Open Source Software: Do Flashing Neon Signs Say, Bad Actors Welcome?
March 29, 2022
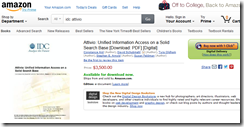
Remember when IDC, one of the units of the Patrick McGovern empire, was a big dog. Before the research unit wound up with swamp mud on its discount sneakers, one of the self-appointed experts suggested my team assemble a big report about — wait for it — open source search. We assembled our data, created profiles similar to those available on my Web site www.xenky.com/vendor-reports, and provided drafts to the estimable IDC. We learned, quite to my surprise, that several of these drafts were listed on Amazon.com for $3,000 each. We did not have a contract, and IDC had no permission to do anything with our profiles of about a dozen open source search solutions. Quite sporty behavior for “the premier global provider of marketing intelligence, advisory services, and events for the information technology, telecommunications, and consumer technology markets.” One IDC expert informed me that the company was called Foundry now. Yeah, who knew?
How do I know IDC sold my work on Amazon without an agreement from me? Check this out:
One take away from our book about open source search software was that security was an afterthought. Did users of open source software think about security? Nope. The users thought about how much money would be saved relying on a “community.” Users like the idea of not having proprietary software companies prevent changes to the code. Security was a community responsibility. Easy assumptions for users who wanted flexibility, reduced costs, and a false sense of no worries about this code.
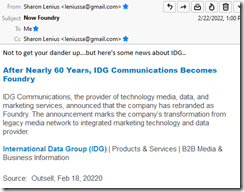
Does the big outfit which violated my copyright and stole my intellectual property care? The information about the lack of security in an enterprise open source software sector was effectively killed. Here’s an email I received in February 2022. You judge what’s shakin’.
The author is in some way affiliated to Foundry. The entity is called Sharon Lenius, and I assume she will respond to email sent to her at leniussa@gmail.com. Let’s hope she receives a lot of email.
Why this jaunt through the history of IDC and open source search software? If the company had its well oiled second hand store slicker in tip top shape, the security weaknesses of open source search software. Furthermore, the reason open source search as well as other types of software were being adopted by big outfits was cost reduction. The big firms used what could be downloaded, assuming that the “community” would identify flaws, fix them, and assume the responsibilities companies should have shouldered themselves.
When I read “A Developer Altered Open Source Software to Wipe Files in Russia,” I thought “decade old news.” A decade! Do I care? The write up states:
The developer of a popular open source package has been caught adding malicious code to it, leading to wiped files on computers located in Russia and Belarus. The move was part of a protest that has enraged many users and raised concerns about the safety of free and open source software.
I think that the security problems now released as “real news” are significant. Security, code integrity, and malicious actions on the part of the community were not at the top of the to do list 10 years ago and are not at the top of the list today.
Is there a fix? Sure, but like most fixes, it is likely to be too little and too late. Like the self regulation of financial services firms, there is considerable room for creative thinking in the open source software sector. In my upcoming 2022 National Cyber Crime Conference lecture, I will point out specific open source tools which can be used to subvert systems relying on open source software. Why not create a malicious chunk of code, tuck it in a library, and allow an incurious 20 something to undermine an organization?
Why not relay on outfits like mid tier consulting firms to provide actionable information? Why not wait until an armed conflict highlights a ticking IED inside some of the most widely used enterprise applications? Why not act in an ethical, responsible way?
I will be dead and logged off permanently before these questions are answered.
Stephen E Arnold, March 29, 2022