Forget AI Bias: Outputs May Just Be Wrong
March 29, 2022
I read a “real” news story which caused me to whip out my stack of 4×6 note cards and jot down some statements and phrases. May I share six examples? (Permission denied? Well, too bad, gentle reader, too too bad.)
- “Too good to be true”
- “Overly optimistic results”
- “The images may look excellent, but they are inaccurate.”
- “Important details… could be completely missing”
- “Results cannot be reproduced”
- “Data crimes”
If you want to see these statements in allegedly objective context, navigate to “‘Off Label’ Use of Imaging Databases Could Lead to Bias in AI Algorithms, Study Finds.” For the intellectually hardy, the original “research” paper is at this link, at least as of March 25, 2022, at 0500 am US Eastern.
The main idea is that short cuts, use of widely used public data, and eagerness to be a winner appear to be a characteristic of some Fancy Dan machine learning methods. (Hello, Stanford AI Laboratory, wearing a Snorkel today?)
Implications? One’s point of view colors the information in the article. Is the article accurate, chock full of reproducible results?
There’s something called a viewshed or its quizlet. Depending on one’s location, certain important objects or concepts may not be in the picture. Does it matter? Only if the autonomous agent sends a smart system through one’s garden party. No manners, no apologies, and no consequences or at least significant consequences, right? Sail on, tally ho, and so forth.
Stephen E Arnold, March 29, 2022
Open Source Software: Do Flashing Neon Signs Say, Bad Actors Welcome?
March 29, 2022
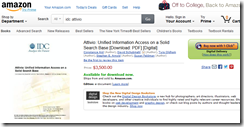
Remember when IDC, one of the units of the Patrick McGovern empire, was a big dog. Before the research unit wound up with swamp mud on its discount sneakers, one of the self-appointed experts suggested my team assemble a big report about — wait for it — open source search. We assembled our data, created profiles similar to those available on my Web site www.xenky.com/vendor-reports, and provided drafts to the estimable IDC. We learned, quite to my surprise, that several of these drafts were listed on Amazon.com for $3,000 each. We did not have a contract, and IDC had no permission to do anything with our profiles of about a dozen open source search solutions. Quite sporty behavior for “the premier global provider of marketing intelligence, advisory services, and events for the information technology, telecommunications, and consumer technology markets.” One IDC expert informed me that the company was called Foundry now. Yeah, who knew?
How do I know IDC sold my work on Amazon without an agreement from me? Check this out:
One take away from our book about open source search software was that security was an afterthought. Did users of open source software think about security? Nope. The users thought about how much money would be saved relying on a “community.” Users like the idea of not having proprietary software companies prevent changes to the code. Security was a community responsibility. Easy assumptions for users who wanted flexibility, reduced costs, and a false sense of no worries about this code.
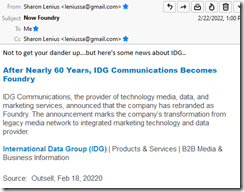
Does the big outfit which violated my copyright and stole my intellectual property care? The information about the lack of security in an enterprise open source software sector was effectively killed. Here’s an email I received in February 2022. You judge what’s shakin’.
The author is in some way affiliated to Foundry. The entity is called Sharon Lenius, and I assume she will respond to email sent to her at leniussa@gmail.com. Let’s hope she receives a lot of email.
Why this jaunt through the history of IDC and open source search software? If the company had its well oiled second hand store slicker in tip top shape, the security weaknesses of open source search software. Furthermore, the reason open source search as well as other types of software were being adopted by big outfits was cost reduction. The big firms used what could be downloaded, assuming that the “community” would identify flaws, fix them, and assume the responsibilities companies should have shouldered themselves.
When I read “A Developer Altered Open Source Software to Wipe Files in Russia,” I thought “decade old news.” A decade! Do I care? The write up states:
The developer of a popular open source package has been caught adding malicious code to it, leading to wiped files on computers located in Russia and Belarus. The move was part of a protest that has enraged many users and raised concerns about the safety of free and open source software.
I think that the security problems now released as “real news” are significant. Security, code integrity, and malicious actions on the part of the community were not at the top of the to do list 10 years ago and are not at the top of the list today.
Is there a fix? Sure, but like most fixes, it is likely to be too little and too late. Like the self regulation of financial services firms, there is considerable room for creative thinking in the open source software sector. In my upcoming 2022 National Cyber Crime Conference lecture, I will point out specific open source tools which can be used to subvert systems relying on open source software. Why not create a malicious chunk of code, tuck it in a library, and allow an incurious 20 something to undermine an organization?
Why not relay on outfits like mid tier consulting firms to provide actionable information? Why not wait until an armed conflict highlights a ticking IED inside some of the most widely used enterprise applications? Why not act in an ethical, responsible way?
I will be dead and logged off permanently before these questions are answered.
Stephen E Arnold, March 29, 2022
KO for AO Kaspersky?
March 29, 2022
I read “Kaspersky Named First Russian Company on Security Risk List.” Interesting. The write up reports:
The U.S. placed internet-security provider AO Kaspersky Lab on a list of companies deemed a threat to national security, for the first time adding a Russian entity to a list dominated by Chinese telecommunications firms. The Federal Communications Commission on Friday also added China Telecom (Americas) Corp, and China Mobile International USA Inc. to the list.
Now let’s ask another question, “Which venture funding firms accept money from individuals who may have interesting connections?”
Do I see any hands?
No.
That’s my point. Kaspersky is an obvious outfit to probe. What’s the action for the dozens, maybe hundreds, of cyber security firms with non-obvious links to interesting sources of cash. Some bad actors buy yachts. Others villas. A few go for nifty jets. How many are into owning cyber security firms, having access to click PowerPoint decks making the future clear in designer graphics, and hanging out with other technical wizards just sharing casual info?
Who wants to ask, “Where did your money come from?”
Stephen E Arnold, March 29, 2022
DarkCyber, March 29, 2022: An Interview with Chris Westphal, DataWalk
March 29, 2022
Chris Westphal is the Chief Analytics Officer of DataWalk, a firm providing an investigative and analysis tool to commercial and government organizations. The 12-minute interview covers DataWalk’s unique capabilities, its data and information resources, and the firm’s workflow functionality. The video can be viewed on YouTube at this location.
Stephen E Arnold, March 29, 2022
Automated Censorship: What Could Go CENSORED with the CENSORED System?
March 28, 2022
Automated censorship: Silent, 24×7, no personnel hassles, no vacations, no breakdowns, and no worries.
Okay, a few may have worries, but these are very small, almost microscopic, worries. The reason? If one can’t find the information, then whatever the information discusses does not exist for many people. That’s the elegance of censorship. A void. No pushback. One does not know.
“How AI Is Creating a Safer Online World” does not worry about eliminating information. The argument is “more safety.” Who can disagree? Smart people understand that no information yields safety, right?
The write up states:
By using machine learning algorithms to identify and categorize content, companies can identify unsafe content as soon as it is created, instead of waiting hours or days for human review, thereby reducing the number of people exposed to unsafe content.
A net positive. The write up assumes that safe content is good. Smart software can recognize unsafe content. The AI can generate data voids which are safe.
The write up does acknowledge that there may be a tiny, probably almost insignificant issue. The article explains with brilliant prose:
Despite its promise, AI-based content moderation faces many challenges. One is that these systems often mistakenly flag safe content as unsafe, which can have serious consequences.
Do we need examples? Sure, let’s point out that the old chestnuts about Covid and politics are presented to close the issue. How are those examples playing out?
How does the write up? Logic that would knock Stephen Toulmin for a loop? A content marketing super play that will make the author and publisher drown in fame?
Nah, just jabber like this:
AI-assisted content moderation isn’t a perfect solution, but it’s a valuable tool that can help companies keep their platforms safe and free from harm. With the increasing use of AI, we can hope for a future where the online world is a safer place for all.
Does a “safer place” suggest I will be spared essays like this in the future? Oh, oh. Censorship practiced by a human: Ignoring content hoo hah. The original word I chose to characterize the analysis has been CENSORED.
Stephen E Arnold, March 28, 2022
Just A One Trick Pony Use Case for Clearview AI? Duh?
March 28, 2022
I read “Ukraine Uses Facial Recognition to Identify Dead Russian Soldiers, Minister Says.” If I were a minister, I suppose everything I might say would become a news story from a “trust” outfit. The write up reports that Clearview AI’s technology and image database will allow Ukraine to ID casualties. Then Ukraine will output the matches via social media. The write up makes clear that other questions were asked, but the minister did not comment. One factoid in the write up is that Clearview has an alleged two billion images scraped from VKontakte, the Russian Facebook.
A couple of points:
- The trust outfit publishing the one trick pony use case requires that one register to ingest the content.
- Will those in Ukraine use the technology to determine if a living Russian is trying to pass as a resident?
My clear view is that the more immediate use case for the system might be to focus on the living. Does that idea creep into the news report? Of course not, Thomson Reuters is not the New York Times.
Which is better the “we don’t comment on the obvious spin from the minister” or “the laptop content” shuffle? “Better” is the incorrect word. How about “different.”
Stephen E Arnold, March 28, 2022
Microsoft Help Files: Truly Helpful?
March 28, 2022
We are approaching April Fools’ Day. One company reliably provides a clever way to make me laugh. CHM? Do you know what the acronym means? No. It is a short hand way to say Compiled HTML Help file. CHH becomes CHM. Makes perfect sense to a Softie.
The tickled ribs result from bad actors using the CHM files to deliver malware. You can read the explanation and inspiration for bad actors in “Microsoft Help Files Disguise Vidar Malware.”
The write up states:
… the .ISO file contains a .CHM file named “pss10r.chm.” Towards the end of the file’s code is a snippet of HTML application (HTA) code containing JavaScript that covertly triggers a second file, “app.exe.” This is, in fact, Vidar malware. “One of the objects unpacked from the .CHM is the HTML file ‘PSSXMicrosoftSupportServices_HP05221271.htm’ — the primary object that gets loaded once the CHM pss10r.chm is opened,” according to the Trustwave writeup. “This HTML has a button object which automatically triggers the silent re-execution of the .CHM “pss10r.chm” with mshta.” Mshta is a Windows binary used for executing HTA files.
With the preliminaries out of the way the malware payload downloads, does some house cleaning, and phones home.
Microsoft, the go to solution for compromising security? Maybe. And what about Defender? What about the super smart cyber security systems from big name vendors. Yeah, how about those defenses?
Now we know there is one thing worse than the informational content of Microsoft help files.
Want to guess?
The Register reports that “Microsoft Azure developers targeted by 200 data stealing npm packages.” Not familiar with npm? NPM is a software registry and contains more than 750,000 code packages. Some open source developers use npm to share software. What if an npm code package has been modified so that malicious actions are included?
Yeah.
Stephen E Arnold, March 28, 2022
The Lapsus$ Gang: Teens or a Cyber Army?
March 28, 2022
I read “Who is LAPSUS$, the Big, Bad Cybercrime Gang Hacking Tech’s Biggest Companies?https://gizmodo.com/who-is-lapsus-the-gang-hacking-microsoft-samsung-an-1848686059” The write up answers the question this way:
British authorities announced the arrest of seven people said to be connected to the gang. Authorities revealed that the unidentified suspects ranged in age from 16 to 21. The ringleader of the gang is reputed to be a 16-year-old British kid from Oxford.
True? The wheels of justice in the UK must turn.
I have another angle. I processed this news story and thought about the assorted explanations offered from some high profile bad actor behaviors; for example, SolarWinds, Microsoft Exchange, Colonial Pipeline, et al.
Here with is my imaginary recreation of the Lapsus$ actions, just explained by luminaries from companies I enjoy following:
A Microsoft-type outfit opined, “Lapsus$ is a gang of more than 1,000 programmers who have labored intensively to compromise our highly secure ecosystem. This is the work of a nation state.
A US government cyber official affiliated with the White House said, “The predatory and dangerous behavior of an unprincipled gang under the direct orders of what might be called the Axis of Evil is undermining the national security of the United States. A failure to follow the 15,000 page checklist for cyber protections will be mandated by a new Executive Order called The Definitive Checklist for Commercial, Governmental, Not-for-Profit, and Any Other Entity Including under Age Operated Fiscal Processes Such As Girl Scout Cookie Sales.”
A founder of a smart cyber security firm said, “These recent breaches would have been prevented had each of the compromised firms licensed our Bayesian anchored cyber security platform. Our smart cyber platform proactively blocks the breach mechanisms developed by world class actors regardless of their geographical location.”
So what’s the present and somewhat amusing reality: Maybe no nation state? Maybe no Axis of Evil? Maybe no massive, organized gang of disaffected technical wizards? Maybe no compromised insiders?
What have we got. A teen whose father appears to be unaware of his progeny’s extracurricular activities?
Content creators: Is it time for a podcast, a Netflix documentary, a 60 minutes segment?
Stephen E Arnold, March 28, 2022
Simple, Fair Digital Markets: Saddle Up, Don Quixote
March 25, 2022
Who knew that I would continue to reference the very long, very weird book I had to read in the seventh grade? Yet here I am: Don Quixote, slayer of windmills, a trusted sidekick, and a study horse.
“Europe Agrees New Law to Curb Big Tech Dominance” explains that the proud animal and adept rider is ambling from the barn after decades of training. Tally ho! The write up says:
Under the Digital Markets Act (DMA), giants such as Google and Apple will be forced to open up their services and platforms to other businesses. Major technology firms have long faced criticism that they use their market dominance to squeeze out competition.
Now that certain US technology outfits are dominant, what’s the fix? I suppose one could dismount and paint the windmills a different color. Where would one locate a color? How about Googling? Alternatively one might consult a Facebook group. And there is the ever objective Amazon, complete with fake reviews and odd ball videos showing a functioning product? Amazing.
Outfitted like the elegant Don, the trusted source of information reports:
The EU wants to give users more choice over how people send messages. The new rules would require that technology make their messaging services interoperable with smaller competitors.
As the rider, cohorts, and snorting animals charge at their targets, will the companies be fungible. Might they prove to be chimera?
At least one of the evil entities is Googzilla? Despite its age, the creature still has teeth, lots of teeth, and lawyers, lots of lawyers.
Stephen E Arnold, March 25, 2022
NASA and Its Coding Guidelines
March 25, 2022
I read “How to Code Like the Top Programmers at Nasa — 10 Critical Rules.” Interesting list. Here are three tips I find fascinating:
- Do not use dynamic memory allocation after initialization
- Data objects must be declared at the smallest possible level of scope
- The use of pointers should be restricted.
There are seven more in the article.
I asked myself, “Should the list include ‘Let Elon Musk’s outfit do it’?”
Stephen E Arnold, March 25, 2022