Exploit Checklist for Bad Actors
July 28, 2021
I found this post my MIT Research (oops, sorry, I meant MITRE Research. The information in “2021 CWE Top 25 Most Dangerous Software Weaknesses” is fascinating. It provides hot links to details in a public facing encyclopedia called Common Weakness Enumeration. The link is to additional information about the Out-of-Bounds Write” weak point. The Top 25 is a helpful reference for good actors as well as bad actors. The MITRE team provides this preface to the list:
The 2021 Common Weakness Enumeration (CWE™) Top 25 Most Dangerous Software Weaknesses (CWE Top 25) is a demonstrative list of the most common and impactful issues experienced over the previous two calendar years. These weaknesses are dangerous because they are often easy to find, exploit, and can allow adversaries to completely take over a system, steal data, or prevent an application from working. The CWE Top 25 is a valuable community resource that can help developers, testers, and users — as well as project managers, security researchers, and educators — provide insight into the most severe and current security weaknesses. To create the 2021 list, the CWE Team leveraged Common Vulnerabilities and Exposures (CVE®) data found within the National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD), as well as the Common Vulnerability Scoring System (CVSS) scores associated with each CVE record. A formula was applied to the data to score each weakness based on prevalence and severity.
Popular weaknesses, the equivalent of a 1960s AM radio station’s “Fast Mover Tunes” are:
- CWE-276 (Incorrect Default Permissions): from #41 to #19
- CWE-306 (Missing Authentication for Critical Function): from #24 to #11
- CWE-502 (Deserialization of Untrusted Data): from #21 to #13
- CWE-862 (Missing Authorization): from #25 to #18
- CWE-77 (Improper Neutralization of Special Elements used in a Command (‘Command Injection’)): from #31 to #25
New entries are:
- CWE-276 (Incorrect Default Permissions): from #41 to #19
- CWE-918 (Server-Side Request Forgery (SSRF)): from #27 to #24
- CWE-77 (Improper Neutralization of Special Elements used in a Command (‘Command Injection’)): from #31 to #25
A few minutes spent with this list can be instructive. The write up includes a list of weaknesses which one might want to know about.
Net net: Who will find this list more inspirational: Marketing oriented cyber threat vendors or bad actors working under the protection of nation states hostile to US interests?
Stephen E Arnold, July 28, 2021
Search Atlas Demonstrates Google Search Bias by Location
July 28, 2021
An article at Wired reminds us that Google Search is not the objective source of information it appears to many users. We learn that “A New Tool Shows How Google Results Vary Around the World.” Researchers and PhD students Rodrigo Ochigame of MIT and Katherine Ye of Carnegie Mellon University created Search Atlas, an experimental Google Search interface. The tool displays three different sets of results to the same query based on location and language, illustrating both cultural differences and government preferences. “Information borders,” they call it.
The first example involves image searches for “Tiananmen Square.” Users in the UK and Singapore are shown pictures of the government’s crackdown on student protests in 1989. Those in China, or elsewhere using the Chinese language setting, see pretty photos of a popular tourist destination. Google says the difference has nothing to do with censorship—they officially stopped cooperating with the Chinese government on that in 2010, after all. It is just a matter of localized results for those deemed likely to be planning a trip. Sure. Writer Tom Simonite describes more of the tool’s results:
“The Search Atlas collaborators also built maps and visualizations showing how search results can differ around the globe. One shows how searching for images of ‘God’ yields bearded Christian imagery in Europe and the Americas, images of Buddha in some Asian countries, and Arabic script for Allah in the Persian Gulf and northeast Africa. The Google spokesperson said the results reflect how its translation service converts the English term ‘God’ into words with more specific meanings for some languages, such as Allah in Arabic. Other information borders charted by the researchers don’t map straightforwardly onto national or language boundaries. Results for ‘how to combat climate change’ tend to divide island nations and countries on continents. In European countries such as Germany, the most common words in Google’s results related to policy measures such as energy conservation and international accords; for islands such as Mauritius and the Philippines, results were more likely to cite the enormity and immediacy of the threat of a changing climate, or harms such as sea level rise.”
Search Atlas is not yet widely available, but the researchers are examining ways to make it so. They presented it at last month’s Designing Interactive Systems conference and are testing a private beta. Of course, the tool cannot reveal the inner workings of Google’s closely held algorithms. It does, however, illustrate the outsized power the company has over who can access what information. As co-creator Ye observes:
“People ask search engines things they would never ask a person, and the things they happen to see in Google’s results can change their lives. It could be ‘How do I get an abortion?’ restaurants near you, or how you vote, or get a vaccine.”
The researchers point to Safiya Noble’s 2018 book “Algorithms of Oppression” as an inspiration for their work. They hope their project will bring the biased nature of search algorithms to the attention of a broader audience.
Cynthia Murrell, July 28, 2021
Google: API Promise, Circa 2021
July 27, 2021
If you are not familiar with “Google Data APIs Client Library (1.41.1),” it is worth a look. You will notice that there is a table of contents to:
- Deprecated Interfaces
- Deprecated Classes
- Deprecated Fields
- Deprecated Methods
- Deprecated Constructors
- Deprecated Enum Constants
An industrious online search wizard can locate other APIs consigned to the Google bit bin; for example, Transformics’ contributions and the much-loved Orkut (loved at least by some innovating individuals in Brazil and a handful of lawyers).
Fresh from this walk down API Memory Lane, navigate to “How Google Cloud Plans to Kill Its ‘Killed By Google’ Reputation.” The write up reports:
Under the new Google Enterprise APIs policy, the company is making a promise that its services will remain available and stable far into the future….The announcement is clear recognition of widespread feedback from Google Cloud customers and outright derision in several corners of the internet regarding Google’s historic reputation for ending support for its APIs without sufficient notice or foresight. The canonical example was probably the company’s decision to shutter Google Reader in 2013 with just a couple of months’ notice, which led to a torrent of criticism that persists today.
Google doesn’t want to leave any customer behind. How did that type of assertion work out for “No Child Left Behind”?
The “new” Google wants to be the “real” Google. That’s going to be a hill to climb with the Bezos bulldozer reworking the cloud landscape and Microsoft (the all time champion of great security) leveraging the brilliant individuals trying to use Excel and Word.
Yasmine El Rashidi allegedly said:
When you have a dream and someone makes promises they keep breaking, it is hard to recover. You lose hope.
What’s this mean for the ad supported Google? Will you promise to give a honest answer and provide factual back up? Yikes, your proof was in disappeared photos on a deprecated Google service. Thus, whatever you wish to say is meaningless at this time. Maybe there is a copy on Google’s never forget subsystem?
Stephen E Arnold, July 27, 2021
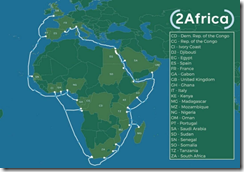
China: Making Technology into a Friend Magnet in Africa
July 27, 2021
I don’t know much about Africa. I remember studying about Belgium’s wonderful and humane approach, but China has found technology more agreeable than Léopold II’s tactics. “Chinese Tech, Ignored by the West, Is Taking over Africa’s Cyberspace” reports:
While China’s telecom giant Huawei has come under increasing attack in the US and the European Union, it is thriving in Africa…
The drive to lure people comes as Huawei faces mounting attacks from the West. But in Africa, the company has a solid base. Currently, Huawei is active in most African countries. According to an Atlantic Council study – “The Digital Infrastructure Imperative in African Markets,” – around 50 percent of Africa’s 3G networks and 70 percent of its 4G networks are built by Huawei.
What’s Huawei’s secret sauce? The article quotes an expert who asserts:
“Huawei has a big competitive advantage because it’s got access to state capital,” says Eric Olander, managing editor of The China Africa Project, a portal that monitors Chinese business ventures across the continent.
What’s that “state capital” enable? Check out this map. The white line is cable which surrounds the African continent. Sixteen major nodes are planned. The 5G system will connect hundreds of millions of people.
Maybe the Google Loon balloons will be given another shot at the Internet connectivity the online ad company deployed in Puerto Rico. Facebook had model airplane-type devices. And Elon Musk has nifty satellite things. But for now, Huawei is having its way with 5G, the Internet connectivity, and capturing a growing market for devices and services.
Stephen E Arnold, July 27, 2021
Can Big Clouds Squeeze Tiny Clouds?
July 27, 2021
I think that big clouds absorb or push smaller clouds out of the way. More accurately, the forces allowing clouds to grow are money, customers, and a desire to be the biggest, most capable cloud in the sky. Agree or not, the decimation of Rackspace suggests that being a mid tier cloud providers is a difficult slot to make work. To get the details on the outfit which once hired the surprising Robert Scoble as an evangelist, navigate to “Rackspace Cuts 10% Of Workforce In One Of Largest Employee Shake-Ups.” The write up states:
The company announced one of the largest layoff rounds in company history today, as it will terminate about 10% of its workforce over the next 12 months, according to a filing with the U.S. Securities and Exchange Commission Thursday (July 22, 2021). The company says it will “backfill” or absorb about 85% of the roles to its offshore service centers, likely a cost-cutting measure. It doesn’t list where those roles will go specifically. The company did partner with Tech Mahindra — an India-based firm — in 2019.
From my vantage point in Harrod’s Creek, this appears to be an IBM-type play. The expensive US workforce can go away after some of the soon-to-be-RIFfed train their lower cost replacement. Yep, MBA and bean counter infused efficiency.
What the story does not address is why. There may be a very small clue in Cloudflare’s blog post “AWS’s Egregious Egress.” The idea is that Amazon AWS makes it easy to enter the nifty AWS Hotel and its walled garden. In fact, getting a room doesn’t cost much at all. However, once in the walled garden, one finds small bladderworts, pitcher plants, sundews, and the venus flytrap. There are some critters basking in the warmth of the AWS servers too. I thought I spotted the technical equivalent of the inland taipan, a couple of king cobras (you know, the ones with the cool cowls), and a family of banded kraits. To get out of the walled garden, there is a modest fee charged. This is similar to the exit visa sold to some departing travelers to the wonderful and exotic Zimbabwe.
This pay-to-leave is described in the Egregious Egress write up. I continue to believe everything I read on the Internet, so let’s assume that the information is spot on. I learned:
To sum up, it costs a lot to leave AWS. The write up points out:
During the last ten years, industry wholesale transit prices have fallen an average of 23% annually. Compounded over that time, wholesale bandwidth is 93% less expensive than 10 years ago. However, AWS’s egress fees over that same period have fallen by only 25%. And, since 2018, the egress fees AWS charges in North America and Europe have not dropped a penny even as wholesale prices in those markets over the same time period have fallen by more than half.
The article suggests that the approach is like a Hotel California. (I was disappointed that the author did not seize upon what is called a roach trap.) The insect cannot get out at least easily and may leave a leg behind as a memento:
The article ends with an appeal to Amazon AWS:
We remain hopeful that AWS will do the right thing, lower their egress fees, join the Bandwidth Alliance — following the lead of the majority of the rest of the hosting industry — and pass along savings from peering with Cloudflare and other networks to all their customers.
To sum up, Amazon’s market presence and its pricing power may be sparking the Rackspace terminations. Will other cloud providers, like those in the Bandwidth Alliance, be thinking about similar actions or hoping that the US government will view Amazon as a 2021 manifestation of the pre Judge Green AT&T? My suggestion is to ask a retired Bell head about those similarities.
Stephen E Arnold, July 28, 2021
NSO Group: Investigative Reporters Are Investigating
July 27, 2021
What happens when one puts a family of beavers (the furry animals once prized for hats) in what remains of the Chrysler Building in Midtown? Well, those beavers will try to build a dam. What do investigative reporters do from more than a dozen newspapers enthralled by the NSO Group intelware story? The answer, gentle reader, is investigate.
What’s been made public in the last few days?
There were a handful of data nuggets I found mildly interesting; for example:
- The very wonderful UK Daily Mail reported that NSO Group “spent millions of dollars on Washington lobbyists, consultants, and lawyers, as it tried to sell its Pegasus spyware to the US government.” One name disclosed in the article was Tom Ridge, the first secretary of homeland security. The estimable Daily Mail notes that the Washington Post knew this factoid too. The Daily Mail added, that NSO Group retained “The Who’s Who of government figures runs through at least three administrations.” The money flowed from OSY Technologies and Francisco Partners, which once owned NSO Group.
- Mashable published “QAnon Believers Don’t Know How to Handle Michael Flynn’s Ties to Spyware Firm Behind Pegasus.” In addition to the QAnon trigger word, the Mashable story noted, “Edward Snowden is call it [Pegasus] the story of the year.” Mashable reported: “Many QAnon followers still don’t exactly know what to make of the news. Some seemed to accept the idea that this “doesn’t look good” for Flynn.”
- Axios (via Yahoo News) reported that Francisco Partners “…The firm finally exited NSO in early 2019, selling it back to the [NSO Group] company’s founders and London-based private equity firm Novalpina, which pledged “a new model for public transparency. Since then, NSO has become the pulsing heart of a dispute between the partners of Novalpina. And, in an ironic twist, it involves leaked WhatsApp messages and a lawsuit against one of the newspapers that later became part of the Pegasus consortium.”
My hunch is that the investigative reporters will continue just like the hypothetical beavers. Beavers were skinned by intrepid traders. Will the investigative reporters find themselves in a similar business process? Flipping stones with the NSO Group logo stenciled on them may reveal some surprises.
Stephen E Arnold, July 27, 2021
DarkCyber for July 27, 2021: NSO Group Again, Making AWS Bots, How Bad Actors Scale, and Tethered Drones
July 27, 2021
The 15th DarkCyber for 2021 addresses some of the NSO Group’s market position. With more than a dozen news organizations digging into who does what with the Pegasus intelware system, the Israeli company has become the face of what some have called the spyware industry. In this program, Stephen E Arnold, author of the Dark Web Notebook, explains how bad actors scale their cyber crime operations. One thousand engineers is an estimate which is at odds with how these cyber groups and units operate. What’s the technique? Tune in to learn why Silicon Valley provided the road map for global cyber attacks. If you are curious, you can build your own software robot to perform interesting actions using the Amazon AWS system as a launch pad. The final story explains that innovation in policing can arrive from the distant pass. An 18th century idea may be the next big thing in law enforcement’s use of drones. DarkCyber is produced by Stephen E Arnold, who publishes Beyond Search. You can access the blog at www.arnoldit.com/wordpress and view the DarkCyber video at this link.
Kenny Toth, July 27, 2021
Why Some Outputs from Smart Software Are Wonky
July 26, 2021
Some models work like a champ. Utility rate models are reasonably reliable. When it is hot, use of electricity goes up. Rates are then “adjusted.” Perfect. Other models are less solid; for example, Bayesian systems which are not checked every hour or large neural nets which are “assumed” to be honking along like a well-ordered flight of geese. Why do I offer such Negative Ned observations? Experience for one thing and the nifty little concepts tossed out by Ben Kuhn, a Twitter persona. You can locate this string of observations at this link. Well, you could as of July 26, 2021, at 630 am US Eastern time. Here’s a selection of what are apparently the highlights of Mr. Kuhn’s conversation with “a former roommate.” That’s provenance enough for me.
Item One:
Most big number theory results are apparently 50-100 page papers where deeply understanding them is ~as hard as a semester-long course. Because of this, ~nobody has time to understand all the results they use—instead they “black-box” many of them without deeply understanding.
Could this be true? How could newly minted, be an expert with our $40 online course, create professionals who use models packaged in downloadable and easy to plug in modules be unfamiliar with the inner workings of said bundles of brilliance? Impossible? Really?
Item Two:
A lot of number theory is figuring out how to stitch together many different such black boxes to get some new big result. Roommate described this as “flailing around” but also highly effective and endorsed my analogy to copy-pasting code from many different Stack Overflow answers.
Oh, come on. Flailing around. Do developers flail or do they “trust” the outfits who pretend to know how some multi-layered systems work. Fiddling with assumptions, thresholds, and (close your ears) the data themselves are never, ever a way to work around a glitch.
Item Three
Roommate told a story of using a technique to calculate a number and having a high-powered prof go “wow, I didn’t know you could actually do that”
No kidding? That’s impossible in general, and that expression would never be uttered at Amazon-, Facebook-, and Google-type operations, would it?
Will Mr. Kuhn be banned for heresy. [Keep in mind how Wikipedia defines this term: “is any belief or theory that is strongly at variance with established beliefs or customs, in particular the accepted beliefs of a church or religious organization.”] Just repeating an idea once would warrant a close encounter with an Iron Maiden or a pile of firewood. Probably not today. Someone might emit a slightly critical tweet, however.
Stephen E Arnold, July 26, 2021
YouTube: Serving Consumers or Bullying?
July 26, 2021
Ycombinator included a comment from someone. That comment was flagged. However, the information in the original comment and the observations offered by Ycombinator users are interesting. The information reveals what I characterize as an escalating battle between those who view YouTube videos and YouTube itself. (I am not going to discuss the escalating tension between “creators,” YouTube, and the service Odysee.com.)
First, the Ycombinator item contains this statement:
YouTube is still not happy. Today when I opened the app on my phone, it still showed me an add. It is infuriating at least. This won’t probably make it, but I needed to share. https://imgur.com/a/BM7XoTe
So what? The flagged poster subscribed to YouTube and YouTube still displays advertisements.
Second, the comments include the tools which one can use to block YouTube’s charming and highly relevant, on point, information packed advertisements; for example:
Adguard
Arachnoid
Cercube
Invidious
SmartTube
Sponsorblock
uBlock Origin
Vanced
Third, the fact that YouTube is becoming a cable-tv like operation is interesting as well.
Net net: Do you hear that tick tock? Maybe it is spelled TikTok?
Stephen E Arnold, July 26, 2021
Putin Has Kill Switch
July 26, 2021
“Russia Disconnected Itself from the Global Internet in Tests” shares an intriguing factoid. Mr. Putin can disconnected the country from the potato fields near Estonia to the fecund lands where gulags once bloomed. The write up reports:
State communications regulator Roskomnadzor said the tests were aimed at improving the integrity, stability and security of Russia’s Internet infrastructure…
If a pesky cyber gang shuts down the Moscow subway from Lichtenstein, it’s pull the plug time. The idea is that Russia will not have to look outside of its territory to locate the malefactors. If outfits like Twitter refuse to conform to Russian law, the socially responsible company may lose some of its Russian content creators.
What other countries will be interested in emulating Russia’s action or licensing the technology? I can think of a few. The Splinter Net is starting to gain momentum. Those ideals about information wanting to be free and the value of distributed systems seem out of step with Mr. Putin’s kill switch.
Stephen E Arnold, July 26, 2021