Making Chips: What Happens When Sanctions Spark Work Arounds
October 25, 2023
![Vea4_thumb_thumb_thumb_thumb_thumb_t[2] Vea4_thumb_thumb_thumb_thumb_thumb_t[2]](https://arnoldit.com/wordpress/wp-content/uploads/2023/10/Vea4_thumb_thumb_thumb_thumb_thumb_t2_thumb-21.gif) Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Maybe the Japanese outfit Canon is providing an example of the knock on effects of sanctions. On the other hand, maybe this is just PR. My hunch is more information will become available in the months ahead. “Nanoimprint Lithography Semiconductor Manufacturing System That Covers Diverse Applications with Simple Patterning Mechanism” discloses:
On October 13, 2023, Canon announced today the launch of the FPA-1200NZ2C nanoimprint semiconductor manufacturing equipment, which executes circuit pattern transfer, the most important semiconductor manufacturing process.
“This might be important,” says a technologically oriented animal in rural Kentucky. Thanks, MidJourney, continue to descend gradiently.
The idea is small and printing traces of a substance. The application is part of the expensive and delicate process of whipping out modern chips.
The write up continues:
By bringing to market semiconductor manufacturing equipment with nanoimprint lithography (NIL) technology, in addition to existing photolithography systems, Canon is expanding its lineup of semiconductor manufacturing equipment to meet the needs of a wide range of users by covering from the most advanced semiconductor devices to the existing devices.
Several observations are warranted:
- Oh, oh. A new process may be applicable to modern chip manufacturing.
- The system and method may be of value to countries dealing with US sanctions.
- Clever folks find ways to do things that regulatory language cannot anticipate.
Is this development important even if the Canon announcement is a bit fluffy? Yep, because the information about the system and method provide important road signs on the information superhighway. Canon does cameras, owns some intelware technology, and now allegedly provides an alternative to the traditional way to crank out advanced semiconductors.
Stephen E Arnold, October 25, 2023
Video Analysis: Do Some Advanced Systems Have Better Marketing Than Technology?
October 16, 2023
![Vea4_thumb_thumb_thumb_thumb_thumb_t[2] Vea4_thumb_thumb_thumb_thumb_thumb_t[2]](https://arnoldit.com/wordpress/wp-content/uploads/2023/10/Vea4_thumb_thumb_thumb_thumb_thumb_t2_thumb-20.gif) Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
I am tempted to list some of the policeware and intelware companies which tout video analysis capabilities. If we narrow our focus to Israel, there are a number of companies which offer software and systems that can make sense of video data. Years ago, I attended a briefing and the company (which I will not name) showed that its system could zip through a 90 minute video of a soccer (football) match and identify the fouls and the goals. Like most demonstrations, the system worked perfectly. In actual real world situations, the system did not work. Video footage is a problem, but there are companies which assert their developers’ confection.
Aggressive bunnies get through the farmer’s fence. The smart surveillance cameras emit a faint beep. The bunnies are having a great time. The farmer? Not so much. Thank you, MidJourney. You do a nice bunny.
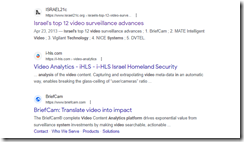
Here’s the results of the query “video analysis Israel.” Notice that I am not including the name of a company nor a specific country. Google returned ads and video thumbnails and this result:
The cited article is from Israel21c 2013 write up “Israel’s Top 12 Video Surveillance Advances.” The cited article reports as actual factual:
Combing such vast amounts of material [from the Boston Marathon bombing in 2013] would have taken months, or even years in the past, but with new video analytics technologies developed by Israel’s BriefCam, according to the publication IsraelDefense, it took authorities just a few days to identify and track Tamerlan and Dzhokhar Tsarneav, the two main suspects in the attack which killed three, and wounded 183. Within five days one of the terrorists was dead, the other arrested after a 22-hour manhunt.
BriefCam is now owned by Canon, the Japanese camera maker. Imagine the technical advances in the last 10 years.
I don’t know if Israel had a BriefCam system at its disposal in the last six months. My understanding is that the Israel Defense Force and related entities have facial recognition systems. These can work on still pictures as well as digital video.
Why is this important?
The information in the San Francisco Chronicle article “Hamas Practiced in Plain Sight, Posting Video of Mock Attack Weeks Before Border Breach” asserts:
A slickly produced two-minute propaganda video posted to social media by Hamas on Sept. 12 shows fighters using explosives to blast through a replica of the border gate, sweep in on pickup trucks and then move building by building through a full-scale reconstruction of an Israeli town, firing automatic weapons at human-silhouetted paper targets. The Islamic militant group’s live-fire exercise dubbed operation “Strong Pillar” also had militants in body armor and combat fatigues carrying out operations that included the destruction of mock-ups of the wall’s concrete towers and a communications antenna, just as they would do for real in the deadly attack last Saturday.
If social media monitoring systems worked, the video should have been flagged and routed to the IDF. If the video analysis and facial recognition systems worked, an alert to a human analyst could have sparked a closer look. It appears that neither of these software-intermediated actions took place and found their way to a human analyst skilled in figuring out what the message payload of the video was. Who found the video? Based on the tag line to the cited article, the information was located by reporters for the Associated Press.
What magical research powers did the AP have? None as it turns out. The article reports:
The Associated Press reviewed more than 100 videos Hamas released over the last year, primarily through the social media app Telegram. Using satellite imagery, the AP was able to verify key details, as well as identify five sites Hamas used to practice shooting and blowing holes in Israel’s border defenses. The AP matched the location of the mocked-up settlement from the Sept 12 video to a patch of desert outside Al-Mawasi, a Palestinian town on the southern coast of the Gaza Strip. A large sign in Hebrew and Arabic at the gate says “Horesh Yaron,” the name of a controversial Israeli settlement in the occupied Palestinian West Bank.
I don’t want to be overly critical of tools like BriefCam or any other company. I do want to offer several observations from my underground office in rural Kentucky:
- The Hamas attack was discernable via humans who were paying attention. Were people in the IDF and related agencies paying attention? Apparently something threw a wrench in a highly-visible, aggressively marketed intelligence capability, right?
- What about home grown video and facial recognition systems? Yes, what about them. My hunch is that the marketing collateral asserts some impressive capabilities. What is tough to overlook is that for whatever reason (human or digital), the bunny got through the fence and did damage to some precious, fragile organic material.
- Are other policeware and intelware vendors putting emphasis on marketing instead of technical capabilities? My experience over the last half century says, “When sales slow down and the competition heats up, marketing takes precedence over the actual product.”
Net net: Is it time for certification of cyber security technology? Is it time for an external audit of intelligence operations? The answer to both questions, I think, is, “Are you crazy?”
Stephen E Arnold, October 16, 2023
xx
xx
xx
India: Okay, No More CSAM or Else the Cash Register Will Ring
October 12, 2023
![Vea4_thumb_thumb_thumb_thumb_thumb_t[1]_thumb Vea4_thumb_thumb_thumb_thumb_thumb_t[1]_thumb](https://arnoldit.com/wordpress/wp-content/uploads/2023/10/Vea4_thumb_thumb_thumb_thumb_thumb_t1_thumb_thumb.gif) Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
X (the Tweeter thing), YouTube, and Telegram get a tough assignment. India wants child sexual abuse material or CSAM for those who want to do acronym speak scrubbed from content or services delivered in the great nation of India. There are some interesting implications for these US technology giants. First, the outfits are accustomed to just agreeing and not doing much to comply with government suggestions. In fact, most of the US high-tech firms offer promises, and those can be slippery fish. Second, determining what is and what is not CSAM can be a puzzler as well. Bad actors are embracing smart software and generating some realistic images and videos without having to find, coerce, film, and pay off humans involved in the distasteful but lucrative business. Questions about the age of a synthetic child porno star are embarrassing to ask and debate. Remember the need for a diverse group to deliberate about such matters. Also, the advent of smart software invites orchestration so that text prompts can be stuffed into a system. The system happily outputs videos with more speed than a human adult industry star speeding to a shoot after a late call. Zeros and ones are likely to take over CSAM because … efficiency.
“India Tells X, YouTube, Telegram to Remove Any Child Sexual Abuse Material from Platforms” reports:
The companies could be stripped of their protection from legal liability if they don’t comply, the government said in a statement. The notices, sent by the federal Ministry of Electronics and Information Technology (MEITY), emphasized the importance of prompt and permanent removal of any child sexual abuse material on these platforms.
My dinobaby perspective is that [a] these outfits cannot comply because neither smart software nor legions of human content curators can keep up with the volume of videos and images pumped by these systems. [b] India probably knows that the task is a tough one and may be counting on some hefty fines to supplement other sources of cash for a delightful country. [c] Telegram poses a bit of a challenge because bad actors use Dark Web and Clear Web lures to attract CSAM addicts and then point to a private Telegram group to pay for and get delivery of the digital goods. That encryption thing may be a sticky wicket.
Net net: Some high-tech outfits may find doing business in India hotter than a Chettinad masala.
Stephen E Arnold, October 13, 2023
Intelware: Some Advanced Technology Is Not So New
October 11, 2023
![Vea4_thumb_thumb_thumb_thumb_thumb_t[2] Vea4_thumb_thumb_thumb_thumb_thumb_t[2]](https://arnoldit.com/wordpress/wp-content/uploads/2023/10/Vea4_thumb_thumb_thumb_thumb_thumb_t2_thumb-8.gif) Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
I read “European Spyware Consortium Supplied Despots and Dictators.” The article is a “report” about intelware vendors. The article in Spiegel International is a “can you believe this” write up. The article identifies a number of companies past and present. Plus individuals are identified.
The hook is technology that facilitates exfiltration of data from mobile devices. Mobile phones are a fashion item and a must have for many people. It does not take much insight to conclude that data on these ubiquitous gizmos can provide potentially high value information. Even better, putting a software module on a mobile device of a person of interest can save time and expense. Modern intelligence gathering techniques are little more than using technology to minimize the need for humans sitting in automobiles or technicians planting listening devices in interesting locations. The other benefits of technology include real time or near real time data acquisition, geo-location data, access to the digital information about callers and email pals, and data available to the mobile’s ever improving cameras and microphones.
The write up points out:
One message, one link, one click. That’s all it takes to lose control of your digital life, unwittingly and in a matter of seconds.
The write up is story focused, probably because a podcast or a streaming video documentary was in the back of the mind of the writers and possibly Spiegel International itself. If you like write ups that have a slant, you will find the cited article interesting.
I want to mentions several facets of the write up which get less attention from “real” journalists.
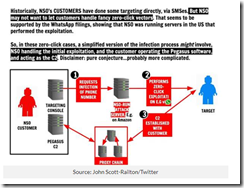
First, the story of the intelware dates back to the late 1970s. Obviously some of the technology has been around for decades, although refined over time. If this “shady” technology were a problem, why has it persisted, been refined, and pressed into service around the world by many countries? It is tempting to focus on a current activity because it makes a good story, but the context and longevity of some of the systems and methods are interesting to me. But 40 years?
Second, in the late 1970s and the block diagrams I have seen presenting the main features of the Amesys system (i2e Technologies) and its direct descendants have had remarkable robustness. In fact, were one to look at the block diagram for a system provided to a controversial government in North Africa and one of the NSO Group Pegasus block diagrams, the basics are retained. Why? A good engineering solution is useful even thought certain facets of the system are improved with modern technology. What’s this mean? From my point of view, the clever individual or group eager to replicate this type of stealth intelware can do it, just with modern tools and today’s robust cloud environment. The cloud was not a “thing” in 1980, but today it is a Teflon for intelware. This means quicker, faster, better, cheaper, and smarter with each iteration.
Source: IT News in Australia
Third, this particular type of intelware is available from specialized software companies worldwide. Want to buy a version from a developer in Spain? No problem. How about a Chinese variety? Cultivate your contacts in Hong Kong or Singapore and your wish will be granted. What about a version from an firm based in India? No problem, just hang out at telecommunications conference in Mumbai.
Net net: Newer and even more stealthy intelware technologies are available today. Will these be described and stories about the use of them be written? Yep. Will I identify some of these firms? Sure, just attend one of my lectures for law enforcement and intelligence professionals. But the big question is never answered, “Why are these technologies demonstrating such remarkable magnetic appeal?” And a related question, “Why do governments permit these firms to operate?”
Come on, Spiegel International. Write about a more timely approach, not one that is decades old and documented in detail on publicly accessible sources. Oh, is location tracking enabled on your phone to obviate some of the value of Signal, Telegram, and Threema encrypted messaging apps?
PS. Now no clicks are needed. The technology can be deployed when a mobile number is known and connected to a network. There is an exception too. The requisite code can be pre-installed on one’s mobile device. Is that a story? Nah, that cannot be true. I agree.
Stephen E Arnold, October 11, 2023
Newly Emerged Snowden Revelations Appear in Dutch Doctoral Thesis
October 10, 2023
![Vea4_thumb_thumb_thumb_thumb_thumb_t[2] Vea4_thumb_thumb_thumb_thumb_thumb_t[2]](https://arnoldit.com/wordpress/wp-content/uploads/2023/10/Vea4_thumb_thumb_thumb_thumb_thumb_t2_thumb-3.gif) Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
One Eddie Snowden (a fine gent indeed) rumor said that 99 percent of the NSA data Edward Snowden risked his neck to expose ten years ago remains unpublished. Some entities that once possessed that archive are on record as having destroyed it. This includes The Intercept, which was originally created specifically to publish its revelations. So where are the elusive Snowden files now? Could they be In the hands of a post-PhD researcher residing in Berlin? Computer Weekly examines three fresh Snowden details that made their way into a doctoral thesis in its article, “New Revelations from the Snowden Archive Surface.” The thesis was written by American citizen Jacob Applebaum, who has since received his PhD from the Eindhoven University of Technology in the Netherlands. Reporter Stefania Maurizi summarizes:
“These revelations go back a decade, but remain of indisputable public interest:
- The NSA listed Cavium, an American semiconductor company marketing Central Processing Units (CPUs) – the main processor in a computer which runs the operating system and applications – as a successful example of a ‘SIGINT-enabled’ CPU supplier. Cavium, now owned by Marvell, said it does not implement back doors for any government.
- The NSA compromised lawful Russian interception infrastructure, SORM. The NSA archive contains slides showing two Russian officers wearing jackets with a slogan written in Cyrillic: ‘You talk, we listen.’ The NSA and/or GCHQ has also compromised Key European LI [lawful interception] systems.
- Among example targets of its mass surveillance program, PRISM, the NSA listed the Tibetan government in exile.”
Of public interest, indeed. See the write-up for more details on each point or, if you enjoy wading through academic papers, the thesis itself [pdf]. So how and when did Applebaum get his hands on information from the Snowden docs? Those details are not revealed, but we do know this much:
“In 2013, Jacob Appelbaum published a remarkable scoop for Der Spiegel, revealing the NSA had spied on Angela Merkel’s mobile phone. This scoop won him the highest journalistic award in Germany, the Nannen Prize (later known as the Stern Award). Nevertheless, his work on the NSA revelations, and his advocacy for Julian Assange and WikiLeaks, as well as other high-profile whistleblowers, has put him in a precarious condition. As a result of this, he has resettled in Berlin, where he has spent the past decade.”
Probably wise. Will most of the Snowden archive remain forever unpublished? Impossible to say, especially since we do not know how many copies remain and in whose hands.
Cynthia Murrell, October 10, 2023
Canada vs. Google: Not a Fair Hockey Game
October 9, 2023
![Vea4_thumb_thumb_thumb_thumb_thumb_t[2] Vea4_thumb_thumb_thumb_thumb_thumb_t[2]](https://arnoldit.com/wordpress/wp-content/uploads/2023/10/Vea4_thumb_thumb_thumb_thumb_thumb_t2_thumb.gif) Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
I get a bit of a thrill when sophisticated generalist executives find themselves rejected by high-tech wizards. An amusing example of “Who is in charge here?” appears in “Google Rejects Trudeau’s Olive Branch, Threatens News Link Block Over New Law.”
A seasoned high-tech executive explains that the laptop cannot retrieve Canadian hockey news any longer. Thanks, Microsoft Bing. Nice maple leaf hat.
The write up states:
Alphabet Inc.’s Google moved closer to blocking Canadians from viewing news links on its search engine, after it rejected government regulations meant to placate its concerns about an impending online content law.
Yep, Canada may not be allowed into the select elite of Google users with news. Why? Canada passed a law with which Google does not agree. Imagine. Canada wants Google to pay for accessing, scraping, and linking to Canadian news.
Canada does not understand who is in charge. The Google is the go-to outfit. If you don’t believe me, just ask some of those Canadian law enforcement and intelligence analysts what online system is used to obtain high-value information. Hint. It is not yandex.ru.
The write up adds:
Google already threatened to remove links to news, and tested blocking such content for a small percentage of users in Canada earlier this year. On Friday, it went further, implying a block could be imminent as the current regulations would force the company to participate in the mandatory bargaining process while it applies for exemption.
Will the Google thwart the Canadian government? Based on the importance of the Google system to certain government interests, a deal of some sort seems likely. But Google could just buy Canada and hire some gig workers to run the country.
Stephen E Arnold, October 9, 2023
Profits Over Promises: IBM Sells Facial Recognition Tech to British Government
September 18, 2023
Just three years after it swore off any involvement in facial recognition software, IBM has made an about-face. The Verge reports, “IBM Promised to Back Off Facial Recognition—Then it Signed a $69.8 Million Contract to Provide It.” Amid the momentous Black Lives Matter protests of 2020, IBM’s Arvind Krishna wrote a letter to Congress vowing to no longer supply “general purpose” facial recognition tech. However, it appears that is exactly what the company includes within the biometrics platform it just sold to the British government. Reporter Mark Wilding writes:
“The platform will allow photos of individuals to be matched against images stored on a database — what is sometimes known as a ‘one-to-many’ matching system. In September 2020, IBM described such ‘one-to-many’ matching systems as ‘the type of facial recognition technology most likely to be used for mass surveillance, racial profiling, or other violations of human rights.'”
In the face of this lucrative contract IBM has changed its tune. It now insists one-to-many matching tech does not count as “general purpose” since the intention here is to use it within a narrow scope. But scopes have a nasty habit of widening to fit the available tech. The write-up continues:
“Matt Mahmoudi, PhD, tech researcher at Amnesty International, said: ‘The research across the globe is clear; there is no application of one-to-many facial recognition that is compatible with human rights law, and companies — including IBM — must therefore cease its sale, and honor their earlier statements to sunset these tools, even and especially in the context of law and immigration enforcement where the rights implications are compounding.’ Police use of facial recognition has been linked to wrongful arrests in the US and has been challenged in the UK courts. In 2019, an independent report on the London Metropolitan Police Service’s use of live facial recognition found there was no ‘explicit legal basis’ for the force’s use of the technology and raised concerns that it may have breached human rights law. In August of the following year, the UK’s Court of Appeal ruled that South Wales Police’s use of facial recognition technology breached privacy rights and broke equality laws.”
Wilding notes other companies similarly promised to renounce facial recognition technology in 2020, including Amazon and Microsoft. Will governments also be able to entice them into breaking their vows with tantalizing offers?
Cynthia Murrell, September 18, 2023
Can Smart Software Get Copyright? Wrong?
September 15, 2023
It is official: copyrights are for humans, not machines. JD Supra brings us up to date on AI and official copyright guidelines in, “Using AI to Create a Work – Copyright Protection and Infringement.” The basic principle goes both ways. Creators cannot copyright AI-generated material unless they have manipulated it enough to render it a creative work. On the other hand, it is a violation to publish AI-generated content that resembles a copyright-protected work. As for feeding algorithms a diet of human-made media, that is not officially against the rules. Yet. We learn:
“To obtain copyright protection for a work containing AI-generated material, the work must have sufficient human input, such as sufficient modification of the AI output or the human selection or arrangement of the AI content. However, copyright protection would be limited to those ‘human-made’ elements. Past, pending, and future copyright applications need to identify explicitly the human element and disclaim the AI-created content if it is more than minor. For existing registrations, a supplementary registration may be necessary. Works created using AI are subject to the same copyright infringement analysis applicable to any work. The issue with using AI to create works is that the sources of the original works may not be identified, so an infringement analysis cannot be conducted until the cease-and-desist letter is received. No court has yet adopted the theory that merely using an AI database means the resulting work is automatically an infringing derivative work if it is not substantially similar to the protectable elements in the copyrighted work.”
The article cites the Copyright Registration Guidance: Works Containing Material Generated by Artificial Intelligence, 88 Fed. Reg. 16,190 (March 16, 2023). It notes those guidelines were informed by a decision handed down in February, Zarya v Dawn, which involved a comic book with AI-generated content. the Copyright Office sliced and diced elements, specifying:
“… The selection and arrangement of the images and the text were the result of human authorship and thus copyrightable, but the AI-generated images resulting from human prompts were not. The prompts ‘influenced,’ but did not ‘dictate,’ the resulting image, so the applicant was not the ‘mastermind’ and therefore not the author of the images. Further, the applicant’s edits to the images were too minor to be deemed copyrightable.”
Ah, the fine art of splitting hairs. As for training databases packed with protected content, the article points to pending lawsuits by artists against Stability AI, MidJourney, and Deviant Art. We are told those cases may be dismissed on technical grounds, but are advised to watch for similar cases in the future. Stay tuned.
Cynthia Murrell, September 15, 2023
Regulating Smart Software: Let Us Form a Committee and Get Industry Advisors to Help
September 1, 2023
 Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
The Boston Globe published what I thought was an amusing “real” news story about legislators and smart software. I know. I know. I am entering oxymoron land. The article is “The US Regulates Cars, Radio, and TV. When Will It Regulate AI? A number of passages received True Blue check marks.
A person living off the grid works to make his mobile phone deliver generative content to solve the problem of … dinner. Thanks, MidJourney. You did a Stone Age person but you would not generate a street person. How helpful!
Let me share two passages and then offer a handful of observations.
How about this statement attributed to Microsoft’s Brad Smith. He is the professional who was certain Russia organized 1,000 programmers to figure out the SolarWinds’ security loopholes. Yes, that Brad Smith. The story quotes him as saying:
“We should move quickly,” Brad Smith, the president of Microsoft, which launched an AI-powered version of its search engine this year, said in May. “There’s no time for waste or delay,” Chuck Schumer, the Senate majority leader, has said. “Let’s get ahead of this,” said Sen. Mike Rounds, R-S.D.
Microsoft moved fast. I think the reason was to make Google look stupid. Both of these big outfits know that online services aggregate and become monopolistic. Microsoft wants to be the AI winner. Microsoft is not spending extra time helping elected officials understand smart software or the stakes on the digital table. No way.
The second passage is:
Historically, regulation often happens gradually as a technology improves or an industry grows, as with cars and television. Sometimes it happens only after tragedy.
Please, read the original “real” news story for Captain Obvious statements. Here are a few observations:
- Smart software is moving along at a reasonable clip. Big bucks are available to AI outfits in Germany and elsewhere. Something like 28 percent of US companies are fiddling with AI. Yep, even those raising chickens have AI religion.
- The process of regulation is slow. We have a turtle and a hare situation. Nope, the turtle loses unless an exogenous power kills the speedy bunny.
- If laws were passed, how would one get fast action to apply them? How is the FTC doing? What about the snappy pace of the CDC in preparing for the next pandemic?
Net net: Yes, let’s understand AI.
Stephen E Arnold, September 1, 2023.
The statement aligns with my experience.
Calls for AI Pause Futile At this Late Date
August 29, 2023
 Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Note: This essay is the work of a real and still-alive dinobaby. No smart software involved, just a dumb humanoid.
Well, the nuclear sub has left the base. A group of technology experts recently called for a 6-month pause on AI rollouts in order to avoid the very “loss of control of our civilization” to algorithms. That might be a good idea—if it had a snowball’s chance of happening. As it stands, observes ComputerWorld‘s Rob Enderle, “Pausing AI Development Is a Foolish Idea.” We think foolish is not a sufficiently strong word. Perhaps regulation could have been established before the proverbial horse left the barn, but by now there are more than 500 AI startups according to Jason Calacanis, noted entrepreneur and promoter.
A sad sailor watches the submarine to which he was assigned leave the dock without him. Thanks, MidJourney. No messages from Mother MJ on this image.
Enderle opines as a premier pundit:
“Once a technology takes off, it’s impossible to hold back, largely because there’s no strong central authority with the power to institute a global pause — and no enforcement entity to ensure the pause directive is followed. The right approach would be to create such an authority beforehand, so there’s some way to assure the intended outcome. I tend to agree with former Microsoft CEO Bill Gates that the focus should be on assuring AI reliability, not trying to pause everything. … There simply is no global mechanism to enforce a pause in any technological advance that has already reached the market.”
We are reminded that even development on clones, which is illegal in most of the world, continues apace. The only thing bans seem to have accomplished there is to obliterate transparency around cloning projects. There is simply no way to rein in all the world’s scientists. Not yet. Enderle offers a grain of hope on artificial intelligence, however. He notes it is not too late to do for general-purpose AI what we failed to do for generative AI:
“General AI is believed to be more than a decade in the future, giving us time to devise a solution that’s likely closer to a regulatory and oversight body than a pause. In fact, what should have been proposed in that open letter was the creation of just such a body. Regardless of any pause, the need is to ensure that AI won’t be harmful, making oversight and enforcement paramount. Given that AI is being used in weapons, what countries would allow adequate third-party oversight? The answer is likely none — at least until the related threat rivals that of nuclear weapons.”
So we have that to look forward to. And clones, apparently. The write-up points to initiatives already in the works to protect against “hostile” AI. Perhaps they will even be effective.
Cynthia Murrell, August 16, 2023