A US Tool Repurposed by Taliban
September 17, 2021
China is the notorious Big Brother of Asia, but the now Taliban run Afghanistan will be using US-made tools to technologically repress people. According to Market Beat article: “US-Built Databases A Potential Tool Of Taliban Repression,” the United States designed databases for the democratically lead Afghanistan. The databases were designed to help Afghanis by promoting law, government accountability, and modernize the country.
The databases were built without much security and they are now in the Taliban’s hands. There are many databases, including ones that include biometrics for identify verification. The Taliban could use the databases for government surveillance and harm Taliban detractors. Former American allies or possible anti-Taliban people have already received threatening messages and taking precautions.
The Taliban claims they are not interested in retribution and are seeking International aid and unfreezing foreign held assets. The world is waiting with bated breath about what the Taliban will do to Afghanis.
The US created the Afghanistan Automated Biometric Identification Database and former officials in the country state the entire database was erased before the pullout. There are still other databases the Taliban has access to:
“Among crucial databases that remained are the Afghanistan Financial Management Information System, which held extensive details on foreign contractors, and an Economy Ministry database that compiled all international development and aid agency funding sources, the former security official said.
Then there is the data — with iris scans and fingerprints for about 9 million Afghans — controlled by the National Statistics and Information Agency. A biometric scan has been required in recent years to obtain a passport or a driver’s license and to take a civil service or university entrance exam.”
It is also possible that voter registration databases and an anti-fraud database of government officials could be under Taliban control.
Unexpected consequences? Exciting.
Whitney Grace, September 17, 2021
Big Tech Defines Material: What Does That Really Mean to Oligopolistic-Type Outfits?
September 16, 2021
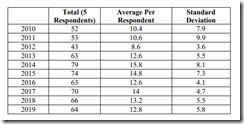
I noted a US government study called “Non HSR Reported Acquisitions by Select Technology Platforms: 2010-2019: FTC Study.” The report, assuming it is spot on, suggests that large companies interpreted the word “material” differently from what some financial / accountant types think it means; for example, “Items are considered to be material when they have an excessive impact on reported profits, or on individual line items within the financial statements.” [Source: The Google, of course.] Some MBAs and accountants have remarkably flexible connotative skills. Is this a Deloitte Touche-type touch?
The report states:
My hunch is that standard deviation is not a hot topic at Zoom happy hours. The standard deviations in the table above suggest that the big tech outfits in the study pretty much redefined “material,” bought stuff and did not make a big deal about it, and chugged along in their cheerfully unregulated state during the period of the study.
The report states:
The five technology platform 6(b) respondents identified 616 non-HSR reportable transactions above $1 million, in addition to 101 Hiring Events and 91 Patent Acquisitions. The respondents reported an additional approximate 60 transactions below $1 million and 160 financial investments. Voting Security (Control) and Asset acquisitions comprise 65% of all of the above transactions. When excluding Hiring Events, Patent Acquisitions, and transactions below $1 million, Voting Security (Control) and Asset acquisitions comprise 85% of the transactions.
I interpret this to mean that the big tech outfits in the sample decided what to report and what to ignore; that is, the deals were not material. There’s that MBA word again.
Here’s another passage I circled:
Most of the transactions that were classified into technology categories were concentrated in the categories of Mobility (mobile devices and device-based software and content, which comprised more than 10% of the acquired firms), Application Software (front-end applications such as CRM, ERP, SCM, BI, commerce and vertical business software, which comprised more than 9% of the acquired firms), and Internet Content & Commerce (internet destination and internet-enabled services, which comprised more than 6% of the acquired firms). In the Mobility and Application Software categories, the number of transactions peaked in 2015; in the Internet Content & Commerce category, the number of transactions peaked in 2011.
Observations:
- Fancy dancing is popular among the companies in the sample; notably, Alphabet/Google, Amazon, Apple, Facebook, and Microsoft
- Regulators, probably with MBAs, looked the other way
- The power of unregulated commercial enterprises makes clear who is in charge of many important technical and social activities.
Interesting stuff, and I am confident that a lawyer with an MBA can explain this misalignment about the meaning of “material.” I wonder if the hints about the behavior of the companies in the sample suggest that we now live in a digital banana republic with the centers of power concentrated among a few corporate entities in their plantation houses.
Stephen E Arnold, September 16, 2021
Just a Little Help from Friends Government Style
September 16, 2021
Nothing should be surprising anymore when it comes to online privacy and targeted ads, but The Guardian shares how governments are trying to alter behavior in the article: “Study Finds Growing Government Use of Sensitive Behavior To ‘Nudge’ Behavior.” Governments have turned to targeted ads on search engines and social media platforms to shape or “nudge” their citizens’ behaviors.
This is a new move “stems from a marriage between the introduction of nudge theory in policymaking and an online advertising infrastructure that provides unforeseen opportunities to run behavioural adjustment campaigns.” Implementing this type of behavior modification could create a perfect feedback loop:
“’With the government, you’ve got access to all this data where you can see pretty much in real time who you need to talk to demographically, and then on the other end you can actually see, well, ‘did this make a difference?’,’ said Ben Collier, of the University of Edinburgh. ‘The government doing this supercharges the ability of it to actually work.’”
Government behavioral modification programs are not new. Countries across the globe have long histories of altering citizens’ behaviors. The United Kingdom is currently employing targeted ad campaigns to deter minors from becoming online fraudsters. Identified at-risk minors online activities are monitored collect data on them that are then used for “influence policing” campaigns with targeted ads. Another influence policing campaign the UK dealt with fire safety. People who purchased candles or matches on Amazon were sent targeted fire safety messages.
The targeted ads appear innocuous and helpful, but the government farms out the work to third party companies. Governments and companies could become lackadaisical with people information and it could impart disinformation. For example, minors targeted with anti-knife violence campaigns might believe that more people carry knives than reality. This could inspire minors to start carrying knives. The anti-fraudster campaigns could also inspire minors to become online bad actors, while the fire safety ads might encourage playing with fire.
Cue the music, please.
Whitney Grace, September 16, 2021
Triggering the Turtle Response: A Cyber Security Misstep?
September 15, 2021
One noble idea is to ask each and every organization to report a cyber attack and data breach. How are noble ideas like this greeted by commercial organizations or government bureaucrats with one eye on SES and one on retirement on a full pension? My hunch is that certain noble ideas are going to be ignored, sidestepped, or bulldozed under legal briefs.
I read “Exclusive: Wide-Ranging SolarWinds Probe Sparks Fear in Corporate America.” The trustworthy outfit Thomson Reuters says:
The SEC is asking companies to turn over records into “any other” data breach or ransomware attack since October 2019 if they downloaded a bugged network-management software update from SolarWinds Corp, which delivers products used across corporate America, according to details of the letters shared with Reuters. People familiar with the inquiry say the requests may reveal numerous unreported cyber incidents unrelated to the Russian espionage campaign, giving the SEC a rare level of insight into previously unknown incidents that the companies likely never intended to disclose.
Many organizations bite the bullet and keep cyber breach info under wraps. Examples include outfits dealing with financial transactions and juicy pharma companies, among others.
What’s going to happen? Investigators will find interesting information to explore and, in the manner of investigators, and piece together.
What’s one method of dealing with this intriguing government request? The turtle response. Pull one’s head into a shell and hope the legal eagles can make it safe to return to pre-SolarWinds’ practices.
Stephen E Arnold, September 15, 2021
Australia Channels China: What Is Next Down Under?
September 13, 2021
Should one be alarmed about the power that social media has. Should one sorry when governments, after decades of indifference, exert their authority over social media. The Conversation discusses a new Australian law and its implications in, “Facebook Or Twitter Posts Can Now Be Quietly Modified By The Government Under New Surveillance Laws.” The new law updates the Surveillance Devices Act 2004 and Telecommunications (Interception and Access) Act 1979. The addendum gives law enforcement officials in Australia to modify, add, copy, or delete online during an investigation.
The Human Rights Law Centre says the bill could violate free speech, while the Digital Rights Watch pointed out that the Australian government ignored recommendations to limit powers in the new bill. Not to mention, legal hacking could make it easier for bad hackers.
The new bill allows authorities to copy, delete, or modify data, with a warrant collect data, and assume control of a social media account. It also contains “emergency authorization” for law enforcement to do any of the above without a warrant.
Prior legislation of this nature included better privacy protections, but the new bill gives law enforcement free rein and force individuals to assist them or face prison time. On one hand the ill makes sense:
“According to the Department of Home Affairs, more and more criminal activity makes use of the “dark web” and “anonymising technologies”. Previous powers are not enough to keep up with these new technologies. In our view, specific and targeted access to users’ information and activities may be needed to identify possible criminals or terrorists. In some cases, law enforcement agencies may need to modify, delete, copy or add content of users to prevent things like the distribution of child exploitation material. Lawful interception is key to protecting public and national security in the fight of global community against cybercrimes.”
On the other hand, third parties could be subject to law enforcement. Individuals’ freedoms could be violated too.
Channeling China? Trying to control speech? What’s next?
Whitney Grace, September 13, 2021
Why Big Tech Is Winning: The UK Admission
August 31, 2021
I read “UK’s FCA Say It Is Not Capable of Supervising Crypto Exchange Binance.” This is a paywalled story, and I am not sure how much attention it will get. As Spotify is learning from locking up the estimable Joe Rogan, paywalls make sense to a tiny slice of one’s potential audience.
The story is an explanation about government helplessness when it comes to fintech or financial technology. The FCA acronym means Financial Conduct Authority. Think about London. Think about the wizards who cooked up some nifty digital currency methods at assorted UK universities less than one hour from the Pickle. Think about the idea that a government agency with near instant access to the wonks at the National Crime Agency, the quiet ones at Canary Wharf, and the interesting folks in Cheltenham. Now consider this passage from the write up:
… the Financial Conduct Authority said that Binance’s UK affiliate had “failed to” respond to some of its basic queries, making it impossible to oversee the sprawling group, which has no fixed headquarters and offers services around the world. The admission underscores the scale of the challenge facing authorities in tackling potential risks to consumers buying frequently unregulated products through nimble crypto currency businesses, which can often circumvent national bans by giving users access to facilities based overseas.
Hello? Rural Kentucky calling, is anyone at work?
Let’s step back. I need to make one assumption; that is, government entities’ have authority and power. What this write up makes clear is that when it comes to technology, the tech outfits have the authority and the power.
Not good in my opinion for the “consumer” and maybe for some competitors. Definitely not good for enforcement authorities.
Who finds sun shining through the clouds after reading this Financial Times’s story? I would wager that tech centric outfits are thinking about a day or more at the beach. No worries. And look. Here comes Snoop Dog handing out free beer. What a day!
Stephen E Arnold, August 31, 2021
Amazon: Can the Bezos Bulldozer Pull Off a JEDI Play in the EU?
August 31, 2021
The Bezos bulldozer is a wonderful construct, and it is uniquely American. For those who do not follow the path of the machine as it grinds forward, Amazon made a case to rip from the grasp of Microsoft the JEDI contract. Now the mom-and-pop seller of books has an opportunity to rework the landscape of an EU fine in the neighborhood of a billion dollars. My goodness, it takes less than a day for the ecommerce store to generate one billion in cash. Painful? For sure.
You can read about this fine in “Europe: Amazon Slapped with Record-Breaking Privacy Fine.” The article characterizes the levy as an “enormous bite.” Yep, one day of revenue is painful indeed. Game changer? Nope.
The question is, “Why not?” With each “punishment” it becomes more and more clear that there is little incentive for certain large technology companies to change their business strategy or practices. After decades of business as usual, change becomes more and more difficult for both regulators and the business constructs. Who’s running the show? Obviously not the regulators.
Stephen E Arnold, August 31, 2021
Palantir: A Blinded Seeing Stone?
August 27, 2021
I try to keep pace with the innovations in intelware. That’s my term for specialized software designed to provide the actionable information required by intel professionals, law enforcement, and one or two attorneys who have moved past thumbtyping.
I am not sure if the article “FBI Palantir Glitch Allowed Unauthorized Access to Private Data” is on the money. The “real news” story asserted:
A computer glitch in a secretive software program used by the FBI allowed some unauthorized employees to access private data for more than a year, prosecutors revealed in a new court filing. The screw-up in the Palantir program — a software created by a sprawling data analytics company co-founded by billionaire Peter Thiel — was detailed in a letter by prosecutors in the Manhattan federal court case against accused hacker Virgil Griffith.
Please, read the source document. Also, my personal view is that such an access lapse is not good, but if the story is accurate, I am less concerned that other FBI officials may have had access to content in Gotham or whatever the system is branded these days is less problematic than oligarchs snooping or a Xi Jinping linked tong IT wonk poking around FBI only data.
My thoughts went in a different direction, and I want to capture them. Keep in mind, I don’t know if the access revelation is “true.” Nevertheless, here’s what I jotted down whilst sitting in a lecture about a smart bung for booze lovers:
- Was the access issue related to Microsoft Windows or to the AWS-type services on which some Palantir installations depend? Microsoft is another “here we go again” question, but the AWS question puts the Bezos bulldozer squarely in the security breach spotlight.
- How many days, weeks, or months was the access control out of bounds? An hour is one thing; the answer “We don’t have a clue” is another.
- If — note the if, please — the access issue is due to a Palantir specific feature or function, is there a current security audit of LE, military, and intel related installations of the “seeing stone” itself? If the answer is “yes”, why was this access issue missed? Who did the audit? Who vetted the auditor? If the answer is “no,” what are the consequences for the other software vendors and IT professionals in the “fault chain”?
The article points out that a royal “we” is troubled. That’s nice. But let’s focus on more pointed questions and deal with what might be a digital Humpty Dumpty. Just my opinion from the underground bunker in rural Kentucky.
Stephen E Arnold, August 27, 2021
Big Tech Vows, Warrants, Commits, Guarantees, and Assures to Make Security Way Way Way Better
August 26, 2021
I had to laugh. I read some of the write ups explaining the pledges of big tech to the White House about security. The US is at or near the bottom when it comes to security. America plays offense. The defense thing is not what George Washington would do.
Here’s a representative write up: “Google, Microsoft Plan to Spend Billions on Cybersecurity after Meeting with Biden.” This triggered a chuckle and a snort:
IBM CEO Arvind Krishna told CNBC ahead of the meeting and outside the White House on Wednesday that cybersecurity is “the issue of the decade.” He said he hoped to see more coordination between the public and private sectors coming out of the meeting and said IBM would do its part to help skill workers in the space.
Why are adversaries of the US running exfiltration, ransomware, and intellectual property theft operations?
Let me count the ways:
- Systems from outfits like Apple and Microsoft can be compromised because security is an add on, an afterthought, or a function implemented to protect revenues
- Senior managers in many US firms are clueless about security and assume that our employees won’t create problems by selling access, clicking on scammer emails, or working from home on projects funded by bad actors
- Customers pay little or no attention to security, often ignoring or working around security safeguards when they exist. Hey, security distracts those folks from scrolling through Facebook or clicking on TikTok videos.
There are other reasons as well; for example, how about the steady flow of one off security gaps discovered by independent researchers. Where are the high end threat intelligence services. If a single person can find a big, gaping security hole, why are the hundreds of smart cyber security systems NOT finding this type of flaw? Oh, right. Well, gee. A zero day by 1,000 evil techies in China or Moldova is the answer. Sorry, not a good answer.
There is a cyber security crisis in America. Yes, Windows may be the giant piece of cheese for the digital rats. Why hack US systems? That’s where there are lots of tasty cheese.
Is there a fix which billions “invested” over five years can fix?
Nope.
Pipe dreams, empty words, and sheepish acquiescence to a fact that bad actors around the world find enervating.
More stringent action is needed from this day. That’s not happening in my opinion. Who created the cyber security problem? Oh, right the outfits promising do not do it again. Quick action after decades of hand waving. And government regulations, certification, and verification that cyber security systems actually work? Wow, that’s real work. Let’s have a meeting to discuss a statement of work and get some trusted consulting firm on this pronto.
I have tears in my eyes and not from laughing. Nothing funny here.
Stephen E Arnold, August 26, 2021
About Those Painful Fines
August 24, 2021
Never one to let pesky regulations get in the way of doing business, “Amazon Hit with Record $888M Fine Over GDPR Violations,” reports CNet. Even that eye-popping sum represents but a minor cost of doing business to the online retail giant. Luxembourg authorities levied the 746 million euro fine on July 16, saying Amazon violated the EU’s GDPR data protection laws. At issue is the way the company processes customer data. Citing reporting from Bloomberg, writer Katie Collins tells us:
“[The CNPD’s] into Amazon was based on a 2018 complaint by French privacy group La Quadrature du Net. The group says it represents the interests of thousands of Europeans to ensure their data isn’t used by big tech companies to manipulate their behavior for political or commercial purposes. It didn’t immediately respond to request for comment. Amazon is under growing scrutiny both at home and abroad over the way it uses customer data. Regulators are concerned that not only could the company’s data processing policies violate privacy protections for consumers while they’re shopping online, they might give the company an advantage over competitors operating within its marketplace. Meanwhile, Amazon is keen for customers to know that their data is safe, and unlike many GDPR fines, this one hasn’t been issued due to a data breach. ‘Maintaining the security of our customers’ information and their trust are top priorities,’ said an Amazon spokesman in a statement on Friday. ‘There has been no data breach, and no customer data has been exposed to any third party. These facts are undisputed.’”
Nice attempt at deflection, Amazon. A data breach is not the issue here, but rather willful disregard of EU privacy regulations. The Amazon spokesperson insists the fine is based on “subjective and untested interpretations” of the GDPR and that it is entirely out of proportion. Though it plans to appeal the fine, it is a price the company can easily pay.
To answer the question, will the fine have an impact? Nope, a monetary penalty is ineffective. Consider this: Russia Fines Google For Not Deleting Banned Content. How much? Three million rubles or about $40,000US. Facebook might be fined as much as $82,000 by the Russian bear.
Painful not.
Cynthia Murrell, August 25, 2021