Want to Catch the Attention of Bad Actors? Say, Easier Cross Chain Transactions
September 24, 2025
 This essay is the work of a dumb dinobaby. No smart software required.
This essay is the work of a dumb dinobaby. No smart software required.
I know from experience that most people don’t know about moving crypto in a way that makes deanonymization difficult. Commercial firms offer deanonymization services. Most of the well-known outfits’ technology delivers. Even some home-grown approaches are useful.
For a number of years, Telegram has been the go-to service for some Fancy Dancing related to obfuscating crypto transactions. However, Telegram has been slow on the trigger when it comes to smart software and to some of the new ideas percolating in the bubbling world of digital currency.
A good example of what’s ahead for traders, investors, and bad actors is described in “Simplifying Cross-Chain Transactions Using Intents.” Like most crypto thought, confusing lingo is a requirement. In this article, the word “intent” refers to having crypto currency in one form like USDC and getting 100 SOL or some other crypto. The idea is that one can have fiat currency in British pounds, walk up to a money exchange in Berlin, and convert the pounds to euros. One pays a service charge. Now in crypto land, the crypto has to move across a blockchain. Then to get the digital exchange to do the conversion, one pays a gas fee; that is, a transaction charge. Moving USDC across multiple chains is a hassle and the fees pile up.
The article “Simplifying Cross Chain Transaction Using Intents” explains a brave new world. No more clunky Telegram smart contracts and bots. Now the transaction just happens. How difficult will the deanonymization process become? Speed makes life difficult. Moving across chains makes life difficult. It appears that “intents” will be a capability of considerable interest to entities interested in making crypto transactions difficult to deanonymize.
The write up says:
In technical terms,
intentsare signed messages that express a user’s desired outcome without specifying execution details. Instead of crafting complex transaction sequences yourself, you broadcast your intent to a network ofsolvers(sophisticated actors) who then compete to fulfill your request.
The write up explains the benefit for the average crypto trader:
when you broadcast an intent, multiple solvers analyze it and submit competing quotes. They might route through different DEXs, use off-chain liquidity, or even batch your intent with others for better pricing. The best solution wins.
Now, think of solvers as your personal trading assistants who understand every connected protocol, every liquidity source, and every optimization trick in DeFi. They make money by providing better execution than you could achieve yourself and saves you a a lot of time.
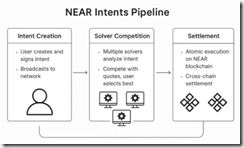
Does this sound like a use case for smart software? It is, but the approach is less complicated than what one must implement using other approaches. Here’s a schematic of what happens in the intent pipeline:
The secret sauce for the approach is what is called a “1Click API.” The API handles the plumbing for the crypto bridging or crypto conversion from currency A to currency B.
If you are interested in how this system works, the cited article provides a list of nine links. Each provides additional detail. To be up front, some of the write ups are more useful than others. But three things are clear:
- Deobfuscation is likely to become more time consuming and costly
- The system described could be implemented within the Telegram blockchain system as well as other crypto conversion operations.
- The described approach can be further abstracted into an app with more overt smart software enablements.
My thought is that money launderers are likely to be among the first to explore this approach.
Stephen E Arnold, September 24, 2025
Scattered Spider: Operating Freely Despite OSINT and Specialized Investigative Tools. Why?
July 7, 2025
 No smart software to write this essay. This dinobaby is somewhat old fashioned.
No smart software to write this essay. This dinobaby is somewhat old fashioned.
I don’t want to create a dust up in the specialized software sector. I noted the July 2, 2025, article “A Group of Young Cybercriminals Poses the Most Imminent Threat of Cyberattacks Right Now.” That story surprised me. First, the Scattered Spider group was documented (more or less) by Trellix, a specialized software and services firm. You can read the article “Scattered Spider: The Modus Operandi” and get a sense of what Trellix reported. The outfit even has a Wikipedia article about their activities.
Last week I was asked a direct question, “Which of the specialized services firms can provide me with specific information about Telegram Groups and Channels, both public and private?” My answer, “None yet.”
Scattered Spider uses Telegram for some messaging functions, and if you want to get a sense of what the outfit does, just fire up your OSINT tools or better yet use one of the very expensive specialized services available to government agencies. The young cybercriminals appear to use the alias @ScatteredSpiderERC.” There is a Wikipedia article about this group’s activities.
So what? Let’s go back to the question addressed directly to me about firms that have content about Telegram. If we assume the Wikipedia write up is sort of correct, the Scattered Spider entity popped up in 2022 and its activities caught the attention of Trellix. The time between the Trellix post and the Wired story is about two years.
Why has a specialized services firm providing actionable data to the US government, the Europol investigators, and the dozens of others law enforcement operations around the world? Isn’t it a responsible act to use that access to Telegram data to take down outfits that endanger casinos and other organizations?
Apparently the answer is, “No.”
My hunch is that these specialized software firms talk about having tools to access Telegram. That talk is a heck of a lot easier than finding a reliable way to access private Groups and Channels, trace a handle back to a real live human being possibly operating in the EU or the US. I would suggest that France tried to use OSINT and the often nine figure systems to crack Telegram. Will other law enforcement groups realize that the specialized software vendors’ tools fall short of the mark and think about a France-type of response?
France seems to have made a dent in Telegram. I would hypothesize that the failure of OSINT and the specialized software tool vendors contributed to France’s decision to just arrest Pavel Durov. Mr. Durov is now ensnared in France’s judicial bureaucracy. To make the arrest more complex for Mr. Durov, he is a citizen of France and a handful of other countries, including Russia and the United Arab Emirates.
I mention this lack of Telegram cracking capability for three reasons:
- Telegram is in decline and the company is showing some signs of strain
- The changing attitude toward crypto in the US means that Telegram absolutely has to play in that market or face either erosion or decimation of its seven year push to create alternative financial services based on TONcoin and Pavel Durov’s partners’ systems
- Telegram is facing a new generation of messaging competitors. Like Apple, Telegram is late to the AI party.
One would think that at a critical point like this, the Shadow Server account would be a slam dunk for any licensee of specialized software advertising, “Telegram content.”
Where are those vendors who webinars, email blasts, and trade show demonstrations? Where are the testimonials that Company Nuco’s specialized software really did work. “Here’s what we used in court because the specialized vendor’s software generated this data for us” is what I want to hear. I would suggest that Telegram remains a bit of a challenge to specialized software vendors. Will I identify these “big hat, no cattle outfits”? Nope.
Just thought that a reminder that marketing and saying what government professionals want to hear are easier than just talking.
Stephen E Arnold, July 2025
Telegram Lecture at TechnoSecurity & Digital Forensics on June 4, 2025
April 3, 2025
 No AI. Just a dinobaby sharing an observation about younger managers and their innocence.
No AI. Just a dinobaby sharing an observation about younger managers and their innocence.
The organizers of the June 2025 TechnoSecurity & Digital Forensics Conference posted a 60 second overview of our Telegram Overview lecture on LinkedIn. You can view the conference’s 60 second video at https://lnkd.in/eTSvpYFb. Erik and I have been doing presentations on specific Telegram subjects for law enforcement groups. Two weeks ago, we provided to the Massachusetts Association of Crime Analysts a 60-minute run down about the technical architecture of Telegram and identified three US companies providing services to Telegram. To discuss a presentation for your unit, please, message me via LinkedIn. (Plus, my son and I are working to complete our 100 page PDF notes of our examination of Telegram’s more interesting features. These range from bots which automate cross blockchain crypto movement to the automatic throttling function in the Telegram TON Virtual Machine to prevent transaction bottlenecks in complex crypto wallet obfuscations.) See you there. — Thank you, Stephen E Arnold, April 3, 2025, 223 pm U S Eastern
More about NAMER, the Bitext Smart Entity Technology
January 14, 2025
 A dinobaby product! We used some smart software to fix up the grammar. The system mostly worked. Surprised? We were.
A dinobaby product! We used some smart software to fix up the grammar. The system mostly worked. Surprised? We were.
We spotted more information about the Madrid, Spain based Bitext technology firm. The company posted “Integrating Bitext NAMER with LLMs” in late December 2024. At about the same time, government authorities arrested a person known as “Broken Tooth.” In 2021, an alert for this individual was posted. His “real” name is Wan Kuok-koi, and he has been in an out of trouble for a number of years. He is alleged to be part of a criminal organization and active in a number of illegal behaviors; for example, money laundering and human trafficking. The online service Irrawady reported that Broken Tooth is “the face of Chinese investment in Myanmar.”
Broken Tooth (né Wan Kuok-koi, born in Macau) is one example of the importance of identifying entity names and relating them to individuals and the organizations with which they are affiliated. A failure to identify entities correctly can mean the difference between resolving an alleged criminal activity and a get-out-of-jail-free card. This is the specific problem that Bitext’s NAMER system addresses. Bitext says that large language models are designed for for text generation, not entity classification. Furthermore, LLMs pose some cost and computational demands which can pose problems to some organizations working within tight budget constraints. Plus, processing certain data in a cloud increases privacy and security risks.
Bitext’s solution provides an alternative way to achieve fine-grained entity identification, extraction, and tagging. Bitext’s solution combines classical natural language processing solutions solutions with large language models. Classical NLP tools, often deployable locally, complement LLMs to enhance NER performance.
NAMER excels at:
- Identifying generic names and classifying them as people, places, or organizations.
- Resolving aliases and pseudonyms.
- Differentiating similar names tied to unrelated entities.
Bitext supports over 20 languages, with additional options available on request. How does the hybrid approach function? There are two effective integration methods for Bitext NAMER with LLMs like GPT or Llama are. The first is pre-processing input. This means that entities are annotated before passing the text to the LLM, ideal for connecting entities to knowledge graphs in large systems. The second is to configure the LLM to call NAMER dynamically.
The output of the Bitext system can generate tagged entity lists and metadata for content libraries or dictionary applications. The NAMER output can integrate directly into existing controlled vocabularies, indexes, or knowledge graphs. Also, NAMER makes it possible to maintain separate files of entities for on-demand access by analysts, investigators, or other text analytics software.
By grouping name variants, Bitext NAMER streamlines search queries, enhancing document retrieval and linking entities to knowledge graphs. This creates a tailored “semantic layer” that enriches organizational systems with precision and efficiency.
For more information about the unique NAMER system, contact Bitext via the firm’s Web site at www.bitext.com.
Stephen E Arnold, January 14, 2025
FOGINT: Big Takedown Coincident with Durov Detainment. Coincidence?
December 19, 2024
 This blog post is the work of an authentic dinobaby. No smart software was used.
This blog post is the work of an authentic dinobaby. No smart software was used.
In recent years, global authorities have taken down several encrypted communication channels. Exclu and Ghost, for example. Will a more fragmented approach keep the authorities away? Apparently not. A Europol press release announces, “International Operation Takes Down Another Encrypted Messaging Service Used by Criminals.” The write-up notes:
“Criminals, in response to the disruptions of their messaging services, have been turning to a variety of less-established or custom-built communication tools that offer varying degrees of security and anonymity. While the new fragmented landscape poses challenges for law enforcement, the takedown of established communication channels shows that authorities are on top of the latest technologies that criminals use.”
Case in point: After a three-year investigation, a multi-national law enforcement team just took down MATRIX. The service, “by criminals for criminals,” was discovered in 2021 on a convicted murderer’s phone. It was a sophisticated tool bad actors must be sad to lose. We learn:
“It was soon clear that the infrastructure of this platform was technically more complex than previous platforms such as Sky ECC and EncroChat. The founders were convinced that the service was superior and more secure than previous applications used by criminals. Users were only able to join the service if they received an invitation. The infrastructure to run MATRIX consisted of more than 40 servers in several countries with important servers found in France and Germany. Cooperation between the Dutch and French authorities started through a JIT set up at Eurojust. By using innovative technology, the authorities were able to intercept the messaging service and monitor the activity on the service for three months. More than 2.3 million messages in 33 languages were intercepted and deciphered during the investigation. The messages that were intercepted are linked to serious crimes such as international drug trafficking, arms trafficking, and money laundering. Actions to take down the service and pursue serious criminals happened on 3 December in four countries.”
Those four countries are France, Spain, Lithuania, and Germany, with an assist by the Netherlands. Interpol highlights the importance of international cooperation in fighting organized crime. Is this the key to pulling ahead in the encryption arms race?
Cynthia Murrell, December 19, 2024
FOGINT: Telegram Steps Up Its Cooperation with Law Enforcement
December 12, 2024
 This short item is the work of the dinobaby. The “fog” is from Gifr.com.
This short item is the work of the dinobaby. The “fog” is from Gifr.com.
Engadget, an online news service, reported “Telegram Finally Takes Action to Remove CSAM from Its Platform.” France picks up Telegram founder Pavel Durov and explains via his attorney how the prison system works in the country. Mr. Durov, not yet in prison, posted an alleged Euro 5 million with the understanding he could not leave the country. According to Engadget, Mr. Durov is further modifying his attitude toward “free speech” and “freedom.”
The article states:
Telegram is taking a significant step to reduce child sexual abuse material (CSAM), partnering with the International Watch Foundation (IWF) four months after the former’s founder and CEO Pavel Durov was arrested. The French authorities issued 12 charges against Durov in August, including complicity in “distributing, offering or making available pornographic images of minors, in an organized group” and “possessing pornographic images of minors.”
For those not familiar with the International Watch Foundation, the organization serves as a “hub” for law enforcement and companies acting as intermediaries for those engaged in buying, leasing, selling, or exchanging illicit images or videos of children. Since 2013, Telegram has mostly been obstinate when asked to cooperate with investigators. The company has waved its hands and insisted that it is not into curtailing free speech.
After the French snagged Mr. Durov, he showed a sudden interest in cooperating with authorities. The Engadget report says:
Telegram has taken other steps since Durov’s arrest, announcing in September that it would hand over IP addresses and phone numbers in legal requests — something it fought in the past. Durov must remain in France for the foreseeable future.
What’s Telegram going to do after releasing handles, phone numbers, and possibly some of that log data allegedly held in servers available to the company? The answer is, “Telegram is pursuing its next big thing.” Engadget does not ask, “What’s Telegram’s next act?” Surprisingly a preview of Telegram’s future is unfolding in TON Foundation training sessions in Vancouver, Istanbul, and numerous other locations.
But taking that “real” work next step is not in the cards for most Telegram watchers. The “finally” is simply bringing down the curtain of Telegram’s first act. More acts are already on stage.
Stephen E Arnold, December 12, 2024
Dark Web: Clever and Cute Security Innovations
December 11, 2024
 This write up was created by an actual 80-year-old dinobaby. If there is art, assume that smart software was involved. Just a tip.
This write up was created by an actual 80-year-old dinobaby. If there is art, assume that smart software was involved. Just a tip.
I am not sure how the essay / technical analysis “The Fascinating Security Model of Dark Web Marketplaces” will diffuse within the cyber security community. I want to highlight what strikes me as a useful analysis and provide a brief, high-level summary of the points which my team and I found interesting. We have not focused on the Dark Web since we published Dark Web Notebook, a complement to my law enforcement training sessions about the Dark Web in the period from 2013 to 2016.
This write up does a good job of explaining use of open source privacy tools like Pretty Good Privacy and its two-factor authentication. The write up walks through a “no JavaScript” approach to functions on the Dark Web site. The references to dynamic domain name operations is helpful as well.
The first observation I would offer is that in the case of the Dark Web site analyzed in the cited article is that the security mechanisms in use have matured and, in the opinion of my research team, advanced to thwart some of the techniques used to track and take down the type of sites hosted by Cyberbunker in Germany. This is — alas — inevitable, and it makes the job of investigators more difficult.
The second observation is that this particular site makes use of distributed services. With the advent of certain hosting providers to offer self managed virtual servers and a professed inability to know what’s happening on physical machines. Certain hosting providers “comply” and then say, “If you try to access the virtual machines, they can fail. Since we don’t manage them, you guys will have to figure out how to get them back up.” Cute and effective.
The third observation is that the hoops through which a potential drug customer has to get through are likely to make a person with an addled brain get clean and then come back and try again. On the other hand, the Captcha might baffle a sober user or investigator as well. Cute and annoying.
The essay is useful and worth reading because it underscores the value of fluid online infrastructures for bad actors.
Stephen E Arnold, December 11, 2024
Explaining Graykey: Helpful or Harmful for Law Enforcement?
November 25, 2024
I am not keen on making some “secrets” publicly available. Those keen on channeling Edward Snowden may have glory words to describe their activities. I take a different view: Some types of information should be proprietary and made known only to those engaged in trying to enforce applicable laws. That said, I want to point to a Reddit.com post about “privacy.” The trigger for the post is an article behind a paywall about a device used to extract information from a mobile phone.
The Reddit post provides a link to the source document “Leaked Documents Show What Phones Secretive Tech ‘Graykey’ Can Unlock”. That write up is typical of non-LE and intel professional reactions to certain types of specialized software and hardware.
What I want to mention is that the Reddit post provides some supplementary information which is not widely known and generally not bandied about outside of certain professional groups. You can find this post, the links to the additional information, and some commentary to disambiguate the jargon used to keep chatter about specialized products and services within a “community.” Here’s the link to the Reddit information: https://shorturl.at/KsDwc
To be frank, I miss the good old days when information of a sensitive nature did not become course material for a computer science and programming class or a road map for outfits competing with US firms. But I am a dinobaby. Believe me, no one cares about my old-timey thoughts.
Stephen E Arnold, November 25, 2024
Entity Extraction: Not As Simple As Some Vendors Say
November 19, 2024
 No smart software. Just a dumb dinobaby. Oh, the art? Yeah, MidJourney.
No smart software. Just a dumb dinobaby. Oh, the art? Yeah, MidJourney.
Most of the systems incorporating entity extraction have been trained to recognize the names of simple entities and mostly based on the use of capitalization. An “entity” can be a person’s name, the name of an organization, or a location like Niagara Falls, near Buffalo, New York. The river “Niagara” when bound to “Falls” means a geologic feature. The “Buffalo” is not a Bubalina; it is a delightful city with even more pleasing weather.
The same entity extraction process has to work for specialized software used by law enforcement, intelligence agencies, and legal professionals. Compared to entity extraction for consumer-facing applications like Google’s Web search or Apple Maps, the specialized software vendors have to contend with:
- Gang slang in English and other languages; for example, “bumble bee.” This is not an insect; it is a nickname for the Latin Kings.
- Organizations operating in Lao PDR and converted to English words like Zhao Wei’s Kings Romans Casino. Mr. Wei has been allegedly involved in gambling activities in a poorly-regulated region in the Golden Triangle.
- Individuals who use aliases like maestrolive, james44123, or ahmed2004. There are either “real” people behind the handles or they are sock puppets (fake identities).
Why do these variations create a challenge? In order to locate a business, the content processing system has to identify the entity the user seeks. For an investigator, chopping through a thicket of language and idiosyncratic personas is the difference between making progress or hitting a dead end. Automated entity extraction systems can work using smart software, carefully-crafted and constantly updated controlled vocabulary list, or a hybrid system.
Automated entity extraction systems can work using smart software, carefully-crafted and constantly updated controlled vocabulary list, or a hybrid system.
Let’s take an example which confronts a person looking for information about the Ku Group. This is a financial services firm responsible for the Kucoin. The Ku Group is interesting because it has been found guilty in the US for certain financial activities in the State of New York and by the US Securities & Exchange Commission.
Pavel Durov and Telegram: In the Spotlight Again
October 21, 2024
 No smart software used for the write up. The art, however, is a different story.
No smart software used for the write up. The art, however, is a different story.
Several news sources reported that the entrepreneurial Pavel Durov, the found of Telegram, has found a way to grab headlines. Mr. Durov has been enjoying a respite in France, allegedly due to his contravention of what the French authorities views as a failure to cooperate with law enforcement. After his detainment, Mr. Durov signaled that he has cooperated and would continue to cooperate with investigators in certain matters.
A person under close scrutiny may find that the experience can be unnerving. The French are excellent intelligence operators. I wonder how Mr. Durov would hold up under the ministrations of Israeli and US investigators. Thanks, ChatGPT, you produced a usable cartoon with only one annoying suggestion unrelated to my prompt. Good enough.
Mr. Durov may have an opportunity to demonstrate his willingness to assist authorities in their investigation into documents published on the Telegram Messenger service. These documents, according to such sources as Business Insider and South China Morning Post, among others, report that the Telegram channel Middle East Spectator dumped information about Israel’s alleged plans to respond to Iran’s October 1, 2024, missile attack.
The South China Morning Post reported:
The channel for the Middle East Spectator, which describes itself as an “open-source news aggregator” independent of any government, said in a statement that it had “received, through an anonymous source on Telegram who refused to identify himself, two highly classified US intelligence documents, regarding preparations by the Zionist regime for an attack on the Islamic Republic of Iran”. The Middle East Spectator said in its posted statement that it could not verify the authenticity of the documents.
Let’s look outside this particular document issue. Telegram’s mostly moderation-free approach to the content posted, distributed, and pushed via the Telegram platform is like to come under more scrutiny. Some investigators in North America view Mr. Durov’s system as a less pressing issue than the content on other social media and messaging services.
This document matter may bring increased attention to Mr. Durov, his brother (allegedly with the intelligence of two PhDs), the 60 to 80 engineers maintaining the platform, and its burgeoning ancillary interests in crypto. Mr. Durov has some fancy dancing to do. One he is able to travel, he may find that additional actions will be considered to trim the wings of the Open Network Foundation, the newish TON Social service, and the “almost anything” goes approach to the content generated and disseminated by Telegram’s almost one billion users.
From a practical point of view, a failure to exercise judgment about what is allowed on Messenger may derail Telegram’s attempts to become more of a mover and shaker in the world of crypto currency. French actions toward Mr. Pavel should have alerted the wizardly innovator that governments can and will take action to protect their interests.
Now Mr. Durov is placing himself, his colleagues, and his platform under more scrutiny. Close scrutiny may reveal nothing out of the ordinary. On the other hand, when one pays close attention to a person or an organization, new and interesting facts may be identified. What happens then? Often something surprising.
Will Mr. Durov get that message?
Stephen E Arnold, October 21, 2024