Voyager Labs Expands into South America
October 14, 2021
Well this is an interesting development. Brazil’s ITForum reports, “Voyager Labs Appoints VP and Opens Operations in Latin America and the Caribbean.” (I read and quote from Google’s serviceable translation.)
Voyager Labs is an Israeli specialized services firm that keeps a very low profile. Their platform uses machine learning to find and analyze clues to fight cyber attacks, organized crime, fraud, corruption, drug trafficking, money laundering, and terrorism. Voyager Labs’ clients include private companies and assorted government agencies around the world.
The brief announcement reveals:
“Voyager Labs, an AI-based cybersecurity and research specialist, announced this week the arrival in Latin America and the Caribbean. To lead the operation, the company appointed Marcelo Comité as regional vice president. The executive, according to the company, has experience in the areas of investigation, security, and defense in Brazil and the region. Comité will have as mission to consolidate teams of experts to improve the services and support in technologies in the region, according to the needs and particularities of each country. ‘It is a great challenge to drive Voyager Labs’ expansion in Latin America and the Caribbean. Together with our network of partners in each country, we will strengthen ties with strategic clients in the areas of government, police, military sector and private companies’, says the executive.”
We are intrigued by the move to South America, since most of the Israeli firms are building operations in Singapore. What’s Voyager know that its competitors do not? Not familiar with Voyager Labs? Worth knowing the company perhaps?
Cynthia Murrell, October 14, 2021
Key Words: Useful Things
October 7, 2021
In the middle of nowhere in the American southwest, lunch time conversation turned to surveillance. I mentioned a couple of characteristics of modern smartphones, butjec people put down their sandwiches. I changed the subject. Later, when a wispy LTE signal permitted, I read “Google Is Giving Data to Police Based on Search Keywords, Court Docs Show.” This is an example of information which I don’t think should be made public.
The write up states:
Court documents showed that Google provided the IP addresses of people who searched for the arson victim’s address, which investigators tied to a phone number belonging to Williams. Police then used the phone number records to pinpoint the location of Williams’ device near the arson, according to court documents.
I want to point out that any string could contain actionable information; to wit:
- The name or abbreviation of a chemical substance
- An address of an entity
- A slang term for a controlled substance
- A specific geographic area or a latitude and longitude designation on a Google map.
With data federation and cross correlation, some specialized software systems can knit together disparate items of information in a useful manner.
The data and the analytic tools are essential for some government activities. Careless release of such sensitive information has unanticipated downstream consequences. Old fashioned secrecy has some upsides in my opinion.
Stephen E Arnold, October 7, 2021
NSO Group and Collateral Damage: Shadowdragon
September 23, 2021
The NSO Group has captured headlines and given a number of journalists a new beat to cover: Special service vendors. This phrase “specialized service vendors” is the one I use to capture the market niche served by companies as diverse as Anduril to Voyager Labs. Most of these firms walk a fine line: Providing enough public information so that a would-be customer like a government agency can locate a contact point to staying out of the floodlights looking for next NSO Group to research and write about.
I read “Shadowdragon: Inside the Social Media Surveillance Software That Can Watch Your Every Move.” The exposé appearing in the The Intercept follows a predictable pattern: Surveillance, law enforcement, technology, sources, similar software (in this story Kaseware), and rights violations.
A Wall Street Journal reporter is allegedly working on a book that will surf on the the NSO Group’s tsunami of surveillance shock.
I have spelled out three concerns about what I call the conversion of NSO Group from a low-profile outfit to the poster child for misuse of certain types of technology. Let me recap these:
- SNOWDEN. Edward Snowden’s oath to keep information secret was broken with his notable data dump. Some of these 2013 materials provided sufficient information about specialized software and services to create or release a desire to know more about the market segment.
- CITIZENS LAB. In 2016 Citizen’s Lab kicked off its coverage of the specialized software niche with “The Million Dollar Dissident: NSO Group’s iPhone Zero Days Used against a UAE Human Rights Defender.”
- PITCHING NSO. In 2017, Francisco Partners’ mounted an effort to sell NSO Group for an asking price of around $1 billion. Venture and finance types perked up their ears. Some asked, “What’s this specialized service cyber software?”
- BOOK. In 2019, Shoshana Zuboff published “The Age of Surveillance Capitalism,” which provided a “name” to some of the specialized software functions.
Reporters, activists, researchers, academics, and companies not previously aware of the specialized service sector are now chasing information. Unlike some commercial market sectors, funds are available. The appetite for advanced software and services is growing.
Now back to the company named associated by some with an insect. What impact will the Intercept write up have. I don’t know, but I have three ideas:
First, the company will become a subject of interest for some; for example, an investigative reporter working on a book about the specialized service sector.
Second, non-LE and intel-related organizations will express an interest in licensing the software and gaining access to the firm’s database and other technology. (Voyager Labs has explored selling its software for “marketing.”)
Third, the company’s willingness to market its products and services more aggressively may be reduced. Shadowdragon advertised for a marketing professional, presumably to support the company’s sales efforts. One of the firm’s senior managers posts on LinkedIn in order to express support for certain activities and retain visibility in that Microsoft owned service.
From my narrow point of view, some information should not be exposed to the public; for example, the Snowden dump. And some of the marketing activities of specialized service providers should be wound back to the low profile activities of the pre-911 era.
Unfortunately it may be too late. Commercial success may be more important than creating solutions which support LE and intelligence operations. Today anyone can enjoy useful tools. Check out Hunchly OSINT or Maltego. Explore what these tools can do.
Will Shadowdragon become collateral damage as a consequence of NSO Group?
Stephen E Arnold, September 23, 2021
Alleged DHS Monitoring of Naturalized Citizens
September 9, 2021
Are the fates of millions of naturalized immigrants are at the mercy of one secretive algorithm run by the Department of Homeland Security and, unsurprisingly, powered by Amazon Web Services?
The Intercept examined a number of documents acquired by the Open Society Justice Initiative and Muslim Advocates through FOIA lawsuits and reports, “Little-Known Federal Software Can Trigger Revocation of Citizenship.” Dubbed ATLAS, the software runs immigrants’ information through assorted federal databases looking for any sign of dishonesty or danger. Journalists Sam Biddle and Maryam Saleh write:
“ATLAS helps DHS investigate immigrants’ personal relationships and backgrounds, examining biometric information like fingerprints and, in certain circumstances, considering an immigrant’s race, ethnicity, and national origin. It draws information from a variety of unknown sources, plus two that have been criticized as being poorly managed: the FBI’s Terrorist Screening Database, also known as the terrorist watchlist, and the National Crime Information Center. Powered by servers at tech giant Amazon, the system in 2019 alone conducted 16.5 million screenings and flagged more than 120,000 cases of potential fraud or threats to national security and public safety. Ultimately, humans at DHS are involved in determining how to handle immigrants flagged by ATLAS. But the software threatens to amplify the harm caused by bureaucratic mistakes within the immigration system, mistakes that already drive many denaturalization and deportation cases.”
DHS appears reluctant to reveal details of how ATLAS works or what information it uses, which makes it impossible to assess the program’s accuracy. It also seems the humans who act on the algorithm’s recommendations have misplaced faith in the accuracy of the data behind it. The article cites a 2020 document:
“It also notes that the accuracy of ATLAS’s input is taken as a given: ‘USCIS presumes the information submitted is accurate. … ATLAS relies on the accuracy of the information as it is collected from the immigration requestor and from the other government source systems. As such, the accuracy of the information in ATLAS is equivalent to the accuracy of the source information at the point in time when it is collected by ATLAS.’ The document further notes that ‘ATLAS does not employ any mechanisms that allow individuals to amend erroneous information’ and suggests that individuals directly contact the offices maintaining the various databases ATLAS uses if they wish to correct an error.”
We are sure that process must be a piece of cake. The authors also report:
“Denaturalization experts say that putting an immigrant’s paper trail through the algorithmic wringer can lead to automated punitive measures based not on that immigrant’s past conduct but the government’s own incompetence. … According to [Muslim Advocates’ Deborah] Choi, in some cases ‘denaturalization is sought on the basis of the mistakes of others, such as bad attorneys and translators, or even the government’s failures in record-keeping or the failures of the immigration system.’ Bureaucratic blundering can easily be construed as a sign of fraud on an immigrant’s part, especially if decades have passed since filling out the paperwork in question.”
Worth monitoring. Atlas may carry important payloads, or blow up on the launch pad.
Cynthia Murrell, September 9, 2021
TikTok: No Big Deal? Data Collection: No Big Deal Either
September 7, 2021
Here’s an interesting and presumably dead accurate statement from “TikTok Overtakes YouTube for Average Watch Time in US and UK.”
YouTube’s mass audience means it’s getting more demographics that are comparatively light internet users… it’s just reaching everyone who’s online.
So this means Google is number one? The write up points out:
The Google-owned video giant has an estimated two billion monthly users, while TikTok’s most recent public figures suggested it had about 700 million in mid-2020.
Absolutely. To me, it looks as if two billion is bigger than 700 million.
But TikTok has “upended the streaming and social landscape.”
How? Two billion is bigger than 700 million. Googlers like metrics, and that’s a noticeable difference.
I learned that the average time per user spent on the apps is higher for TikTok than for YouTube. TikTok has a high levels of “engagement.”
Google YouTube has more users, but TikTok users are apparently more hooked on the short form content from the quasi-China influenced outfit.
Advertisers will care. Retailers who want to hose users with product pitches via TikTok care.
Data harvesters at TikTok will definitely care. The more time spent on a monitored app provides a more helpful set of data about the users. These users can be tagged and analyzed using helpful open source tools like Bootleg.
Just a point to consider: How useful will time series data be about a TikTok user or user cluster? How useful will such data be when it comes time to identify a candidate for insider action? But some Silicon Valley wizards pooh pooh TikTok data collection. Maybe a knowledge gap for this crowd?
Stephen E Arnold, September 9, 2021
Protonmail Anecdote
September 6, 2021
Protonmail has been mentioned in come circles as a secure email service. Users pay to use the system. I have included it in my lectures about online messaging as an example of a “secure” service.
I spotted this Twitter thread which may be true, but, on the other hand, it may be an example of disinformation. The thread includes a screenshot and comments which may indicate that Protonmail has provided to law enforcement details about a specific user.
The person creating the tweet with the information points out:
I appreciate protonmail transparency on what happened, they provide a onion domain to avoid that issue (and a VPN), every service has to follow the law of the country they are in and a biggest issue here is the criminalization of climate activists by the french police [sic]
Additional information or disinformation may be available from this link.
Stephen E Arnold, September 6, 2021
Palantir: A Blinded Seeing Stone?
August 27, 2021
I try to keep pace with the innovations in intelware. That’s my term for specialized software designed to provide the actionable information required by intel professionals, law enforcement, and one or two attorneys who have moved past thumbtyping.
I am not sure if the article “FBI Palantir Glitch Allowed Unauthorized Access to Private Data” is on the money. The “real news” story asserted:
A computer glitch in a secretive software program used by the FBI allowed some unauthorized employees to access private data for more than a year, prosecutors revealed in a new court filing. The screw-up in the Palantir program — a software created by a sprawling data analytics company co-founded by billionaire Peter Thiel — was detailed in a letter by prosecutors in the Manhattan federal court case against accused hacker Virgil Griffith.
Please, read the source document. Also, my personal view is that such an access lapse is not good, but if the story is accurate, I am less concerned that other FBI officials may have had access to content in Gotham or whatever the system is branded these days is less problematic than oligarchs snooping or a Xi Jinping linked tong IT wonk poking around FBI only data.
My thoughts went in a different direction, and I want to capture them. Keep in mind, I don’t know if the access revelation is “true.” Nevertheless, here’s what I jotted down whilst sitting in a lecture about a smart bung for booze lovers:
- Was the access issue related to Microsoft Windows or to the AWS-type services on which some Palantir installations depend? Microsoft is another “here we go again” question, but the AWS question puts the Bezos bulldozer squarely in the security breach spotlight.
- How many days, weeks, or months was the access control out of bounds? An hour is one thing; the answer “We don’t have a clue” is another.
- If — note the if, please — the access issue is due to a Palantir specific feature or function, is there a current security audit of LE, military, and intel related installations of the “seeing stone” itself? If the answer is “yes”, why was this access issue missed? Who did the audit? Who vetted the auditor? If the answer is “no,” what are the consequences for the other software vendors and IT professionals in the “fault chain”?
The article points out that a royal “we” is troubled. That’s nice. But let’s focus on more pointed questions and deal with what might be a digital Humpty Dumpty. Just my opinion from the underground bunker in rural Kentucky.
Stephen E Arnold, August 27, 2021
DarkCyber for August 24, 2021, Now Available
August 24, 2021
The program for August 24, 2021, is now available at this link. This program, number 17 in the 2021 series, contains five stories. These are:
The NSO Group matter has produced some interesting knock on effects.
The consequence of NSO Group’s activities include criticism from the United Nations and Edward Snowden, a whistle blower and resident of Moscow. The Taliban’s takeover of Afghanistan was remarkable.
The core technology for the antagonists is discussed. You will learn about the musician Tankz and his method for making illegal credit card fraud accessible to young people in the UK and elsewhere. In addition to alleged financial crime, Tankz sings about Pyrex whipping. Ask your children what this is and then decide if you need to take action.
The program includes another reminder than one can find anti-security actors on the Regular Web and the Dark Web. The challenge is to make sure you do not become the victim of a scam.
The US government created an interesting report about nuclear war. It is not clear how lo9ng this document will remain available from a public Web server. You can check the link in the DarkCyber video for yourself. Tip: The document explains how the US may select a target for a nuclear strike.
The final story reports that the drone called Avenger has a new capability: Autonomous decision capability enabled by track and follow electronics. No human operator needed when a target is identified.
DarkCyber is produced by Stephen E Arnold and the DarkCyber research team. New programs appear every two weeks unless one of the video distribution services decides to remove the content derived from open sources of information. Tankz and a fellow traveler named DankDex, purveyor of the Fraud Bible, appear to post without pushback.
Kenny Toth, August 24, 2021
Remember Who May Have Wanted to License Pegasus?
August 20, 2021
Cyber intelligence firm NSO, makers of Pegasus spyware, knows no bounds when it comes to enabling government clients to spy on citizens. Apparently, however, it draws the line at helping Facebook spy on its users. At his Daring Fireball blog, computer scientist John Gruber reports that “Facebook Wanted NSO Spyware to Monitor iOS Users.” We learn that NSO CEO Shalev Hulio has made a legal declaration stating he was approached in 2017 by Facebook reps looking to purchase certain Pegasus capabilities. Gruber quotes Motherboard’s Joseph Cox, who wrote:
“At the time, Facebook was in the early stages of deploying a VPN product called Onavo Protect, which, unbeknownst to some users, analyzed the web traffic of users who downloaded it to see what other apps they were using. According to the court documents, it seems the Facebook representatives were not interested in buying parts of Pegasus as a hacking tool to remotely break into phones, but more as a way to more effectively monitor phones of users who had already installed Onavo. ‘The Facebook representatives stated that Facebook was concerned that its method for gathering user data through Onavo Protect was less effective on Apple devices than on Android devices,’ the court filing reads. ‘The Facebook representatives also stated that Facebook wanted to use purported capabilities of Pegasus to monitor users on Apple devices and were willing to pay for the ability to monitor Onavo Protect users.’”
We are glad to learn NSO has boundaries of any sort. And score one for Apple security. As for Facebook, Gruber asserts this news supports his oft-stated assertion that Facebook is a criminal operation. He bluntly concludes:
“Facebook’s stated intention for this software was to use it for mass surveillance of its own honest users. That is profoundly [messed] up — sociopathic.”
Perhaps.
Cynthia Murrell, August 20, 2021
Silicon Valley Neologisms: The Palantir Edition
August 19, 2021
Do you remember the Zuckerland metaverse? (Yes, I know he borrowed the word, but when you are president of a digital country, does anyone dare challenge Zuck the First, Le Roi Numérique?)
Palantir Technologies (the Seeing Stone outfit with the warm up jacket fashion bug) introduced a tasty bit of jargon-market speak in its Q2 2021 earnings call:
Palantir’s meta-constellation software harnesses the power of growing satellite constellations, deploying AI into space to provide insights to decision-makers here on Earth. Our meta-constellation integrates with existing satellites, optimizing hundreds of orbital sensors and AI models and allowing users to ask time-sensitive questions across the entire planet. Important questions like, where are the indicators of wildfires or how are climate changes affecting crop productivity? And when and where are naval fleets conducting operations? Meta-constellation pushes Palantir’s Edge AI technology to a new frontier.
I think meta-constellation is a positive contribution to the American Silicon Valley-Denver lingo.
One of the interesting factoids in the write up is that the average customer “invests” lots of money in the firm’s software and services. The average customer yields $7.9 million. Let’s assume there was a touch of spreadsheet fever whipping the accountants. Chop that down to a couple of million, and the cowboy outfit is doing okay. Now the job is to corral those customers so there is sustainable, recurring revenue and generous profits going forward like little doggies heading to the meat processing facility.
Also, deploying the Palantirians’ system is as easy as cooking some of Cowboy Ken’s beans in an iron pot over a wood fire. The transcript faithfully reports:
In just two days, we were able to deploy an entire solution for this customer, leveraging our out-of-the-box functionality built in foundry, a time line previously unthinkable in the eyes of the customer. And frankly, it would have been unthinkable to us even three years ago, where an equivalent project might have taken three months. This is only possible because of our product. Innovations from software-defined data integration are driving the marginal cost of data integration to 0, archetypes and our no-code technologies that are driving the marginal cost of application development to zero.
Those data cowboys are moving faster than a branded calf on a crisp April morning.
The most interesting factoid is contained in this statement:
Given our strong cash flow position, we repaid our outstanding $200 million term loan facility and are currently debt-free. After paying off the debt, we ended the quarter with $2.3 billion in cash and cash equivalents.
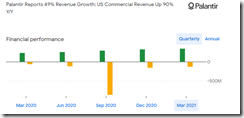
I don’t want to raise a touchy subject, but this chart caught my attention:
That yellow line means that the company is losing money if I am interpreting the Google Finance graph correctly.
It may be helpful to consider that Palantir has never turned a profit. Let’s hope those Colorado transplants can covert expensive cows into hard cash after more than a decade grazing on the range. No digital cows, please. Leave those for the Facebook metaverse which is less than a meta-constellation in JRR Tolkien fantasy space.
Stephen E Arnold, August 19, 2021