How about Those Cyber Security Awards? Great in the Wake of SolarWinds and the MSFT Exchange Issues
March 26, 2021
The Cyber Defense Awards, hosted by Cyber Defense Magazine, has released its list of “InfoSec Awards for 2020-Winners.” The introduction reads:
“These InfoSec Awards are in their 8th year and specifically focused on finding innovative infosec players who have a presence in the United States and other countries. With over 3,200 cybersecurity companies worldwide, only a small number – roughly 10% – are highlighted as InfoSec Awards 2020 winners, based upon independent judging and analysis. This year, we’ve continued to expand our coverage of some of our winning Women in Cybersecurity who will be rolled into our annual update, highlighting some of the innovative women helping taking cybersecurity to new heights.”
It is nice that the awards are recognizing the contributions of women in the male dominated field, and the post presents us with an impressive list of companies. However, we note one name seems to be missing—FireEye, the firm whose smart human analyst (non AI infused) actually caught the widespread SolarWinds’ attack. After that debacle, the effects of which the cyber-security community is still unraveling, we wonder whether these awards are justified. Perhaps they should have taken the year off.
Be that as it may, those interested in the cyber security field may want to check out the full list. It and a description of the judges’ approach can be viewed at the link above.
Now the $64 dollar question: How many of these “winners” detected the SolarWinds and Exchange breaches? Choose one: [a] None, [b] Zip, [c] Zero, [d] Nada.
Cynthia Murrell, March 26, 2021
Microsoft: Losing an Appetite for Chinese Take Out?
March 16, 2021
I read “Microsoft Claims They Are under Attack by China.” Last month, Microsoft was under attack by Russia. In this most recent round of finger pointing, the Giant Freakin Robot states:
Microsoft says this hack actually began months ago, maybe as early as January with the hackers masking their efforts along the way and prying deeper into the base systems that stand up these email servers. Once it was noticed in early March, the company worked on a fix.
The bad actors have done significant harm. Attributing the attack to a nation state suggests that companies based in the US and deploying software and services worldwide are targets of value.
Several questions come to mind:
- With an attack which began months ago, why weren’t existing cyber security systems able to discern the breach and issue alerts?
- How long is “months ago”? What if the Exchange breaches occurred three, six, a year or more before being detected? Microsoft “defender” should have defended, but what about third party cyber security systems?
- Will the patches remediate the problem? Microsoft issued a Windows 10 update which caused some print functions to fail? Are Microsoft’s “fixes” introducing new vulnerabilities?
Net net: The bad actors (whether kids in McDonalds) or trained cyber warriors in bunkers may not be the actual problem.
What’s the problem?
Microsoft’s core business processes maybe?
The move to the cloud, background updates, flawed quality checks, and an eagerness to blame others could be contributing factors to the Redmond giant’s spate of woes.
What countries will be blamed for attacking Microsoft? I think Liechtenstein looks suspicious, don’t you?
Scrap the Chinese lunch order for today too.
Stephen E Arnold, March 16, 2021
Quantum Computing: The Solution to SolarWinds and Microsoft Security Gaps
March 12, 2021
I am an optimist. I have been waking up with the idea that life is good and my work might make the world a slightly better place. However, I don’t put much trust in unicorns (nifty horses with a long pointy horn or the Silicon Valley type), fairies, or magical mermaids. When new technology comes along, I view the explanations of the technology’s wonders with skepticism. Mobile phones are interesting, but the phone has been around for a while. Shrinking chips make it possible to convert the “phone” into a general purpose thumbtyping machine. Nifty, but still a phone on steroids.
I thought about the human tendency to grasp for silver bullets. This characteristic runs through Jacques Ellul’s book The Technology Bluff. Its decades-old explanations and analyses are either unknown or ignored by many informed individuals. My hunch is that the Murdoch-owned Wall Street Journal assumes that its writers are responsible for understanding certain topics.
I read “Effective Cybersecurity Needs Quantum Computing.” Perhaps I should send a copy of Dr. Ellul’s book? But why? It’s not like the hippy dippy books included in the Murdoch book reviews. Dr. Ellul likes interesting words; for example, Mancipium. Does Mr. Murdoch’s oldest son know the meaning of the word? He should he lives in a mancipum-infused environment.
The essay asserts that a new and essentially unworkable technology will deal with the current cybersecurity challenges. How many years will be required to covert baby step lab experiments into a scalable solution to the business methods employed at outfits like SolarWinds and Microsoft? One, maybe five, or a more realistic 25 years?
The problems caused by flawed, short cut riddled, and uninformed approaches to coding, building, deploying, and updating enterprise software are here-and-now puzzles. For a point of reference, the White House sounded an alarm that a really big problem exists and poses threats today.
Sure, let’s kick back and wait for the entities of nifty technology to deliver solutions. IBM, Google, and other firms are beavering away on the unicornesque quantum computing. That’s fine, but to covert expensive, complex research and development projects into a solution for the vulnerability of that email you sent a few minutes ago is just off the wall. Sure, there may be a tooth fairy or a wizard with a magic wand, but that’s not going to be the fix quantum computing allegedly will deliver.
The WSJ essay states:
The extraordinary sensitivity of qubits reveals interference instantly and unfailingly. They would alert us when hackers read, copy or corrupt transmitted files.
Sure, if someone pays attention. I want to point out that exactly zero of the cybersecurity systems monitoring the SolarWinds’ misstep sounded an alarm. Hooking these systems into a quantum system will result in what, another two to five years of development. Walking by today’s quantum computers and waving an iPhone close to a component can create some excitement. Why? Yep, sensitivity. But why worry about trivial details.
The Murdocher does admit that quantum computers are years away, there is zero value in kicking today’s security disasters down the road like a discard can of Pabst Blue Ribbon beer. Funding is fine. Conflating the current radiation poisoning of digital systems with quantum computing is like waiting for an Uber or Lyft driver to come by in a chariot pulled by a unicorn.
Stephen E Arnold, March 12, 2021
Palantir and Anduril: Best Buds for Sure
March 12, 2021
I read “Anduril Industries Joins Palantir Technologies’ TITAN Industry Team.” In the good old days I would have been zipping from conference to conference outputting my ideas. Now I sit in rural Kentucky and fire blog posts into the datasphere.
This post calls attention to an explicit tie up between two Peter Thiel-associated entities: Palantir Technologies and Anduril. The latter is an interesting company with some nifty smart technology, including a drone which has the cheerful name “Anvil.”
For details about the new US Army project and the relationship between these two companies, the blog post was online as of March 8, 2021. (Some information may be removed, and I can’t do much about what other outfits do.)
Information about Anduril is available at their Web site. Palantir is everywhere and famous in the intelware business and among some legal eagles. No, I don’t have a Lord of the Rings fetish, but some forever young folks do.
Stephen E Arnold, March 12, 2021
The Microsoft Supply Chain Works Even Better Going Backwards
March 4, 2021
Do you remember the character KIR-mit. He once allegedly said:
Yeah, well, I’ve got a dream too, but it’s about singing and dancing and making people happy. That’s the kind of dream that gets better the more people you share it with.
I am not talking about Jim Henson’s memorable character. That frog spelled its name Kermit. This is KIR-mit, an evil doppelgänger from another universe called Redmonium.

This KIR-mit is described in “Microsoft Is Using Known Issue Rollback (KIR) to Fix Problems Caused by Windows 10 Updates.” I learned that KIR
enables Microsoft to rollback changes introduced by problematic patches rolled out through Windows Update. KIR only applies to non-security updates.
Does the method expand the attack service for bad actors? Will weird calls to senior citizens increase with offers to assist with KIR-mit modifications? Will questionable types provide links to download KIRs which are malware? Yes, yes, and yes.
The article points out:
Known Issue Rollback is an important Windows servicing improvement to support non-security bug fixes, enabling us to quickly revert a single, targeted fix to a previously released behavior if a critical regression is discovered.
KIR is something users have said they wanted. Plus Microsoft has had this capability for a long time. I recall reading that Microsoft had a method for verifying the “digital birth certificate” of software in order to identify and deal with the SolarWinds-type of supply chain hack. I point this out in my upcoming lecture for a law enforcement entity. Will my audience find the statement and link interesting? I have a hunch the cyber officers will perk up their ears. Even the JEDI fans will catch my drift.
Just regular users may become woozy from too much KIR in the system. Plus, enterprise users will be “in charge of things.” Wonderful. Users at home are one class of customers; enterprise users are another. In between, attack surface the size of the moon.
Several questions:
- Why not improve the pre release quality checks?
- Why not adopt the type of practices spelled out by In Toto and other business method purveyors?
- Why not knock off the crazy featuritis and deliver stable software in a way that does not obfuscate, mask, and disguise what’s going on?
And the answers to these questions is, “The cloud is more secure.”
Got it. By the way a “kir” is a French cocktail. Some Microsoft customers may need a couple of these to celebrate Microsoft’s continuous improvement of its outstanding processes.

As KIR-mit said, “It’s about making people happy.” That includes bad actors, malefactors, enemies of the US, criminals, and Microsoft professionals like Eric Vernon and Vatsan Madhava, the lucky explainers of KIR-mit’s latest adventure.
Stephen E Arnold, March 4, 2021
DarkCyber for February 9, 2021, Now Available
February 9, 2021
DarkCyber is a twice-a-month video news program about the Dark Web, cyber crime, and lesser known online services. The program is produced by Stephen E Arnold. You can view the program on the Beyond Search blog or on YouTube at this link.
This week’s program features a discussion of Microsoft’s explanation of the SolarWinds’ misstep. The online explanation is a combination of forensic information with an old-fashioned, almost Balmer-esque marketing pitch. Plus, DarkCyber responds to a viewer who wanted more information about locating bad actor hackers promoting their criminal capabilities on the Dark Web. The program highlights two Dark Web services and provides information to two online resources which offer additional information. Three other stories round out the February 9, 2021, program. Allegedly some of the software stolen in the SolarWinds’ misstep (a data breach which compromised more than 18,000 companies and government organizations) is available for sale. Information about the cost of the software and how to buy are provided. Next you learn about the app tracking technology which is creating friction between Apple and Facebook. Who benefits from tracking users’ actions hundreds of times each day? DarkCyber answers this question. The final story is another signature drone news item. If you think that one drone poses a challenge, consider the difficulty of dealing with thousands of miniature weaponized drones converging on a unit or disrupting warfighting tactics under live fire.
Kenny Toth, February 9, 2021
Enterprise Search: Blasting Away at Feet, Walls, and Partners
January 18, 2021
I read a very good write up called “Is Elasticsearch No Longer Open Source Software?” The write up contains a helpful summary of the history of Elastic and its Lucene-based search solution. Plus the inhospitable territory of open source licensing gets a review as well. To boil down the write up does not do it justice, so navigate to the source document and read it first hand.
I noted a couple of passages which I found suggestive.
First, here’s a comment which strikes me as relevant to the Bezos bulldozer’s approach to low or no cost, high utility software:
if you want to provide Elasticsearch on a SaaS basis, you have to release any code that you use to do this: in Amazon’s case this could mean all the management layers that go into providing Elasticsearch on Amazon Web Services (AWS), so I doubt this is going to happen.
My view is that Elastic and its management team want to put some sand in the bulldozer’s diesel fuel. The question is, “WWAD” or “What will Amazon do?” Some of the options available to Amazon are likely to be interesting. The specific series of actions Amazon pursues will be particularly thrilling.
Second, another passage I circled was:
Smaller SaaS providers without Amazon’s resources will have to decide whether to do a deal with Elastic or Amazon to continue to offer a hosted Elasticsearch.
Based on my limited understanding of the legal hoo-hah with open source legal nuances, I think a customer will have to make a choice. Ride the bulldozer or go with the Son of Compass search. (Yep, that would be Elastic.)
For me, my meanderings through open source and enterprise search sparked these thoughts:
- In a competitive arena, open source will become closed. Too much money is at stake for the “leaders”
- Open source provides a low cost, low friction way to add functionality or enable an open source “play.” Once up and running, the company using open source wants to make sure the costs of R&D, bug fixes, and other enhancements are “free”; that is, not an expense to the company using open source software.
- Forks or code released to open source are competitive moves motivated by financial and marketing considerations.
Open source, open code, open anything: Sounds too good to be true. For some situations, enterprise search’s DNA will surface and the costs can be tricky enough to make an accountant experience heart burn. And the lawyers? Those folks send invoices. The users? Search is a utility. The companies appropriating and making their solution proprietary? Mostly happy campers. And the open source “developers”? Yikes.
Stephen E Arnold, January 18, 2021
DarkCyber for January 12, 2021, Now Available
January 12, 2021
DarkCyber is a twice-a-month video news program about online, the Dark Web, and cyber crime. You can view the video on Beyond Search or at this YouTube link.
The program for January 12, 2021, includes a featured interview with Mark Massop, DataWalk’s vice president. DataWalk develops investigative software which leapfrogs such solutions as IBM’s i2 Analyst Notebook and Palantir Gotham. In the interview, Mr. Massop explains how DataWalk delivers analytic reports with two or three mouse clicks, federates or brings together information from multiple sources, and slashes training time from months to several days.
Other stories include DarkCyber’s report about the trickles of information about the SolarWinds’ “misstep.” US Federal agencies, large companies, and a wide range of other entities were compromised. DarkCyber points out that Microsoft’s revelation that bad actors were able to view the company’s source code underscores the ineffectiveness of existing cyber security solutions.
DarkCyber highlights remarkable advances in smart software’s ability to create highly accurate images from poor imagery. The focus of DarkCyber’s report is not on what AI can do to create faked images. DarkCyber provides information about how and where to determine if a fake image is indeed “real.”
The final story makes clear that flying drones can be an expensive hobby. One audacious drone pilot flew in restricted air zones in Philadelphia and posted the exploits on a social media platform. And the cost of this illegal activity. Not too much. Just $182,000. The good news is that the individual appears to have avoided one of the comfortable prisons available to authorities.
One quick point: DarkCyber accepts zero advertising and no sponsored content. Some have tried, but begging for dollars and getting involved in the questionable business of sponsored content is not for the DarkCyber team.
Finally, this program begins our third series of shows. We have removed DarkCyber from Vimeo because that company insisted that DarkCyber was a commercial enterprise. Stephen E Arnold retired in 2017, and he is now 77 years old and not too keen to rejoin the GenX and Millennials in endless Zoom meetings and what he calls “blatant MBA craziness.” (At least that’s what he told me.)
Kenny Toth, January 12, 2021
Factoids from Best Paper Awards in Computer Science
January 6, 2021
I noted “Best Paper Awards in Computer Science Since 1996.” The year caught my attention because that was the point in time at which software stagnation gained traction. See “The Great Software Stagnation” for the argument.
The Best Papers tally represents awards issued to the “best papers”. Hats off to the compiler Jeff Huang and his sources and helpers.
I zipped through the listings which contained dozens upon dozens of papers I knew absolutely zero about. I will probably be pushing up daisies before I work through these write ups.
I pulled out several observations which answered questions of interest to me.
First, the data illustrate the long tail thing. Stated another way, the data reveal that if an expert wants to win a prestigious award, it matters which institution issues one’s paycheck:
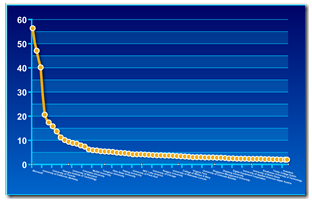
Second, what are the most prestigious “names” to which one should apply for employment in computer science? Here’s the list of the top 25. The others are interesting but not the Broadway stars of the digital world:
| 1 | Microsoft | 56.4 |
| 2 | University of Washington | 50.5 |
| 3 | Carnegie Mellon University | 47.1 |
| 4 | Stanford University | 43.3 |
| 5 | Massachusetts Institute of Technology | 40.2 |
| 6 | University of California, Berkeley | 29.2 |
| 7 | University of Michigan | 20.6 |
| 8 | University of Illinois at Urbana–Champaign | 18.5 |
| 9 | Cornell University | 17.4 |
| 10 | 16.8 | |
| 11 | University of Toronto | 15.8 |
| 12 | University of Texas at Austin | 14.5 |
| 13 | IBM | 13.7 |
| 14 | University of British Columbia | 12.4 |
| 15 | University of Massachusetts Amherst | 11.2 |
| 16 | Georgia Institute of Technology | 10.3 |
| 17 | École Polytechnique Fédérale de Lausanne | 10.1 |
| 18 | University of Oxford | 9.6 |
| 19 | University of California, Irvine | 9.4 |
| 20 | Princeton University | 9.1 |
| 21 | University of Maryland | 8.9 |
| 22 | University of California, San Diego | 8.7 |
| 23 | University of Cambridge | 8.6 |
| 24 | University of Wisconsin–Madison | 8 |
| 25 | Yahoo | 7.9 |
Note that Microsoft, the once proud Death Star of the North, is number one. For comparison, the Google is number 10. But the delta in average “bests” is an intriguing 39.6 papers. The ever innovative IBM is number 13, and the estimable Yahoo Oath Verizon confection is number 25.
I did not spot a Chinese University. A quick scan of the authors reveals that quite a few Chinese wizards labor in the research vineyards at these research-oriented institutions. Short of manual counting and analysis of names, I decided to to calculate authors by nationality. I think that’s a good task for you, gentle reader.
What about search as a research topic in this pool? I used a couple of online text analysis tools like Writewords, a tool on my system, and the Madeintext service. The counts varied slightly, which is standard operating procedure for counting tools like these. The 10 most frequently used words in the titles of the award winning papers are:
| data 63 times |
| based 56 times |
| learning 53 times |
| using 49 times |
| design 45 times |
| analysis 38 times |
| software 36 times |
| time 36 times |
| search 35 times |
| Web 30 times |
The surprise is that “search” was, based on my analysis of the counts I used, was the ninth most popular word in the papers’ titles. Who knew? Almost as surprising was “social” ranking a miserable 46th. Search, it seems, remains an area of interest. Now if that interest can be transformed into sustainable revenue and sufficient profit to fund research, bug fixes, and enhancements — life would be better in my opinion.
Stephen E Arnold, January 5, 2020
Bang: Write Like a Stable Hemmingway
November 19, 2020
Do you want to write like Ernest Hemmingway? You can. Navigate to this link. Click on edit and be guided to the promised land of a famous author. You remember Mr. Hemmingway, right? The cats? The drinking? The poster with the word “Endurance” in big type. Big like a despairing fish.
I wrote this passage using the Hemingway app:
The App Is a Fish
Coders in distress. Improve communication. Land the fish. The sun blazed across my insight. The result? Blindness. Will it swim away? Will I remain in the dark like the creatures of the sea.
I clicked the button, a clean, sharp edged button. Here’s my score:
Grade 1. Smart software is fine, like a sword thrust through a bull on a hot afternoon in Madrid. Does that hurt, Jake?
Nope.
Stephen E Arnold, November 19, 2020



