CyberOSINT Study Findings Video Available
May 5, 2015
The third video summarizing Stephen E Arnold’s “CyberOSINT: Next Generation Information Access” is available. Grab your popcorn. The video is at this link.
Kenny Toth, May 5, 2015
Recorded Future: The Threat Detection Leader
April 29, 2015
The Exclusive Interview with Jason Hines, Global Vice President at Recorded Future
In my analyses of Google technology, despite the search giant’s significant technical achievements, Google has a weakness. That “issue” is the company’s comparatively weak time capabilities. Identifying the specific time at which an event took place or is taking place is a very difficult computing problem. Time is essential to understanding the context of an event.
This point becomes clear in the answers to my questions in the Xenky Cyber Wizards Speak interview, conducted on April 25, 2015, with Jason Hines, one of the leaders in Recorded Future’s threat detection efforts. You can read the full interview with Hines on the Xenky.com Cyber Wizards Speak site at the Recorded Future Threat Intelligence Blog.
Recorded Future is a rapidly growing, highly influential start up spawned by a team of computer scientists responsible for the Spotfire content analytics system. The team set out in 2010 to use time as one of the lynch pins in a predictive analytics service. The idea was simple: Identify the time of actions, apply numerical analyses to events related by semantics or entities, and flag important developments likely to result from signals in the content stream. The idea was to use time as the foundation of a next generation analysis system, complete with visual representations of otherwise unfathomable data from the Web, including forums, content hosting sites like Pastebin, social media, and so on.
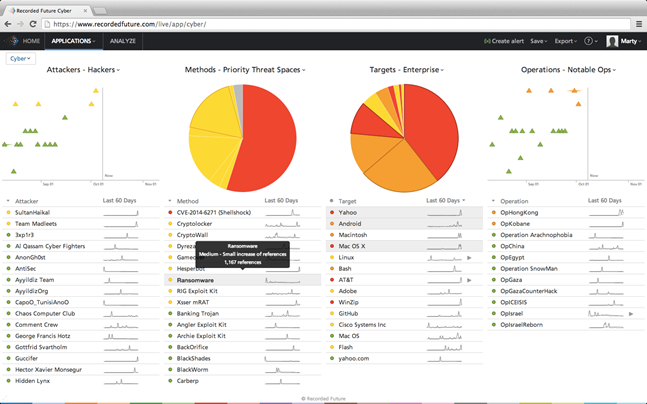
A Recorded Future data dashboard it easy for a law enforcement or intelligence professionals to identify important events and, with a mouse click, zoom to the specific data of importance to an investigation. (Used with the permission of Recorded Future, 2015.)
Five years ago, the tools for threat detection did not exist. Components like distributed content acquisition and visualization provided significant benefits to enterprise and consumer applications. Google, for example, built a multi-billion business using distributed processes for Web searching. Salesforce.com integrated visualization into its cloud services to allow its customers to “get insight faster.”
According to Jason Hines, one of the founders of Recorded Future and a former Google engineer, “When our team set out about five years ago, we took on the big challenge of indexing the Web in real time for analysis, and in doing so developed unique technology that allows users to unlock new analytic value from the Web.”
Recorded Future attracted attention almost immediately. In what was an industry first, Google and In-Q-Tel (the investment arm of the US government) invested in the Boston-based company. Threat intelligence is a field defined by Recorded Future. The ability to process massive real time content flows and then identify hot spots and items of interest to a matter allows an authorized user to identify threats and take appropriate action quickly. Fueled by commercial events like the security breach at Sony and cyber attacks on the White House, threat detection is now a core business concern.
The impact of Recorded Future’s innovations on threat detection was immediate. Traditional methods relied on human analysts. These methods worked but were and are slow and expensive. The use of Google-scale content processing combined with “smart mathematics” opened the door to a radically new approach to threat detection. Security, law enforcement, and intelligence professionals understood that sophisticated mathematical procedures combined with a real-time content processing capability would deliver a new and sophisticated approach to reducing risk, which is the central focus of threat detection.
In the exclusive interview with Xenky.com, the law enforcement and intelligence information service, Hines told me:
Recorded Future provides information security analysts with real-time threat intelligence to proactively defend their organization from cyber attacks. Our patented Web Intelligence Engine indexes and analyzes the open and Deep Web to provide you actionable insights and real-time alerts into emerging and direct threats. Four of the top five companies in the world rely on Recorded Future.
Despite the blue ribbon technology and support of organizations widely recognized as the most sophisticated in the technology sector, Recorded Future’s technology is a response to customer needs in the financial, defense, and security sectors. Hines said:
When it comes to security professionals we really enable them to become more proactive and intelligence-driven, improve threat response effectiveness, and help them inform the leadership and board on the organization’s threat environment. Recorded Future has beautiful interactive visualizations, and it’s something that we hear security administrators love to put in front of top management.
As the first mover in the threat intelligence sector, Recorded Future makes it possible for an authorized user to identify high risk situations. The company’s ability to help forecast and spotlight threats likely to signal a potential problem has obvious benefits. For security applications, Recorded Future identifies threats and provides data which allow adaptive perimeter systems like intelligent firewalls to proactively respond to threats from hackers and cyber criminals. For law enforcement, Recorded Future can flag trends so that investigators can better allocate their resources when dealing with a specific surveillance task.
Hines told me that financial and other consumer centric firms can tap Recorded Future’s threat intelligence solutions. He said:
We are increasingly looking outside our enterprise and attempt to better anticipate emerging threats. With tools like Recorded Future we can assess huge swaths of behavior at a high level across the network and surface things that are very pertinent to your interests or business activities across the globe. Cyber security is about proactively knowing potential threats, and much of that is previewed on IRC channels, social media postings, and so on.
In my new monograph CyberOSINT: Next Generation Information Access, Recorded Future emerged as the leader in threat intelligence among the 22 companies offering NGIA services. To learn more about Recorded Future, navigate to the firm’s Web site at www.recordedfuture.com.
Stephen E Arnold, April 29, 2015
IBM: QRadar Update
April 22, 2015
I read “IBM builds QRadar Security Intelligence in the Cloud.” The write up presents a new IBM service. I checked my files and the “new” service seems to be based on a 2009 acquisition’s capabilities. I did not include IBM in my CyberOSINT monograph because it struck me as lagging behind Cyveillance and several other outfits’ offerings. I did have one question after reading the article: Does the system trap buzzword anomalies like this one:
This is also powered by IBM QRadar technology, and uses analytics and a hosted, multi-tenant technology to integrate with existing infrastructure, working with real-time correlation and anomaly detection capabilities.
Stephen E Arnold, April 22, 2015
Second CyberOSINT Video Available
April 22, 2015
Xenky.com posted the second part of its interview with Stephen E Arnold. You can view CyberOSINT 2: The Information Factory via YouTube.
Kenny Toth, April 22, 2015
Twitter Plays Hard Ball or DataSift Knows the End Is in Sight
April 11, 2015
I read “Twitter Ends its Partnership with DataSift – Firehose Access Expires on August 13, 2015.” DataSift supports a number of competitive and other intelligence services with its authorized Twitter stream. The write up says:
DataSift’s customers will be able to access Twitter’s firehose of data as normal until August 13th, 2015. After that date all the customers will need to transition to other providers to receive Twitter data. This is an extremely disappointing result to us and the ecosystem of companies we have helped to build solutions around Twitter data.
I found this interesting. Plan now or lose that authorized firehose. Perhaps Twitter wants more money? On the other hand, maybe DataSift realizes that for some intelligence tasks, Facebook is where the money is. Twitter is a noise machine. Facebook, despite its flaws, is anchored in humans, but the noise is increasing. Some content processes become more tricky with each business twist and turn.
Stephen E Arnold, April 11, 2015
CyberOSINT Update: No Fooling
April 1, 2015
Two quick items about cyber OSINT. These are not April Fool jokes and the information is available without nag screens, registration forms, or blinking ads.
First, we have posted a five minute video that explains what cyber OSINT means. I was interviewed by award winning tech journalist Ric Manning. You can view the video at this link.
Second, we have started a new interview series. Like the original Search Wizards Speak series of interviews, the Cyber Wizards Speak interviews provide more first-person information about cyber OSINT from those working in the field. The interviews are intended for those interested in law enforcement, intelligence, and security. The first interview in the series presents the viewpoints of Luca Scagliarini, one of the original developers of the Expert System Cogito system. You can find the interview at www.xenky.com/expert-system.
Watch for upcoming announcements about more cyber OSINT videos and interviews with the principals of BrightPlanet and Recorded Future.
Copies of my new study CyberOSINT: Next Generation Access are available at www.xenky.com/cyberosint.
Stephen E Arnold, April 1, 2015
Lexmark Jumps into Intelligence Work
March 25, 2015
I read “Lexmark Buys Software Maker Kofax at 47% Premium in $1B Deal.” The write up focuses on Kofax’s content management services. Largely overlooked is Kofax’s Kapow Tech unit. This company provides specialized services to intelligence, law enforcement, and security entities. How will a printer company in Lexington manage the ageing Kofax technology and the more promising Kapow entity? This should be interesting. Lexmark already owns the Brainware technology and the ISYS Search Software system. Lexmark is starting to look a bit like IBM and OpenText. These companies have rolled up promising firms, only to lose their focus. Will Lexmark follow in IBM’s footsteps and cook up a Watson? I think there is still some IBM DNA in the pale blue veins of the Lexmark outfit. On the other hand, Lexmark seems to be emulating some of the dance steps emerging from the Hewlett Packard ballroom as well. Fascinating. The mid-tier consultants with waves, quadrants, and paid for webinars will have to find a way to shoehorn hardware, health care, intelligence, and document scanning into one overview. Confused? Just wait.
Stephen E Arnold, March 25, 2015
Modus Operandi Gets a Big Data Storage Contract
March 24, 2015
The US Missile Defense Agency awarded Modus Operandi a huge government contract to develop an advanced data storage and retrieval system for the Ballistic Missile Defense System. Modus Operandi specializes in big data analytic solutions for national security and commercial organizations. Modus Operandi posted a press release on their Web site to share the news, “Modus Operandi Awarded Contract To Develop Advanced Data Storage And Retrieval System For The US Missile Defense Agency.”
The contract is a Phase I Small Business Innovation Research (SBIR), under which Modus Operandi will work on the DMDS Analytic Semantic System (BASS). The BASS will replace the old legacy system and update it to be compliant with social media communities, the Internet, and intelligence.
“ ‘There has been a lot of work in the areas of big data and analytics across many domains, and we can now apply some of those newer technologies and techniques to traditional legacy systems such as what the MDA is using,’ said Dr. Eric Little, vice president and chief scientist, Modus Operandi. ‘This approach will provide an unprecedented set of capabilities for the MDA’s data analysts to explore enormous simulation datasets and gain a dramatically better understanding of what the data actually means.’ ”
It is worrisome that the missile defense system is relying on an old legacy system, but at least it is being upgraded now. Modus Operandi also sales Cyber OSINT and they are applying this technology in an interesting way for the government.
Whitney Grace, March 24, 2015
Stephen E Arnold, Publisher of CyberOSINT at www.xenky.com
Geofeedia Secures Cash Infusion of $3 Million
March 11, 2015
Cyber OSINT vendor Geofeedia landed an additional $3 million in venture funding, according to the Chicago Tribune. The new capital brings the firm’s total funding to $6.8 million. Goofeedia specializes in location-based social media intelligence. According to the firm’s Web site:
Businesses, media companies, and government agencies use Geofeedia to understand social media happening at locations important to them. Geofeedia’s patented technologies allow you to search and monitor areas as large as a city or as small as a single building. Geofeedia currently searches Twitter, Facebook, Instagram, YouTube, Picasa, Flickr and Viddy. Geofeedia searches by location first rather than by a specific series of words (such as keywords or hashtags). The net result: Geofeedia’s data set contains the hidden 70%+ of data coming from locations compared to traditional tools that rely on certain words to be included in their data sets.
For more information, navigate to www.geofeedia.com.
Stephen E Arnold, March 11, 2015
Centripetal and Cyveillance Form Threat Detection Partnership
March 11, 2015
Two companies with cyber OSINT capabilities have formed a partnership to deliver “actionable threat intelligence.” I learned in a news release that:
Centripetal Networks Inc., the leading provider of Real-Time Active Network Defense solutions, announces their partnership today with Cyveillance, a QinetiQ company and a world leader in cyber intelligence. This partnership will deliver actionable cyber threat intelligence to organizations across all industries by enabling Centripetal’s high-performance RuleGate® platform to leverage Cyveillance’s advanced threat intelligence streams.
Both companies delivered well-received presentations at the recent Cyber OSINT conference held in Washington, DC, in February 2015.
For more information about Centripetal navigate to www.centripetalnetworks.com and Cyveillance at www.cyveillance.com.
Stephen E Arnold, March 11, 2015


