms deal with the likes of Googzilla, the Bezos bulldozer, and legions of Softies? Maybe. Ziggy is an optimist. I am a realist with a touch of radical empiricism, a tasty combo indeed.
Stephen E Arnold, October 17, 2023
Intelware: Some Advanced Technology Is Not So New
October 11, 2023
![Vea4_thumb_thumb_thumb_thumb_thumb_t[2] Vea4_thumb_thumb_thumb_thumb_thumb_t[2]](https://arnoldit.com/wordpress/wp-content/uploads/2023/10/Vea4_thumb_thumb_thumb_thumb_thumb_t2_thumb-8.gif) Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
I read “European Spyware Consortium Supplied Despots and Dictators.” The article is a “report” about intelware vendors. The article in Spiegel International is a “can you believe this” write up. The article identifies a number of companies past and present. Plus individuals are identified.
The hook is technology that facilitates exfiltration of data from mobile devices. Mobile phones are a fashion item and a must have for many people. It does not take much insight to conclude that data on these ubiquitous gizmos can provide potentially high value information. Even better, putting a software module on a mobile device of a person of interest can save time and expense. Modern intelligence gathering techniques are little more than using technology to minimize the need for humans sitting in automobiles or technicians planting listening devices in interesting locations. The other benefits of technology include real time or near real time data acquisition, geo-location data, access to the digital information about callers and email pals, and data available to the mobile’s ever improving cameras and microphones.
The write up points out:
One message, one link, one click. That’s all it takes to lose control of your digital life, unwittingly and in a matter of seconds.
The write up is story focused, probably because a podcast or a streaming video documentary was in the back of the mind of the writers and possibly Spiegel International itself. If you like write ups that have a slant, you will find the cited article interesting.
I want to mentions several facets of the write up which get less attention from “real” journalists.
First, the story of the intelware dates back to the late 1970s. Obviously some of the technology has been around for decades, although refined over time. If this “shady” technology were a problem, why has it persisted, been refined, and pressed into service around the world by many countries? It is tempting to focus on a current activity because it makes a good story, but the context and longevity of some of the systems and methods are interesting to me. But 40 years?
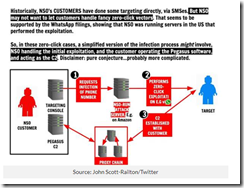
Second, in the late 1970s and the block diagrams I have seen presenting the main features of the Amesys system (i2e Technologies) and its direct descendants have had remarkable robustness. In fact, were one to look at the block diagram for a system provided to a controversial government in North Africa and one of the NSO Group Pegasus block diagrams, the basics are retained. Why? A good engineering solution is useful even thought certain facets of the system are improved with modern technology. What’s this mean? From my point of view, the clever individual or group eager to replicate this type of stealth intelware can do it, just with modern tools and today’s robust cloud environment. The cloud was not a “thing” in 1980, but today it is a Teflon for intelware. This means quicker, faster, better, cheaper, and smarter with each iteration.
Source: IT News in Australia
Third, this particular type of intelware is available from specialized software companies worldwide. Want to buy a version from a developer in Spain? No problem. How about a Chinese variety? Cultivate your contacts in Hong Kong or Singapore and your wish will be granted. What about a version from an firm based in India? No problem, just hang out at telecommunications conference in Mumbai.
Net net: Newer and even more stealthy intelware technologies are available today. Will these be described and stories about the use of them be written? Yep. Will I identify some of these firms? Sure, just attend one of my lectures for law enforcement and intelligence professionals. But the big question is never answered, “Why are these technologies demonstrating such remarkable magnetic appeal?” And a related question, “Why do governments permit these firms to operate?”
Come on, Spiegel International. Write about a more timely approach, not one that is decades old and documented in detail on publicly accessible sources. Oh, is location tracking enabled on your phone to obviate some of the value of Signal, Telegram, and Threema encrypted messaging apps?
PS. Now no clicks are needed. The technology can be deployed when a mobile number is known and connected to a network. There is an exception too. The requisite code can be pre-installed on one’s mobile device. Is that a story? Nah, that cannot be true. I agree.
Stephen E Arnold, October 11, 2023
Getty and Its Licensed Smart Software Art
September 26, 2023
![Vea4_thumb_thumb_thumb_thumb_thumb_t[1] Vea4_thumb_thumb_thumb_thumb_thumb_t[1]](http://arnoldit.com/wordpress/wp-content/uploads/2023/09/Vea4_thumb_thumb_thumb_thumb_thumb_t1_thumb-1.gif) Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid. (Yep, the dinobaby is back from France. Thanks to those who made the trip professionally and personally enjoyable.)
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid. (Yep, the dinobaby is back from France. Thanks to those who made the trip professionally and personally enjoyable.)
The illustration shows a very, very happy image rights troll. The cloud of uncertainty from AI generated images has passed. Now the rights software bots, controlled by cheerful copyright trolls, can scour the Web for unauthorized image use. Forget the humanoids. The action will be from tireless AI generators and equally robust bots designed to charge a fee for the image created by zeros and ones. Yes!
A quite joyful copyright troll displays his killer moves. Thanks, MidJourney. The gradient descent continues, right into the legal eagles’ nests.
“Getty Made an AI Generator That Only Trained on Its Licensed Images” reports:
Generative AI by Getty Images (yes, it’s an unwieldy name) is trained only on the vast Getty Images library, including premium content, giving users full copyright indemnification. This means anyone using the tool and publishing the image it created commercially will be legally protected, promises Getty. Getty worked with Nvidia to use its Edify model, available on Nvidia’s generative AI model library Picasso.
This is exciting. Will the images include a tough-to-discern watermark? Will the images include a license plate, a social security number, or a just a nifty sting of harmless digits?
The article does reveal the money angle:
The company said any photos created with the tool will not be included in the Getty Images and iStock content libraries. Getty will pay creators if it uses their AI-generated image to train the current and future versions of the model. It will share revenues generated from the tool, “allocating both a pro rata share in respect of every file and a share based on traditional licensing revenue.”
Who will be happy? Getty, the trolls, or the designers who have a way to be more productive with a helping hand from the Getty robot? I think the world will be happier because monetization, smart software, and lawyers are a business model with legs… or claws.
Stephen E Arnold, September 26, 2023
Microsoft: Good Enough Just Is Not
September 18, 2023
Was it the Russian hackers? What about the special Chinese department of bad actors? Was it independent criminals eager to impose ransomware on hapless business customers?
No. No. And no.
The manager points his finger at the intern working the graveyard shift and says, “You did this. You are probably worse than those 1,000 Russian hackers orchestrated by the FSB to attack our beloved software. You are a loser.” The intern is embarrassed. Thanks, Mom MJ. You have the hands almost correct… after nine months or so. Gradient descent is your middle name.
“Microsoft Admits Slim Staff and Broken Automation Contributed to Azure Outage” presents an interesting interpretation of another Azure misstep. The report asserts:
Microsoft’s preliminary analysis of an incident that took out its Australia East cloud region last week – and which appears also to have caused trouble for Oracle – attributes the incident in part to insufficient staff numbers on site, slowing recovery efforts.
But not really. The report adds:
The software colossus has blamed the incident on “a utility power sag [that] tripped a subset of the cooling units offline in one datacenter, within one of the Availability Zones.”
Ah, ha. Is the finger of blame like a heat seeking missile. By golly, it will find something like a hair dryer, fireworks at a wedding where such events are customary, or a passenger aircraft. A great high-tech manager will say, “Oops. Not our fault.”
The Register’s write up points out:
But the document [an official explanation of the misstep] also notes that Microsoft had just three of its own people on site on the night of the outage, and admits that was too few.
Yeah. Work from home? Vacay time? Managerial efficiency planning? Whatever.
My view of this unhappy event is:
- Poor managers making bad decisions
- A drive for efficiency instead of a drive toward excellence
- A Microsoft Bob moment.
More exciting Azure events in the future? Probably. More finger pointing? It is a management method, is it not?
Stephen E Arnold, September 18, 2023
Bankrupting a City: Big Software, Complexity, and Human Shortcomings Does the Trick
September 15, 2023
 Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
I have noticed failures in a number of systems. I have no empirical data, just anecdotal observations. In the last few weeks, I have noticed glitches in a local hospital’s computer systems. There have been some fascinating cruise ship problems. And the airlines are flying the flag for system ineptitudes. I would be remiss if I did not mention news reports about “near misses” at airports. A popular food chain has suffered six recalls in a four or five weeks.
Most of these can be traced to software issues. Others are a hot mess combination of inexperienced staff and fouled up enterprise resource planning workflows. None of the issues were a result of smart software. To correct that oversight, let me mention the propensity of driverless automobiles to mis-identify emergency vehicles or possessing some indifference to side street traffic at major intersections.
“The information technology manager looks at the collapsing data center and asks, “Who is responsible for this issue?” No one answers. Those with any sense have adopted the van life, set up stalls to sell crafts at local art fairs, or accepted another job. Thanks, MidJourney. I guarantee your sliding down the gradient descent is accelerating.
What’s up?
My person view is that some people do not know how complex software works but depend on it despite that cloud of unknowing. Other people just trust the marketing people and buy what seems better, faster, and cheaper than an existing system which requires lots of money to keep chugging along.
Now we have an interesting case example that incorporates a number of management and technical issues. Birmingham, England is now bankrupt. The reason? The cost of a new system sucked up the cash. My hunch is that King Charles or some other kind soul will keep the city solvent. But the idea of city going broke because it could not manage a software project is illustrative of the future in my opinion.
“Largest Local Government Body in Europe Goes Under amid Oracle Disaster” reports:
Birmingham City Council, the largest local authority in Europe, has declared itself in financial distress after troubled Oracle project costs ballooned from £20 million to around £100 million ($125.5 million).
An extra £80 million would make little difference to an Apple, Google, or Microsoft. To a city in the UK, the cost is a bit of a problem.
Several observations:
- Large project management expertise does not deliver functional solutions. How is that air traffic control or IRS system enhancement going?
- Vendors rely on marketing to close deals, and then expect engineers to just make the system work. If something is incomplete or not yet coded, the failure rate may be anticipated, right? Nope, what’s anticipated in a scope change and billing more money.
- Government agencies are not known for smooth, efficient technical capabilities. Agencies are good at statements of work which require many interesting and often impossible features. The procurement attorneys cannot spot these issues, but those folks ride herd on the legal lingo. Result? Slips betwixt cup and lip.
Are the names of the companies involved important? Nope. The same situation exists when any enterprise software vendor wins a contract based on a wild and wooly statement of work, managed by individuals who are not particularly adept at keeping complex technical work on time and on target, and when big outfits let outfits sell via PowerPoints and demonstrations, not engineering realities.
Net net: More of these types of cases will be coming down the pike.
Stephen E Arnold, September 15, 2023
New Wave Management or Is It Leaderment?
September 12, 2023
 Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Here’s one of my biases, and I am rather proud of it. I like to word “manager.” According to my linguistics professor Lev Soudek, the word “manage” used to mean trickery and deceit. When I was working at a blue chip consulting firm, the word meant using tactics to achieve a goal. I think of management as applied trickery. The people whom one pays will go along with the program, but not 24×7. In a company which expects 60 hours of work a week the minimum for survival of a Spanish inquisition inspired personnel approach, mental effort had to be expended.
I read “I’m a Senior Leader at Amazon and Have Seen Many Bad Managers. Here Are 3 Reasons Why There Are So Few Great Ones.” The intense, clear-eyed young person explains that he has worked at some outfits which are not among my list of the Top 10 high-technology outfits. His résumé includes eBay (a digital yard sale), a game retailer, and the somewhat capricious Amazon (are we a retail outfit, are we a cloud outfit, are we a government services company, are we a data broker, are we a streaming company, etc.).
A modern practitioner of leaderment is having trouble getting the employees to fall in, throw their shoulders back, and mark in step to the cadence of Am-a-zon, Am-a-zon like a squad of French Foreign Legion troops on Bastille Day. Thanks, MidJourney. The illustration did not warrant a red alert, but it is also disappointing.
I assume that these credentials are sufficient to qualify for a management guru. Here are the three reasons managers are less than outstanding.
First, managers just sort of happen. Few people decide to be a manager. Ah, serendipity or just luck.
Second, managers don’t lead. (Huh, the word is “management”, not “leaderment.”)
Third, pressure for results means some managers are “sacrificing employee growth.” (I am not sure what this statement means. If one does not achieve results, then that individual and maybe his direct reports, the staff he leaderments, and his boss will be given an opportunity to find their future elsewhere. Translation for the GenZ reader: You are fired.
Let’s step back and think about these insights. My initial reaction is that a significant re-languaging has taken place in the write up. A good manager does not have to be a leader. In fact, when I was a guest lecturer at the Kansai Institute of Technology, I met a number of respected Japanese managers. I suppose some were leaders, but a number made it clear that results were number one or ichiban.
In my work career, confusing to manage with to lead would create some confusion. I recall when I was working in the US Congress with a retired admiral who was elected to represent an upscale LA district, the way life worked was simple: The retired admiral issued orders. Lesser entities like myself figured out how to execute, tapped appropriate resources, and got the job done. There was not much leadership required of me. I organized; I paid people money; and I hassled everyone until the retired admiral grunted in a happy way. There was no leaderment for me. The retired admiral said, “I want this in two days.” There was not much time for leaderment.
I listened to a podcast called GeekWire. The September 2, 2023, program made it clear that the current big dog at Amazon wants people to work in the office. If not, these folks are going to go away. What makes this interesting is that the GeekWire pundits pointed out that the Big Dog had changed his story, guidelines, and procedures for this work from home and work from office approach multiple times.
Therefore, I am not sure if there is management or leaderment at the world’s largest digital mall. I do know that modern leaderment is not for me. The old-fashioned meaning of manage seems okay to me.
Stephen E Arnold, September 12, 2023
Google: An Ad Crisis Looms from the Cancer of Short Videos
September 7, 2023
The weird orange newspaper ran a story which I found important. To read the article, you will need to pony up cash; I suggest you consider doing that. I want to highlight a couple of key points in the news story and offer a couple of observations.
An online advertising expert looks out his hospital window and asks, “I wonder if the cancer in my liver will be cured before the cancer is removed from my employer’s corporate body?” The answer may be, “Liver cancer can be has a five year survival rate between 13 to 43 percent (give or take a few percentage points).” Will the patient get back to Foosball and off-site meetings? Is that computer capable of displaying TikTok videos? Thanks, Mother MJ. No annoying red appeal this banners today.
The article “Shorts Risks Cannibalising Core YouTube Business, Say Senior Staff” contains an interesting (although one must take with a dollop of mustard and some Dead Sea salt):
Recent YouTube strategy meetings have discussed the risk that long-form videos, which produce more revenue for the company, are “dying out” as a format, according to these people.
I am suspicious of quotes from “these people.” Nevertheless, let’s assume that the concern at the Google is real like news from “these people.”
The idea is that Google has been asleep at the switch as TikTok (the China linked short video service) became a go-to destination for people seeking information. Yep, some young people search TikTok for information, not just tips on self-harm and body dysmorphia. Google’s reaction was slow and predictable: Me too me too me too. Thus, Google rolled out “Shorts,” a TikTok clone and began pushing it to its YouTube faithful.
The party was rolling along until “these people” sat down and looked at viewing time for longer videos and the ad revenue from shorter videos. Another red alert siren began spinning up.
The orange newspaper story asserted:
In October last year, YouTube reported its first-ever quarterly decline in ad revenue since the company started giving its performance separately in 2020. In the following two quarters, the platform reported further falls compared with the same periods the previous year.
With a decline in longer videos, the Google cannot insert as many ads. If people watch shorter videos, Google has reduced ad opportunities. Although Google would love to pump ads into 30 second videos, viewers (users) might decide to feed their habit elsewhere. And where one may ask? How about TikTok or the would be cage fighter’s Meta service?
Several observations:
- Any decline in ad revenue is a force multiplier at the Google. The costs of running the outfit are difficult to control. Google has not been the best outfit in the world in creating new, non ad revenue streams in the last 25 years. That original pay-to-play inspiration has had legs, but with age, knees and hips wear out. Googzilla is not as spry as it used to be and its bright idea department has not found sustainable new revenue able to make up for a decline in traditional Google ad revenue… yet.
- The cost of video is tough to weasel out of Google’s financial statements. The murky “cloud” makes it easy to shift some costs to the enabler of the magical artificial intelligence push at the company. In reality, video is a black hole of costs. Storage, bandwidth, legal compliance, creator hassles, and overhead translate to more ads. Long videos are one place to put ads every few minutes. But when the videos are short like those cutting shapes dance lessons, the “short” is a killer proposition.
- YouTube is a big deal. Depending on whose silly traffic estimates one believes, YouTube is as big a fish in terms of eyeballs as Google.com search. Google search is under fire from numerous directions. Prabhakar Raghavan has not mounted much of a defense to the criticisms directed at Google search’s genuine inability to deliver relevant search results. Now the YouTube ad money flow is drying up like streams near Moab.
Net net: YouTube has become a golden goose. But short videos are a cancer and who can make fois gras out of a cancerous liver?
Stephen E Arnold, September 7, 2023
Search: The Moonshot for Alphabet Google YouTube Etc. May Be Off by Miles
September 6, 2023
 Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Google is now 25. Yep, a quarter century. If you want to read a revisionist history of the beloved firm, point your Chrome browser (yep, it is part of the alleged monopoly) at “Questions, Shrugs and What Comes Next: A Quarter Century of Change.” The cited article appears in the Google blog (does anyone remember Blogger or what about the Google blog search?). The idea is that Sundar Pichai logged into a Google workspace (yep, that’s the software system intended to deal Microsoft a mortal blow).
I just wanted to hire a normal clown. It was not possible. The clown search became a monster. Let’s have fun! Thanks, MidJourney, you old gradient descent entity.
What does Mr. Pichai write, allegedly without the assistance of other Googlers, advisors, and legal eagles?
One of this statements is:
Search is still at the core of our mission, and it’s still our biggest moonshot with so much more to do.
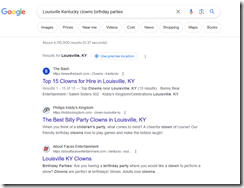
Okay, I want to stop there. I wanted to find a service in Louisville, Kentucky, that sends clowns to birthday parties. Pretty simple, right. I entered the query “Louisville Kentucky clowns birthday parties.” I expected to see a list of people or companies in the clown rental business. Wrong? I received this output from the “biggest moonshot” outfit:
The top hit was to The Bash, a service which lists clowns. That link pointed me to Bunny Bear Entertainment and Salem Sisters 502. No phone number, just a link to get a free quote. Okay, that looks good. Click on the link and what happens? A form appears and someone will contact me. Yeah, I wanted to talk to a person.
The second hit was to Phillips (presenting itself as kiddyskingdom.com) at a toll free number. Same deal. A referral service. No, I could not talk to a human in Louisville.
The third hit was to About Faces. Yep, another SEO-ized reseller of clown services. No phone number for me to call to talk to a real live clown.
Several observations:
- Google search (the moonshot) is not useful. It creates work; it does not provide what I wanted.
- Google’s business is selling ads which are funding Google Cloud ambitions to break out of the one-trick-pony pejorative aimed at the company by the Softie Steve Ballmer a long time ago.
- The blog post is a marketing pitch for Google’s smart software.
Net net: Vintage Google operating without regard to regulatory scrutiny, allegations that the company is a monopoly, or managing people in a way that is what I hoped the clown company would provide to me: Laughs.
A “healthy disregard for the impossible.” Sure. I trust Google. I believe the Google. But delivering on point search results. I don’t need a clown for that. I have one.
Stephen E Arnold, September 6, 2023
Amazon Offers AI-Powered Review Consolidation for Busy Shoppers
September 6, 2023
I read the reviews for a product. I bought the product. Reality was — how shall I frame it — different from the word pictures. Trust those reviews. ? Hmmm. So far, Amazon’s generative AI focus has been on supplying services to developers on its AWS platform. Now, reports ABC News, “Amazon Is Rolling Out a Generative AI Feature that Summarizes Product Reviews.” Writer Haleluya Hadero tells us:
“The feature, which the company began testing earlier this year, is designed to help shoppers determine at a glance what other customers said about a product before they spend time reading through individual reviews. It will pick out common themes and summarize them in a short paragraph on the product detail page.”
A few mobile shoppers have early access to the algorithmic summaries while Amazon tweaks the tool with user feedback. Eventually, the company said, shoppers will be able to surface common themes in reviews. Sounds nifty, but there is one problem: Consolidating reviews that are fake, generated by paid shills, or just plain wrong does nothing to improve their accuracy. But Amazon is more eager to jump on the AI bandwagon than to perform quality control on its reviews system. We learn:
“The Seattle-based company has been looking for ways to integrate more artificial intelligence into its product offerings as the generative AI race heats up among tech companies. Amazon hasn’t released its own high-profile AI chatbot or imaging tool. Instead, it’s been focusing on services that will allow developers to build their own generative AI tools on its cloud infrastructure AWS. Earlier this year, Amazon CEO Andy Jassy said in his letter to shareholders that generative AI will be a ‘big deal’ for the company. He also said during an earnings call with investors last week that ‘every single one’ of Amazon’s businesses currently has multiple generative AI initiatives underway, including its devices unit, which works on products like the voice assistant Alexa.”
Perhaps one day Alexa will recite custom poetry or paint family portraits for us based on the eavesdropping she’s done over the years. Heartwarming. One day, sure.
Cynthia Murrell, September 19, 2023
Google: Trapped in Its Own Walled Garden with Lots of Science Club Alums
August 30, 2023
 Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
I read “MapReduce, TensorFlow, Vertex: Google’s Bet to Avoid Repeating History in AI.” I found the idea that Google gets in its own way a retelling of how high school science club management produces interesting consequences.
A young technology wizard finds himself in a Hall of Mirrors at the carnival. He is not sure what is real or in which direction to go. The world of the House of Mirrors is disorienting. The young luminary wants to return to the walled garden where life is more comfortable. Thanks, MidJourney. Four tries and I get this tired illustration. Gradient descent time?
The write up asserts:
Google is in the middle of trying to avoid repeating history when releasing its industry-altering technology.
I disagree. The methods defining Google produce with remarkable consistency a lack of informed control. The idea is that organizations have a culture. That cultural evolves over time, but it remains anchored in its past. Thus, as the organization appears to move forward in time, that organization behaves in a predictable way; for example, Google has an approach to management which guarantees friction. Examples range from the staff protests to the lateral arabesque used to move Dr. Jeff Dean out of the way of the DeepMind contingent.
The write up takes a different view; for example:
Run by engineers, the [Google MapReduce] team essentially did not foresee the coming wave of open-source technology to power the modern Web and the companies that would come to commercialize it.
Google lacks the ability to perceive its opportunities. The company is fenced by its dependence on online advertising. Thus, innovations are tough for the Googlers to put into perspective. One reason is the high school science club ethos of the outfit; the other is that the outside world is as foreign to many Googlers as the world beyond the goldfish’s bowl filled with water. The view is distorted, surreal, and unfamiliar.
How can a company innovate and make a commercially viable product with this in its walled garden? It cannot. Advertising at Google is a me-too product for which Google prior to its IPO settled a dispute with Yahoo over the “inspiration” for pay-to-play search. The cost of this “inspiration” was about $1 billion.
In a quarter century, Google remains what one Microsoftie called “a one-trick pony.” Will the Google Cloud emerge as a true innovation? Nope. There are lots of clouds. Google is the Enterprise Rent-a-Car to the Hertz and Avis cloud rental firms. Google’s innovation track record is closer to a high school science club which has been able to win the state science club content year after year. Other innovators win the National Science Club Award (once called the Westinghouse Award). The context-free innovations are useful to others who have more agility and market instinct.
My view is that Google has become predictable, lurching from one technical paper to legal battle like a sine wave in a Physics 101 class; that is, a continuous wave with a smooth periodic function.
Don’t get me wrong. Google is an important company. What is often overlooked is the cultural wall that keeps the 100,000 smartest people in the world locked down in the garden. Innovation is constrained, and the excitement exists off the virtual campus. Why do so many Xooglers innovate and create interesting things once freed from the walled garden? Culture has strengths and weaknesses. Google’s muffing the bunny, as the article points out, is one defining characteristic of a company which longs for high school science club meetings and competitions with those like themselves.
Tony Bennett won’t be singing in the main cafeteria any longer, but the Googlers don’t care. He was an outsider, interesting but not in the science club. If the thought process doesn’t fit, you must quit.
Stephen E Arnold, August 30. 2023