Tech Giants: Are There Reasons for Complaining about Tiny Component Vendors?
February 8, 2022
I read “Tiny chips, Big Headaches.” The write up is interesting and it comes at a time which follows [a] record earnings and [b] before the anti-trust cowboys begin their roundup. I found this paragraph notable:
But there is growing anxiety that as cloud-computing networks have become larger and more complex, they are still dependent, at the most basic level, on computer chips that are now less reliable and, in some cases, less predictable. In the past year, researchers at both Facebook and Google have published studies describing computer hardware failures whose causes have not been easy to identify. The problem, they argued, was not in the software — it was somewhere in the computer hardware made by various companies.
The write up concludes that fixes are “a little bit like changing an engine while an airplane is still flying.” This statement is attributed too Gary Smerdon, a wizard at TidalScale.
Let’s step back.
The alleged technology monopolies are eager to cement their market dominance. One way to do this is to become like AMD: Smart people paying other people to fabricate their silicon and assemble their gizmos. It stands to reason that really smart people like those at the tech giants want to gain control and be like Apple. Apple went its own direction and seems to have a lucrative allegedly monopoly and some fascinating deals with people like a certain online advertising outfit for search.
What’s the argument for becoming more like Henry Ford’s River Rouge operation. That’s the one that ingested iron ore at one end of the facility and output automobiles at the other end. Today the raw material is user clicks and the outputs are monetization of messages to the users or the crafting of subscription services that are tough to resist.
My take on the reasons for pointing the finger at third parties is more of the shifting blame. This method was evident when Mr. Zuckerberg said Apple’s “privacy” policy created some headwinds. Sure, the Zuckbook has other headwinds, but the point is that it is useful to focus blame elsewhere.
However, the write up advances a point which I found interesting. Here is the passage from the write up I noted:
In the past year, researchers at both Facebook and Google have published studies describing computer hardware failures whose causes have not been easy to identify. The problem, they argued, was not in the software — it was somewhere in the computer hardware made by various companies.
I want to direct your attention to this statement: “The problem… was not in the software.”
Now that is an interesting observation about software. The general rule is that software has flaws. Maybe Steve Gibson can generate “perfect” software for SpinRite, but how many at the alleged technology monopolies follow his practices? I would assert that many at the alleged technology monopolies know what his method is; therefore, if certain wizards don’t know something, it clearly is not worth knowing in the first place.
I interpreted the statement that “The problem … was not in the software.”
Hubris, thy manifestation is those who believe their software was not a problem.
Ho, ho, ho.
My concern is that presenting an argument that failures in uptime are someone else’s problem invites the conclusion, “Well, we will be more like Apple. Hasta la vista, Intel.”
Personally I don’t care what the alleged technology monopolies do. Trouble looms for these outfits regardless of the direction in which I look. What annoys me is that the Gray Lady is pretty happy telling the alleged technology monopolies’ story.
The problem is not the software. The problem is the human thing: Reformation, disinformation, and misinformation as stealth weapons in the battle for continued market dominance.
Stephen E Arnold, February 8, 2022
NSO Group: Another Ripple in the Intelware Sector
February 8, 2022
I read Haaretz’s article “Pegasus Scandal Is a Massive Can of Worms About to Erupt All Over Israel’s Elites.” Is a “commission of inquiry” into NSO Group and related topics a good idea, an inevitable action, or just handwaving after the train has left Tel Aviv Savidor Mercaz? Overturning previous legal decisions may be the least disruptive consequence of the NSO Group-type of publicity that specialized software and service firms are attracting.
There’s another twist. This write up states:
Public Security Minister Omer Bar-Lev announced the formation of a commission of inquiry into the police use of Pegasus after both he and Israel Police commissioner Kobi Shabtai had called for an external investigation into the matter. This was a major about-face from earlier statements…
What repercussions will result from this new group poking around in systems, methods, policies, customers, use cases, and functionalities?
My thought is that there will be louder thumps than those created by Ringo Star in the tune “Get Back.”
I found this line particularly interesting:
Netanyahu is also the pioneer of “Pegasus diplomacy,” using the cyber offense tool developed by the NSO Group as a sweetener for all manner of diplomatic and security agreements with foreign leaders – ranging from Brazil’s Jair Bolsonaro to Saudi Crown Prince Mohammed bin Salman.
When will the rest of the band kick in? Nope, says the write up:
This investigation has the potential to rock Israel’s political class, the law enforcement establishment, the intelligence community and Israel’s foreign relations. As a result, it is unlikely to go very far.
Stephen E Arnold, February 8, 2022
Data Federation? Loser. Go with a Data Lake House
February 8, 2022
I have been the phrase “data lake house” or “datalake house.” I noted some bold claims about a new data lake house approach in “Managed Data Lakehouse Startup Onehouse Launches with $8M in Funding.” The write up states:
One of the flagship features of Onehouse’s lakehouse service is a technology called incremental processing. It allows companies to start analyzing their data soon after it’s generated, which is difficult when using traditional technologies.
The write up adds:
The company’s lakehouse service automatically optimizes customers’ data ingestion workflows to improve performance, the startup says. Because the service is delivered via the cloud on a fully managed basis, customers don’t have to manage the underlying infrastructure.
The idea of course is that traditional methods of handling data are [a] slow, [b] expensive, and [c] difficult to implement.
The premise is that the data lake house delivers more efficient use of data and a way to “future proof the data architected for machine learning / data science down the line.”
When I read this I thought of Vivisimo’s explanation of its federating method. IBM bought Vivisimo, and I assume that it is one of the ingredient in IBM’s secret big data sauce. MarkLogic also suggested in one presentation I sat through that its system would ingest data and the MarkLogic system (once eyed by the Google as a possible acquisition) would allow near real time access to the data. One person in the audience was affiliated with the US Library of Congress, and that individual seemed quite enthused about MarkLogic. And there are companies which facilitate data manipulation; for example, Kofax and its data connectors.
From my point of view, the challenge is that today large volumes of data are available. These data have to be moved from point A to point B. Ideally data do not require transformation. At some point in the flow, data in motion can be processed. There are firms which offer real time or near real time data analytics; for example, Trendalyze.com.
Conversion, moving, saving, and then doing something “more” with the data remain challenges. Maybe Onehouse has the answer?
Stephen E Arnold, February 8, 2022
Threat Intelligence Purchases
February 8, 2022
Many companies are (rightly) are putting more emphasis on cybersecurity. In order to make the task easier and more efficient, a business might invest in software to help manage and analyze all the data involved. BetaNews offers “Five Pointers for Choosing a Threat Intelligence Platform: What to Look For in a TIP.” We see this write-up as but a starting point—it holds some useful pointers but includes no benchmark about SolarWinds and Exchange type exploits. Nor does it address the vital points of insider threats and phishing. Readers looking to expand their cybersecurity efforts would do well to carry their research beyond this article. That said, we turn to writer Anthony Perridge’s description of a TIP:
“A Threat Intelligence Platform, or TIP, serves as a central repository for all threat data and intelligence from internal and internal sources. Correctly configured, the TIP should be able to deliver essential context around threats that helps the team understand the who, what, when, how and why of a threat. Crucially, it should also help prioritize threats, based on the parameters set by the organization, filtering out the noise so the resulting actions are clear. A good TIP benefits a range of stakeholders, from the board aiming to understand strategic risk to CISOs focusing on improving defense while staying on budget, and from security analysts collaborating more effectively to incident response teams benefiting from automated prioritization of incidents. Knowing what you need to invest in is the first step. The next is to understand the key features you need and why. There is a lot to consider, but in my view the following are five key areas that should be on your checklist as you evaluate TIPs.”
The piece goes on to describe each of these five factors: support for both structured and unstructured data (shouldn’t that be a given by now?); the ability to provide context around data; how the platform scores and prioritizes indicators; the integration options available; and effective automation balanced with manual investigation. Then there are the “business considerations,” in other words, the costs involved. For example, TIPs are usually offered on a subscription, per user basis. One should consider carefully how many users should get access—teams outside security operations, like risk management, might need to be included. Also, pay close attention to the fees that can add up, like integration and cloud hosting fees. See the write-up for more information; just remember not to stop your investigation there.
Cynthia Murrell, February 8, 2021
Government Content Removal Requests by Country, Visualized
February 8, 2022
We often hear about countries requesting tech companies remove certain content from their online platforms, especially Russia and China. It can be difficult, though, to discern and compare which types of content is verboten in which nations. Digg paints us a picture in, “The Countries that Ask Google to Remove the Most Content, Visualized.” Reporter Adwait writes:
“The most common reason for taking down content is ‘defamation’ according to a Surfshark analysis, which six out of the top ten leaders cite as a reason. Russia has a sizable lead with the most number of takedown requests, nearly ten-times more than second-placed Turkey. … Google receives thousands of requests every year from all levels of government to remove online content. From infringement of intellectual property rights to defamation, there are a number of reasons a removal request might be submitted. But where in the world asks Google to remove content the most? Historically, Russia is by far the most prolific content removal requester, submitting 123,606 requests in total over the past ten years. Turkey is next up with 14,231 requests which, although the second-highest figure, seems mere in comparison.”
Such a visual aid is a good idea, but it would be even better if it were well executed. Sadly, this illustration features ribbon graphs in muted colors with no numbers. Readers may want to navigate instead to the Surfshark User Data Surveillance Report from which this graphic was made. It includes several informative graphs, all of which contain easily discernable colors and actual numbers. It also includes data on request made of Microsoft, Facebook, and Apple as well as Google. The cybersecurity firm behind the report, Surfshark, was founded in 2018 and is based in Tórtola, Castilla-La Mancha, Spain.
Cynthia Murrell, January 8, 2021
NSO Group: Under Watch Names Revealed
February 7, 2022
I noted the Calcalist article “No One Was Immune: Israel Police Pegasus Surveillance List Revealed.” The downstream consequences of the NSO Group’s MBA-infused approach to specialized software and services continue to become visible.
This passage refers to Israel; however, it is a thought starter:
The bland term used by police for these activities was “technological and data oriented policing,” but Calcalist reveals that the use of Pegasus wasn’t local or limited to a small number of cases. This became one of the most useful tools implemented by police to gather intelligence. Special operations members of the police’s cyber-SIGINT unit have been penetrating the phones of citizens secretly and without judicial warrants, taking control of them with Pegasus against the law and with the understanding that judges wouldn’t approve such activity.
I want to reiterate that the old-school specialized software and services vendors focus their efforts on direct contacts with government agencies and/or attending limited or restricted attendance conferences. As the number of firms tapping open source and proprietary methods to gain access to certain data streams increased, the need for MBA-type marketing exponentiated.
A return to more traditional methods would be a refreshing change. Who is to blame? I think the entrepreneurs who create specialized software and services firms are prime movers. However, the enablers are the entities which fund these often young go-getters bear some responsibility. Blaming under funded, understaffed, and under equipped government professionals may be warranted under some circumstances.
My view is that an engineer chock full of MBA-isms should be licensed prior to hanging out a shingle, signing up for a trade show stand, and generating buzz via news releases and social media posts on LinkedIn.
Until then, the knock ons from the NSO Group’s global visibility are likely to hold some surprises. Do you like surprises? I don’t too much.
Stephen E Arnold, February 7, 2022
A Non Googley Person Demonstrates That Fact
February 7, 2022
I read “Google Slides is Actually Hilarious.” Ms. Javier, may I call you Laura? Laura, I want to be helpful. You have identified logical functions in a content creation tool from the company that embodies technology. Your failure to recognize the company’s brilliance — essentially the breath-taking equivalent of Brunelleschi’s dome or Einstein’s theory of relativity — make it clear that you have to rewire your thinking in order to appreciate the outputs of Googzilla. I fear your write up offers hard evidence that you, earnest but obtuse Laura, are not Googley. Definitely.
Let me highlight three quantum supremacy grade functions you find amusing:
First, left aligned text in circles. Indeed, the stylistic touch is “very cool.” Competitive projects like Microsoft’s sad looking PowerPoint or Libre’s donkey-like Impress continue the death-by-slide-deck motifs that lost favor in one of General Schwarzkophf Jr.’s White House presentations. Believe me, the off center text offers a visual break from the dreary sameness of Department of Defense-contractor created slide decks. Loosen up. Don’t be like General Schwarzkopf Jr. Embrace the left aligned! Now!
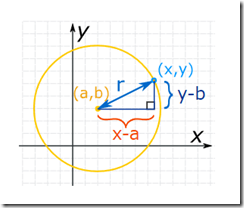
Second, your statement that “it’s impossible to align text with images.” Oh, Laura, it is only impossible for the non-Googley. The work arounds are easy: [1] Write a script in Go. [2] Have the script output of the text presented in a PNG files as “art.” [3] Have the script create a new slide. [4] Have the Snorkel based AI determine the high probability location at which to paste in the art. [5] The Pichai approved smart software will copy the art from new slide to your rather lame slide with this type of calculation:
Thanks to MathIsFun.com for the circle.
[6] When the script ends, you can adjust final placement by holding the Shift key and using the cursor keys to move the PNG where you want it. What’s the big deal. Laura, dare I ask, “Are you adept at Go? Maybe Python?”
Finally, the “transparency slider that starts at zero.” Oh, Laura, you are in the visible light portion of the electromagnetic spectrum. The Google is banging along in gamma ray land. It is obvious that sliders begin at zero and increment upwards, just like Google’s ad revenue and the number of irrelevant items in a search results page.
Net net: I know you will read books to learn, talk to people who are sadly not Googley, and try to be creative. It’s okay to be not Googley. Laura, I think I see some sunshine in this Google presentation situation.
Stephen E Arnold, February 7, 2022
Facial Recognition: Trouble for Thirsty Teens
February 7, 2022
I spotted an interesting item on the BBC Web site. (At some point, the article may be removed as Mother Beeb does her on-going content clean up.) The story is “Supermarket Cameras To Guess Age of Alcohol Buyers.” Some young people use falsified documents in order to purchase products with age controls. These have been handcrafted at home, obtained from a friend at a football match, or purchased via Telegram. Due to the legal risk of providing a tasty room temperature alcoholic beverage to someone too young to purchase the fine drink legally, stores have had to rely of keen eyed employees. Yeah, well, that doesn’t work too well in the age of Covid and it never worked in many situations. The write up explains that the controversial technology of facial recognition will be used by some stores and probably drinking establishments to help verify the age of the would be imbiber. The write up states:
The trial will use cameras that can estimate each customer’s age. It is part of a Home Office test of technologies to assist with the selling of alcohol.
I wonder if the images will be captured and stored? Will the system rely on smart software or a combination of a database of faces and artificial intelligence? Will the system “learn” and improve its accuracy?
So far: No answers.
Stephen E Arnold, February 7, 2022
African Governments Vs. Citizens Online
February 7, 2022
As Market Research Telecast reports in a recent write-up, “Hacking: Demand for Products from the NSO Group and Co. Does Not Decrease.” As that piece points out, sales of the notorious Pegasus and other spyware continue to grow despite a rash of lawsuits, sanctions, and other threats against preeminent spyware vendor NSO. We see several examples of ways governments use such tools and other cyber strategies against their citizens, and some unintended consequences, in the Africa Center for Strategic Studies’ article, “Deluge of Digital Repression Threatens African Security.” Reporters Nathaniel Allen and Catherine Lena Kelly write:
“Digital repression is on the rise in many parts of Africa. Over a dozen African countries have recently experienced politically motivated internet shutdowns. Roughly the same number have been identified as operators of military-grade spyware (such as Pegasus, RCS, and FinFisher), which they use to track domestic political opponents and activists with the same vigor as criminals and terrorists. Governments employ automated tools to subject social media platforms to expansive surveillance. Increasingly, leaders are taking advantage of vague elements of recently passed cybercrime laws to expand executive powers to arrest activists and debilitate the free press. African leaders frequently portray digitally repressive tactics as necessary to combat threats from terrorism, organized crime, and secessionist violence. In fact, their main impact is to undermine the fundamental freedoms that make it possible for governments to be transparent, legitimate, and accountable to citizens.”
The thorough, link-filled article provides examples of such legislation leveraging, beginning with Tanzania. Information gathered with spyware is used against political opponents, journalists, and activists to blackmail, harass, or arrest them. Then there are other repressive tactics, like simply shutting down the Internet. This is a favorite ploy before and during contested elections and amid protests.
Allen and Kelly point out this irony: though governments often cite security as their excuse for implementing repressive policies, such measures often have the opposite effect by fueling political instability. Then there are the financial costs—like the rest of the world, much of Africa’s business has moved online. Politically motivated Internet shutdowns can be extremely pricy.
The article goes on to spell out some measures that can help combat misinformation and extremism online without sacrificing citizen rights. It also describes several citizen-centric organizations working to protect online freedoms in different parts of Africa. See the article for those details.
Cynthia Murrell, February 9, 2022
What Speed Brings
February 7, 2022
People, especially senior citizens, love to proclaim that the Internet is ruining personal relationships, eroding communication and participation, and destroying society. While society will continue to stand, the old fogies might be right about the ruination of participation and communication. The Guardian has an interesting and startling article titled: “Faster Internet Speeds Linked To Lower Civic Engagement In UK.”
Faster internet might be a detriment to society, because a recent study from Cardiff University and Sapienza University discovered that when people had faster Internet they engaged less with political parties, trade unions, and volunteering. Ironically faster Internet did not impact interactions with family or friends. The joint university study found that faster Internet speeds reduced civic engagement among 450,000 people. That is more than double of Great Britain’s Conservative party.
While one cannot trust the polarization of media and the 24-hour news cycle, the Internet does bring attention to civic-centered actions whether that be positive or negative. With that in mind, one would think that people would engage more in civic duties. Faster Internet speeds, however, mean faster access to entertainment and increase the instant gratification syndrome.
Faster Internet might decrease social engagement according to this study, but others found the opposite:
“The study’s authors have also speculated that the phenomenon may have helped fuel populism as people’s involvement with initiatives for “the common good”, which they say are effectively “schools of democracy” where people learn the benefit of cooperation, has declined.
Other studies have shown that social media engagement has strengthened other kinds of civic engagement, for example by helping to organize protests and fuelling an interest in politics, even if it does not manifest in traditional forms of participation.However, politics conducted online has been found to be more susceptible to “filter bubbles”, which limit participants’ exposure to opposing views and so foster polarization.”
The study did take the Covid-19 pandemic into consideration, because it limited civic involvement. Bonding with family and friends grows with faster Internet speeds and current communication trends, but people’s understanding of the importance of civic duties. Economic activity and how democratic institutions function suffer. What is the solution to repair that?
Whitney Grace, February 5, 2022