DarkCyber for April 17, 2018, Is Now Available
April 17, 2018
DarkCyber for April 17, 2018, is now available at www.arnoldit.com/wordpress and on Vimeo at https://vimeo.com/264827844
DarkCyber is a weekly video news and analysis program about the Dark Web and lesser known Internet services.
Push back from different organizations suggests that the unregulated, free wheeling days of digital currencies are winding down. France and Japan have taken action to curtail some digital currency practices. Plus Google and Twitter have banned ads for digital currencies.
In March 2018, Stephen E Arnold, producer of DarkCyber, was named to International Judicial Commission of Inquiry into Human Trafficking & Child Sex Abuse. He points out that as censorship increases, bad actors will step up their pace of innovation.
He said, “An uptick in the use of pastesites and encrypted chat make it increasingly difficult for investigators to identify and take action against those engaged in human trafficking and related crimes. Additional funding and faster cycle procurements of next generation are important priorities in the next six to nine months.”
DarkCyber answers a viewer’s question about the Katim secure mobile phone created by DarkMatter, a cyber security firm in the United Arab Emirates. The Katim device may be a market test or a way to determine interest in secure devices.
VPNs promise increased security for users. DarkCyber points out that a number of VPNs leak user data. Protocol flaws and VPN operators who keep logs of user behaviors make it clear that VPNs may be virtual, just not private.
For more information about DarkCyber, write us at darkcyber333 at yandex.com.
Kenny Toth, April 17, 2018
Attivio and MC+A Combine Forces
April 7, 2018
Over the years, Attivio positioned itself as more than search. That type of shift has characterized many vendors anchored in search and retrieval. We noted that Attivio has “partnered” with MC+A, a search centric company. MC+A also forged a relationship with Coveo, another search and retrieval vendor with a history of repositioning.
We learned from “Attivio and MC+A Announce Partnership to Deliver Next-Generation Cognitive Search Solutions” at Markets Insider that:
“MC+A will resell Attivio’s platform, seamlessly integrate their enterprise-grade connectors into it, and provide SI services in the US market. ‘Partnering with MC+A extends our ability to address organizations’ needs for making all information available to employees and customers at the moment they need it,’ said Stephen Baker, CEO at Attivio. ‘This is particularly critical for companies looking to upgrade legacy search applications onto a modern, machine-learning based search and insight platform.’ …
The story added:
“By combining self-learning technologies, such as natural language processing, machine learning, and information indexing, the Attivio platform is helping Fortune 500 enterprises leverage customer insight, surface upsell opportunities, and improve compliance productivity. MC+A has over 15 years of experience innovating with search and delivering customized search-based applications solutions to enterprises. MC+A has also developed a connector bridge solution that allows customers to leverage existing infrastructure to simplify the transition to the Attivio platform.”
Attivio was founded in 2007, and is headquartered in Newton, Massachusetts. The company’s client roster includes prominent organizations like UBS, Cisco, Citi, and DARPA. Attivio in its early days was similar in some ways to the Fast Search & Transfer technology once cleverly dubbed ESP. No, not extra sensory perception. ESP was the enterprise search platform.
Based in Chicago and founded in 2004, MC+A specializes in implementations of cognitive search and insight engine technology. A couple of years ago, MC+A was involved with Yippy, the former Vivisimo metasearch system. When IBM bought Vivisimio, the metasearch technology morphed into a Big Data component of Watson.
If this walk down memory lane suggests that vendors of proprietary systems have been working to find purchase on revenue mountain, there may be a reason. The big money, based on information available to Beyond Search, comes from integrating open source solutions like Lucene into comprehensive analytic systems.
In a nutshell, the rise of Lucene and Elastic have created opportunities for some companies which can deliver more comprehensive solutions than search and retrieval anchored in old-school solutions.
More than repositioning, jargon, and partnerships may be needed in today’s market place where “answers”, not laundry lists are in demand. For mini profiles of vendors which are redefining information access and answering questions, follow the news stories in our new video news program DarkCyber. There’s a new program each week. Plus, you can get a sense of the new directions in information access by reading my 2015 book (still timely and very relevant) CyberOSINT: Next Generation Information Access.
Stephen E Arnold,
Stephen E Arnold, April 7, 2018
CyberOSINT: Next Generation Information Access Explains the Tech Behind the Facebook, GSR, Cambridge Analytica Matter
April 5, 2018
In 2015, I published CyberOSINT: Next Generation Information Access. This is a quick reminder that the profiles of the vendors who have created software systems and tools for law enforcement and intelligence professionals remains timely.
The 200 page book provides examples, screenshots, and explanations of the tools which are available to analyze social media information. The book is the most comprehensive run down of the open source, commercial, and cloud based systems which can make sense of social media data, lawful intercept data, and general text and imagery content.
Companies described in this collection of “tools” include:
- Cyveillance (now LookingGlass)
- Decisive Analytics
- IBM i2 (Analysts Notebook)
- Geofeedia
- Leidos
- Palantir Gotham
- and more than a dozen developers of commercial and open source, high impact cyberOSINT tool vendors.
The book is available for $49. Additional information is available on my Xenky.com Web site. You can buy the PDF book online at this link gum.co/cyberosint.
Get the CyberOSINT monograph. It’s the standard reference for practical and effective analysis, text analytics, and next generation solutions.
Stephen E Arnold, April 5, 2018
DarkCyber Profiles the Grayshift iPhone Unlocking Appliance
April 5, 2018
DarkCyber has released a special video report about Grayshift’s iPhone unlocking device for law enforcement forensics professionals. The GrayKey device unlocks most iPhones quickly and without the need to ship the suspect’s mobile phone off site.
The video is available on Vimeo at https://vimeo.com/262858305.
The video covers the pricing for the iPhone unlocker and its key features. Plus, the video product overview identifies the challenges that Grayshift will have to overcome if it wants to become the preferred provider of plug-and-unlock iPhone devices.
Stephen E Arnold said, “Grayshift’s GrayKey is important because it offers an easy-to-use iPhone unlocking system. Four digit passcode protected devices can be unlocked in two to three hours. Apple mobiles with six digit passcodes can be unlocked in two to three days. The device can be used in a mobile forensics lab and costs a fraction of some competitive solutions. GrayKey looks like the right product at the right time and at the right price.”
DarkCyber is a weekly video new program for law enforcement, intelligence, and security professionals. The special report series will focus on a single product, service, or technical innovation.
This is a special report in his CyberOSINT Tools series. These special reports will be issued when notable products, services, or technologies become available to law enforcement and intelligence professionals.
Stephen E Arnold is the author of “Dark Web Notebook” and “CyberOSINT: Next Generation Information Access.” He has been named as a technology adviser to the UK based Judicial Commission of Inquiry into Human Trafficking and Child Sex Abuse.” Mr. Arnold also lectures to law enforcement and intelligence professionals attending the Telestrategies ISS conferences in Prague, Washington, DC, and Panama City, Panama. In recent months, he has shared his research with law enforcement and intelligence professionals in the US and Europe. His most recent lectures focus on deanonymizing chat and digital currency transactions. One hour and full day programs are available via webinars and on-site presentations.
Kenny Toth, April 5, 2018
SIXGILL: Dark Web Intelligence with Sharp Teeth
December 14, 2017
“Sixgill” refers to the breathing apparatus of a shark. Deep. Silent. Stealthy. SIXGILL offers software and services which function like “your eyes in the Dark Web.”
Based in Netanya, just north of Tel Aviv, SIXGILL offers services for its cyber intelligence platform for the Dark Web. What sets the firm apart is its understanding of social networks and their mechanisms for operation.*
The company’s primary product is called “Dark-i.” The firm’s Web site states that the firm’s system can:
- Track and discover communication nodes across darknets with the capability to trace malicious activity back to their original sources
- Track criminal activity throughout the cyber crime lifecycle
- Operate in a covert manner including the ability to pinpoint and track illegal hideouts
- Support clients with automated and intelligence methods.
The Dark-i system is impressive. In a walk through of the firm’s capabilities, I noted these specific features of the Dark-i system:
- Easy-to-understand reports, including summaries of alleged bad actors behaviors with time stamp data
- Automated “profiles” of Dark Web malicious actors
- The social networks of the alleged bad actors
- The behavior patterns in accessing the Dark Web and the Dark Web sites the individuals visit.
- Access to the information on Dark Web forums.
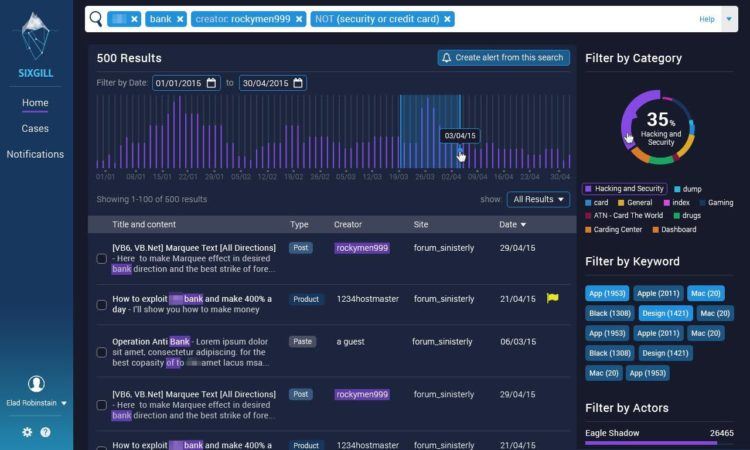
Details about the innovations the company uses are very difficult to obtain. Based on open source information, a typical interface for SIXGILL looks like this:
Based on my reading of the information in the screenshot, it appears that this SIXGILL display provides the following information:
- The results of a query
- Items in the result set on a time line
- One-click filtering based on categories taken from the the sources and from tags generated by the system, threat actors, and Dark Web sources
- A list of forum posts with the “creator” identified along with the source site and the date of the post.
Compared with reports about Dark Web activity from other vendors providing Dark Web analytic, monitoring, and search services, the Dark Web Notebook team pegs s SIXGILL in the top tier of services.
Palantir Technologies: Valuation Doubts?
October 18, 2017
i read “Palantir Will Struggle to Hold On to $20 Billion Valuation, Study Says.” Interesting stuff because beating up on hapless Silicon Valley companies is becoming a mini-trend. Facebook is in the dog house because it sells ads. Google is in the kennel because Europe finds its business practices less than Euro-cool. Twitter. Poor Twitter. Its part time boss is going to improve controls on the Wild West of short messages.
Now it is Palantir, the software company which offers an alternative to the IBM Analyst Notebook system. I thought Palantir was in the cat bird seat to provide technology that would deliver certain functionality to various US government agencies, financial institutions, and other organizations wanting to make sense of data.
I learned from the Bloomberg write up:
If Palantir Technologies Inc. pursues plans for a public offering and follows through by 2019, it will need to rein in spending and woo corporate customers just to be able to hang on to a $20 billion valuation it was awarded two years ago, according to a new study. It could also be worth a lot less.
Bloomberg cites a “study” which reveals that Palantir technology needs some set up and configuration before the users can make sense of digital information processed by the system.
This apparently comes as a surprise to Bloomberg and the SharesPost research team.
The reality of next generation information access systems is different from an iPhone or Android app one downloads and uses immediately. I know this is a surprise to many “experts,” but next generation information access systems are complicated. I explain why in my 2015 CyberOSINT: Next Generation Information Access Systems.
What’s interesting is that instead of putting the Palantir systems in a meaningful context, the report and apparently Bloomberg want to make another Silicon Valley outfit look like a bent penny.
Valuation is in the eye of the beholder and the Excels generated by whiz kids who want to buy a new Porsche.
Bloomberg quotes the report as a way to wrap up the news story with a stomp on Palantir’s foot; to wit:
Palantir “is currently valued much higher than its peers in the big data and analytics space,” Kulkarni wrote, adding that he believes Palantir will maintain the rich valuation if it keeps adding corporate clients and expedites cost cutting. He wrote that Palantir remains an attractive acquisition target – Oracle weighed the option last year but demurred – and estimated Palantir’s low-end value in 2019 at $13.8 billion.
Is there another view of Palantir? Guess not.
Stephen E Arnold, October 18, 2017
Short Honk: Cyber Weapon Market
October 2, 2017
In November 2017, the focus of Beyond Search and HonkinNews will change. The free information services will increase their coverage of weaponized online. A preview of the type of information we will highlight appears in “Cyber Weapon Market to Reach US$521.87 Billion by the End of 2021.” A summary of the report appears in the article in OpenPR. The news item asserts:
According to TMR, the global cyber weapon market stood at US$390 bn in 2014. Rising at a CAGR of 4.4% CAGR, the market is expected to reach US$521.87 bn by the end of 2021. With a share of 73.8%, the defensive cyber weapon segment dominated the market by type in 2014. Regionally, North America accounted for the leading share of 36% in the global market in 2014.
If the estimate is accurate, there is money in things cyber. Watch for our new report E Discovery for Cyber Intelligence. Previews of the report will appear in our twice a month video program “HonkinNews” starting in six weeks.
Stephen E Arnold, October 2, 2017
Stephen E Arnold: Dark Web Use Expected to Increase
June 27, 2017
Author predicts filtering and other restrictions on the open Internet will push more users toward secret encrypted platforms
Despite stepped-up efforts by federal and local law enforcement agencies, the Dark Web and the contraband markets that thrive there will continue to grow in the coming years. That’s the conclusion shared by author and consultant Stephen E Arnold in his new book Dark Web Notebook, a practical guide for law enforcement, intelligence, and corporate security personnel.
Arnold was a featured speaker this month at the at the Techno Security & Digital Forensics Conference in Myrtle Beach, SC, where he explained how the Dark Web operates and how investigators can assume a secret identity and acquire the necessary tools to explore hidden online communities.
In his lectures, Arnold noted that governments in the UK, China, Egypt, and other countries are implementing tighter restrictions on electronic communications while private companies such as Facebook and Google are implementing more content filtering. The result, he said, is that more activities that are normally conducted on the “surface web” are migrating to the encrypted platforms offered by the Dark Web. At the same time, private citizens are adopting apps and other encryption tools to protect their personal privacy.
“It’s like squeezing a sponge or a tube of toothpaste,” Arnold said. “The substance has to go somewhere. The Dark Web will become more attractive to people who want to conduct their affairs in secret and that will make the Dark Web an increasing area of interest to law enforcement, security and intelligence professionals.”
The Dark Web is also flashing on the radar of state and local law enforcement agencies. A June 10 article in the New York Times (https://www.nytimes.com/2017/06/10/business/dealbook/opioid-dark-web-drug-overdose.html) described how police in the resort town of Park City, UT, had to learn about the Dark Web after two 13-year-old boys died after taking a synthetic opioid called “Pinky” that was purchased on the Dark Web.
“This terrible tragedy is an example of how the influence of the Dark web is spreading into small town in the US and around the world. Law enforcement personnel at all levels are going to need to understand how this new environment functions if they hope to protect the citizens in their communities,” Arnold said.
Although much has been written about the Dark Web, Arnold’s book is unique in that it was created specifically for investigators. It presents step-by-step instructions that help investigators safely explore the digital underworld. The book is available as a 250-page digital download for $49 at https://gum.co/darkweb.
In addition to his lectures, Arnold also offers a hands-on tutorial for small groups of qualified participants. In these sessions, participants use a secure computer to create a “legend” identity and explore the Dark We. They also learn how to acquire other digital tools and services including Bitcoin, the digital currency favored by Dark Web vendors.
Arnold will present his lectures and tutorial again at the 2017 Techno Security & Digital Forensics Conference September 18-20 in San Antonio. Information about the conference is available at www.technosecurity.us.
About the Book
The 250-page book includes a tour of the Dark Web with profiles of vendors and markets, explanations of access tools such as the Tor browser, reviews of services for searching Dark Web content, research resources available on the public Internet, and details about commercial solutions.
Detailed descriptions of each chapter are posted at http://xenky.com/darkwebnotebook.
The book is available as a digital download for $49 at https://gum.co/darkweb.
About the Author
Stephen E Arnold’s career includes work at Halliburton Nuclear Utility Services and Booz, Allen & Hamilton. He built and sold several stary-up ventures including The Point Internet Service. He and his team built the online system for the Threat Open Intelligence Gateway (TOSIG) for the US government. He is the author of The Google Legacy (2005), Google Version 2 (2007), and Google: The Digital Gutenberg (2009). In 2015, he published CyberOSINT: Next Generation Information Access. He is a Summa cum laude graduate of Bradley University and he has completed work on his PhD at the University of Illinois.
About ArnoldIT
Arnold Information Technology conducts research into online information and services. Founded by Stephen E Arnold in 1991, the company has provided technology services to organizations worldwide.
Ric Manning, June 27, 2017
Dark Web Notebook Now Available
June 5, 2017
Arnold Information Technology has published Dark Web Notebook: Investigative Tools and Tactics for Law Enforcement, Security, and Intelligence Organizations. The 250-page book provides an investigator with instructions and tips for the safe use of the Dark Web. The book, delivered as a PDF file, costs $49.

Orders and requests for more information be directed to darkwebnotebook@yandex.com. Purchasers must verify that they work for a law enforcement, security, or intelligence organization. Dark Web Notebook is not intended for general distribution due to the sensitive information it contains.
The author is Stephen E Arnold, whose previous books include CyberOSINT: Next Generation Information Access and Google Version 2.0: The Calculating Predator, among others. Arnold, a former Booz, Allen & Hamilton executive, worked on the US government-wide index and the Threat Open Source Intelligence Gateway.
The Dark Web Notebook was suggested by attendees at Arnold’s Dark Web training sessions, lectures, and webinars. The Notebook provides specific information an investigator or intelligence professional can use to integrate Dark Web information into an operation.
Stephen E Arnold, author of the Dark Web Notebook, said:
“The information in the Dark Web Notebook has been selected and presented to allow an investigator to access the Dark Web quickly and in a way that protects his or her actual identity. In addition to practical information, the book explains how to gather information from the Dark Web. Also included are lists of vendors who provide Dark Web services to government agencies along with descriptions of open source and commercial software tools for gathering and analyzing Dark Web data. Much of the information has never been collected in a single volume written specifically for those engaged in active investigations or operations.”
The book includes a comprehensive table of contents, a glossary of terms and their definitions, and a detailed index.
The book is divided into 13 chapters. These are:
- Why write about the Dark Web?
- An Introduction to the Dark Web
- A Dark Web Tour with profiles of more than a dozen Dark Web sites, their products, and services
- Dark Web Questions and Answers
- Basic Security
- Enhanced Security
- Surface Web Resources
- Dark Web Search Systems
- Hacking the Dark Web
- Commercial Solutions
- Bitcoin and Variants
- Privacy
- Outlook
In addition to the Glossary, the annexes include a list of DARPA Memex open source software written to perform specific Dark Web functions, a list of spoofed Dark Web sites operated by law enforcement and intelligence agencies, and a list of training resources.
Kenny Toth, June 5, 2017
Dark Web and Tor Investigative Tools Webinar
January 5, 2016
Telestrategies announced on January 4, 2016, a new webinar for active LEA and intel professionals. The one hour program is focused on tactics, new products, and ongoing developments for Dark Web and Tor investigations. The program is designed to provide an overview of public, open source, and commercial systems and products. These systems may be used as standalone tools or integrated with IBM i2 ANB or Palantir Gotham. More information about the program is available from Telestrategies. There is no charge for the program. In 2016, Stephen E Arnold’s new Dark Web Notebook will be published. More information about the new monograph upon which the webinar is based may be obtained by writing benkent2020 at yahoo dot com.
Stephen E Arnold, January 5, 2016